Lab:Use OpenSSL to generate the Certificate Signing Request (CSR) for VMware NSX (with multiple SANs): Difference between revisions
m (Cleaning up wiki tables) |
No edit summary |
||
| Line 32: | Line 32: | ||
</div> | </div> | ||
⚠️ You can not use the NSX Manager to generate a new CSR that are usable for the signing and replacement of CA signed certificates. The NSX Manager does not provides the private key with the CSR. This private key is required later in this [https://www. | ⚠️ You can not use the NSX Manager to generate a new CSR that are usable for the signing and replacement of CA signed certificates. The NSX Manager does not provides the private key with the CSR. This private key is required later in this [https://www.iwanhoogendoorn.nl/index.php/Lab:_Replacing_the_self-signed_SSL_certificates_with_CA-signed_certificates step]. For this reason you need to use another tool to generate the CSR. I am using OpenSSL in this article. | ||
<span id="0d32cd91-e27e-4ec3-9a2c-6a046241bf44"></span> | <span id="0d32cd91-e27e-4ec3-9a2c-6a046241bf44"></span> | ||
| Line 141: | Line 141: | ||
! Algorithm | ! Algorithm | ||
|- | |- | ||
| | | Pod-120-NSXT-LM-1 | ||
| pod-120-nsxt-lm-1.sddc.lab | | pod-120-nsxt-lm-1.sddc.lab | ||
| NSX Academy | | NSX Academy | ||
| Line 152: | Line 152: | ||
| RSA | | RSA | ||
|- | |- | ||
| | | Pod-120-NSXT-LM-2 | ||
| pod-120-nsxt-lm-2.sddc.lab | | pod-120-nsxt-lm-2.sddc.lab | ||
| NSX Academy | | NSX Academy | ||
| Line 163: | Line 163: | ||
| RSA | | RSA | ||
|- | |- | ||
| | | Pod-120-NSXT-LM-3 | ||
| pod-120-nsxt-lm-3.sddc.lab | | pod-120-nsxt-lm-3.sddc.lab | ||
| NSX Academy | | NSX Academy | ||
| Line 174: | Line 174: | ||
| RSA | | RSA | ||
|- | |- | ||
| | | Pod-120-NSXT-LM | ||
| pod-120-nsxt-lm.sddc.lab | | pod-120-nsxt-lm.sddc.lab | ||
| NSX Academy | | NSX Academy | ||
| Line 185: | Line 185: | ||
| RSA | | RSA | ||
|- | |- | ||
| | | Pod-120-NSXT-LM (wildcard) | ||
| pod-120-nsxt-lm.sddc.lab | | pod-120-nsxt-lm.sddc.lab | ||
| NSX Academy | | NSX Academy | ||
| Line 204: | Line 204: | ||
| RSA | | RSA | ||
|} | |} | ||
</div> | </div> | ||
| Line 316: | Line 313: | ||
-----END PRIVATE KEY-----</pre></div></div> | -----END PRIVATE KEY-----</pre></div></div> | ||
'''Continue with >>''' [[Lab: Signing the NSX CSR with a Microsoft (root) CA Server]] | |||
[[Category:NSX]] | |||
[[Category:Networking]] | |||
[[Category:VMware]] | |||
[[Category:NSX Academy]] | |||
[ | |||
Revision as of 13:12, 21 January 2024
In this lab I am working with the following software and versions:
| Software | Version | Filename |
|---|---|---|
| VMware NSX | 4.0.0.1 | nsx-unified-appliance-4.0.0.1.0.20159694.ova |
| Windows Server | 2019 | en_windows_server_2019_updated_feb_2020_x64_dvd_de383770.iso |
| OpenSSL | 1.1.1q | Win64OpenSSL_Light-1_1_1q.exe |
| Visual C++ Redistributable Packages 2017 | 14.16.27033 | VC_redist.x64.exe |
- Create a “wildcard” CSR that can be used to sign and that can be used for all NSX Manager Nodes including the NSX Manager VIP address.
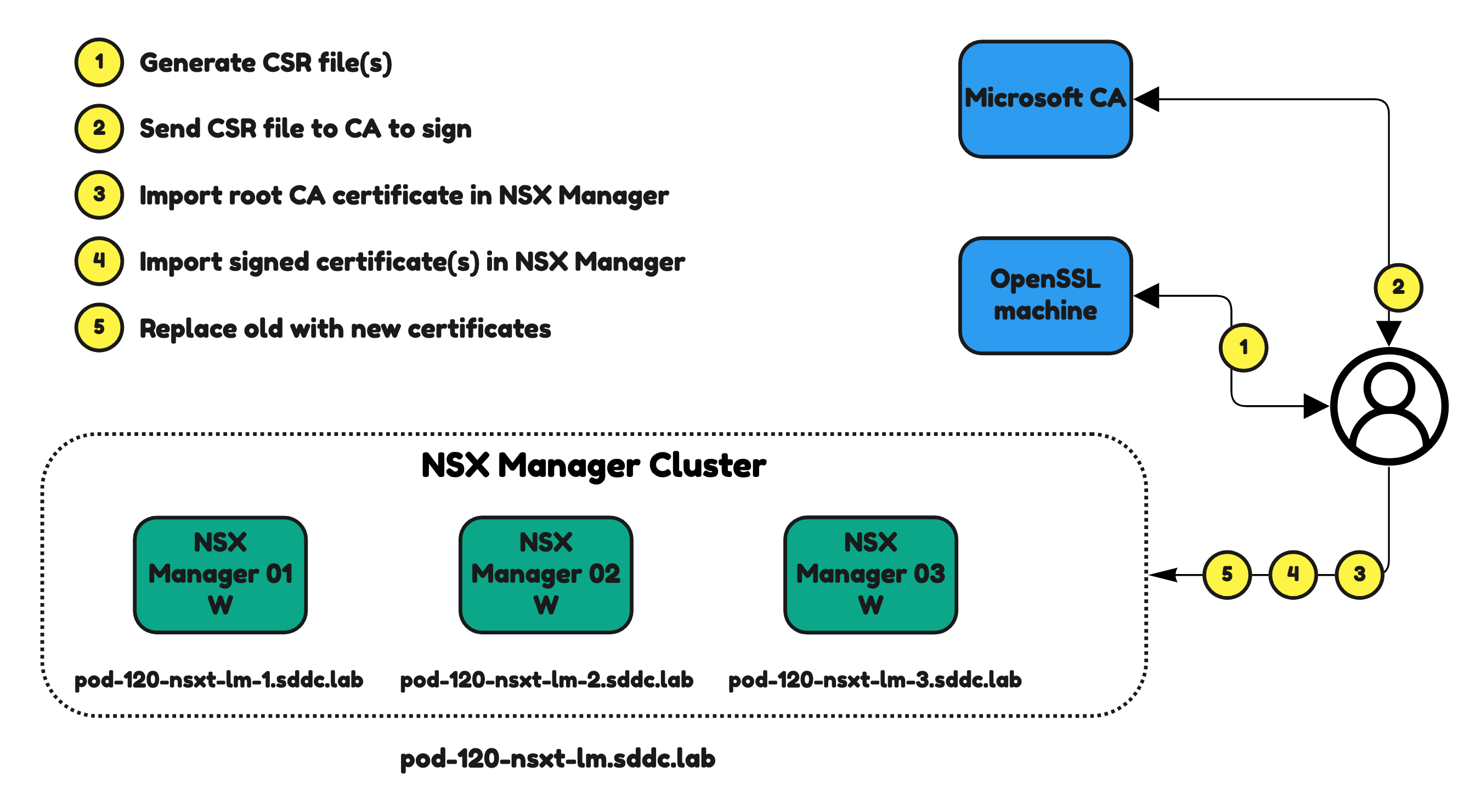
⚠️ You can not use the NSX Manager to generate a new CSR that are usable for the signing and replacement of CA signed certificates. The NSX Manager does not provides the private key with the CSR. This private key is required later in this step. For this reason you need to use another tool to generate the CSR. I am using OpenSSL in this article.
The Steps
- STEP 1: Install OpenSSL and Visual C++ Redistributable Packages
- STEP 2: Create a the certificate config file
- STEP 3: Use OpenSSL to generate the .csr and .key file
STEP 1: Install OpenSSL and Visual C++ Redistributable Packages
Visual C++ Redistributable Packages
Agree on the license terms and conditions and click “Install”.
Review the progress.
Click on “
Open SSL
Select “I accept the agreement” and click “Next”.
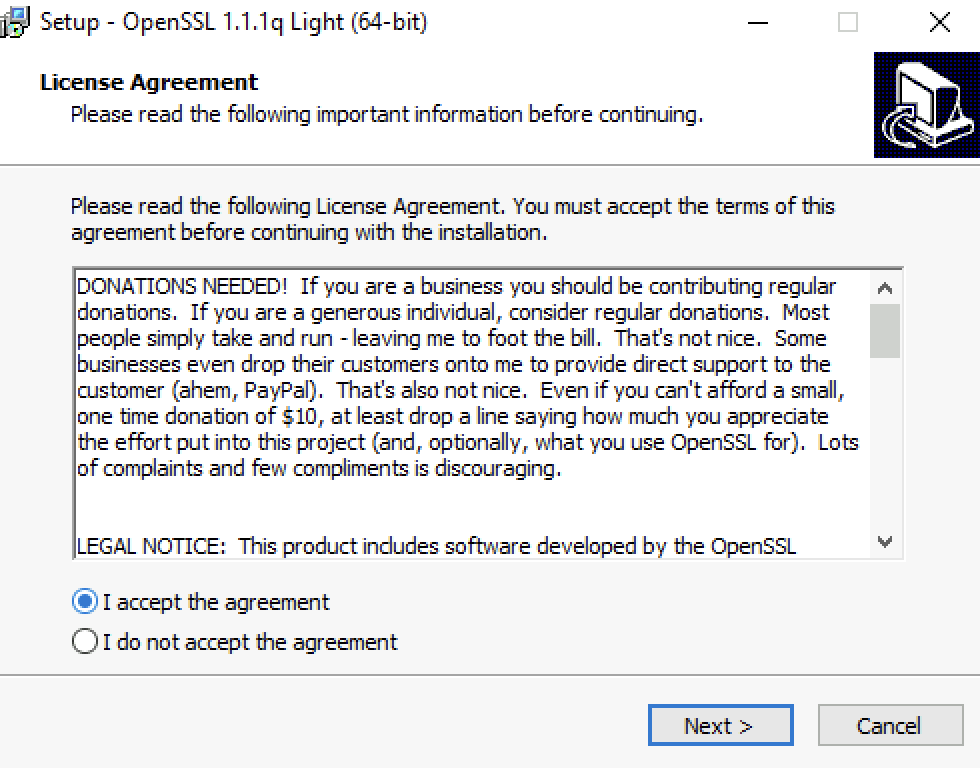
Click “Next”.
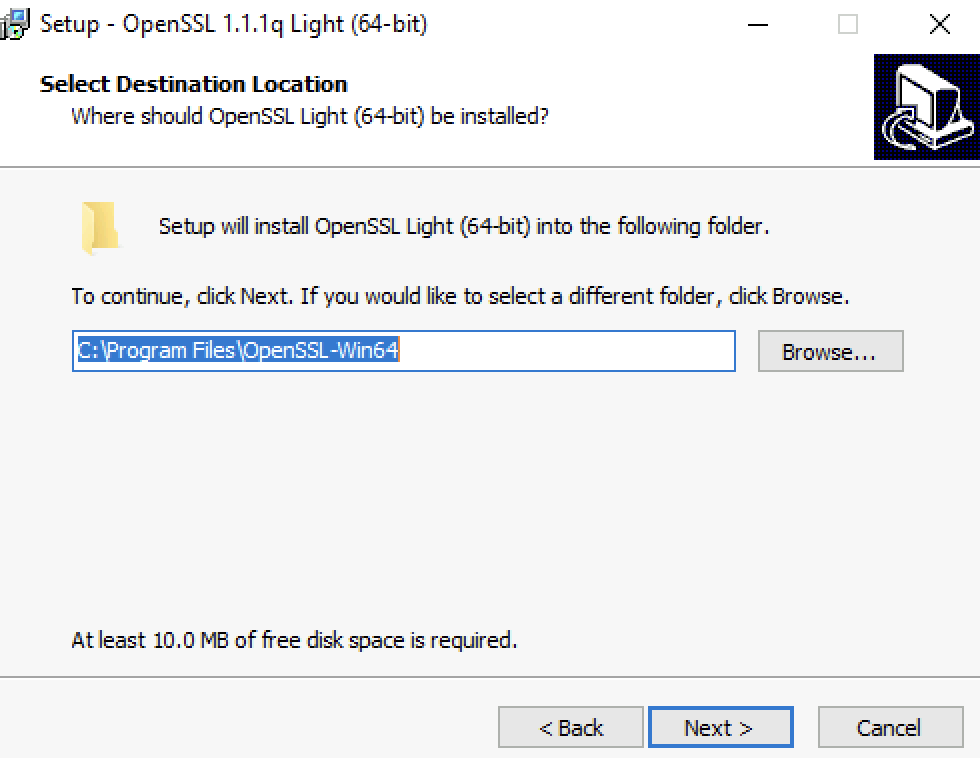
Click “Next”.
Select “The OpenSSL binaries (/bin) directory” and click “Next”.
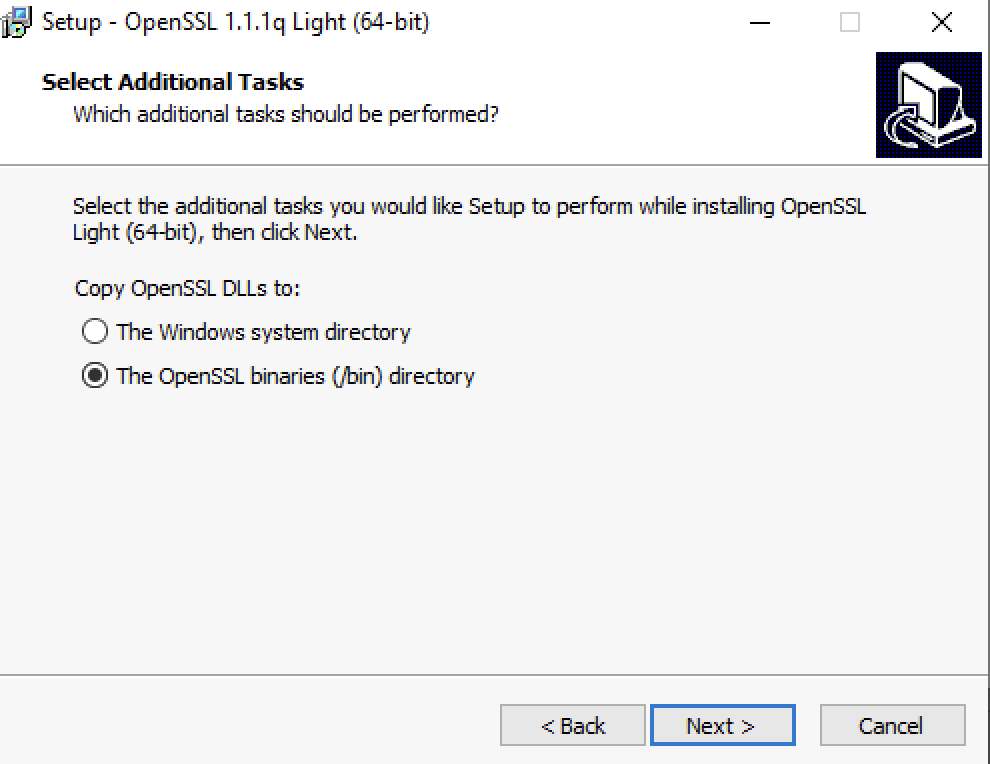
Click “Install”.
Click “Finish”.
The OpenSSL executable file is stored in this directory:
C:\Program Files\OpenSSL-Win64\bin
STEP 2: Create the certificate config file
I am using the information in the table below of the Pod-120-NSXT-LM (wildcard) as input for the config file.
| NSX Manager Node | C(ommon N(Name) | O(rganization) | O(rg) (Unit) | C(ountry) | ST(ate) | L(ocality) | (SAN) DNS Names | Key Size | Algorithm |
|---|---|---|---|---|---|---|---|---|---|
| Pod-120-NSXT-LM-1 | pod-120-nsxt-lm-1.sddc.lab | NSX Academy | Education | NL | ZH | Rotterdam | pod-120-nsxt-lm-1.sddc.lab | 2048 | RSA |
| Pod-120-NSXT-LM-2 | pod-120-nsxt-lm-2.sddc.lab | NSX Academy | Education | NL | ZH | Rotterdam | pod-120-nsxt-lm-2.sddc.lab | 2048 | RSA |
| Pod-120-NSXT-LM-3 | pod-120-nsxt-lm-3.sddc.lab | NSX Academy | Education | NL | ZH | Rotterdam | pod-120-nsxt-lm-3.sddc.lab | 2048 | RSA |
| Pod-120-NSXT-LM | pod-120-nsxt-lm.sddc.lab | NSX Academy | Education | NL | ZH | Rotterdam | pod-120-nsxt-lm.sddc.lab | 2048 | RSA |
| Pod-120-NSXT-LM (wildcard) | pod-120-nsxt-lm.sddc.lab | NSX Academy | Education | NL | ZH | Rotterdam | pod-120-nsxt-lm.sddc.lab pod-120-nsxt-lm-1.sddc.lab |
2048 | RSA |
Create a new file named nsx.cfg with the following content.
[ req ] default_bits = 2048 distinguished_name = req_distinguished_name encrypt_key = no prompt = no string_mask = nombstr req_extensions = v3_req [ v3_req ] basicConstraints = CA:TRUE keyUsage = digitalSignature, keyEncipherment, dataEncipherment extendedKeyUsage = serverAuth, clientAuth subjectAltName = DNS:pod-120-nsxt-lm, DNS:pod-120-nsxt-lm.sddc.local, DNS:pod-120-nsxt-lm-1, DNS:pod-120-nsxt-lm-1.sddc.local, DNS:pod-120-nsxt-lm-2, DNS:pod-120-nsxt-lm-2.sddc.local, DNS:pod-120-nsxt-lm-3, DNS:pod-120-nsxt-lm-3.sddc.local [ req_distinguished_name ] countryName = NL stateOrProvinceName = ZH localityName = Rotterdam 0.organizationName = NSX Academy organizationalUnitName = Education commonName = pod-120-nsxt-lm.sddc.local
Save the file in a separate /certs folder (to keep things clean).
STEP 3: Use OpenSSL to generate the .csr and .key file
Use the following command to generate the .csr and .key file.
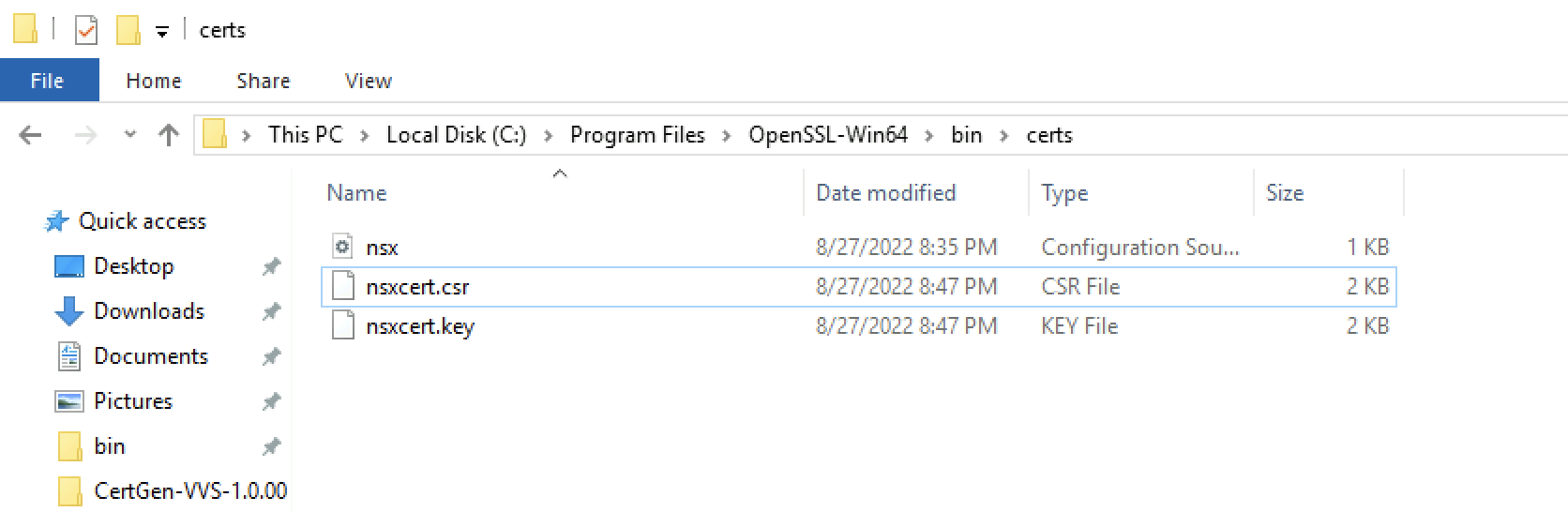
C:\Program Files\OpenSSL-Win64\bin>openssl req -out ./certs/nsxcert.csr -newkey rsa:2048 -nodes -keyout ./certs/nsxcert.key -config ./certs/nsx.cfg Generating a RSA private key ..............+++++ ...............+++++ writing new private key to './certs/nsxcert.key' ----- C:\Program Files\OpenSSL-Win64\bin>
Verify if the .csr and .key file are available.
-----BEGIN CERTIFICATE REQUEST----- MIID4zCCAssCAQAwfTELMAkGA1UEBhMCTkwxCzAJBgNVBAgTAlpIMRIwEAYDVQQH EwlSb3R0ZXJkYW0xFDASBgNVBAoTC05TWCBBY2FkZW15MRIwEAYDVQQLEwlFZHVj YXRpb24xIzAhBgNVBAMTGnBvZC0xMjAtbnN4dC1sbS5zZGRjLmxvY2FsMIIBIjAN BgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAvDqoVcDu6hxqalmsKRwNETnVcIfp rll5jo3PvkZH8c6j6yH5QldM0KuCa9N0Bo4M6VJ7hhNi7BQfWdLxLctR7PSS3eLc 3xvmL5Ed2WNtdgXqyLUA1LaIKQBT8X9FQZ3sal9OHJkDLWw7aJvnsuhNGIcykB+L C9CVd99w+wGqNXSVbk1AFOKekCZuboQ+FmPxjZTH2a/Bct9FzvQRi5M1tA+4g+yu sVoYe5zn89h2u6qtCVpHpd/0F3BmSIQsciSrtdQJ3+24RNhvETYNhyoXGfWVbObU 16nIIKd/UaNuG3JVKcyDxl7CdcxJHPjNoUU9js5Om7BN1Wqv6G1O+N6OFQIDAQAB oIIBHzCCARsGCSqGSIb3DQEJDjGCAQwwggEIMAwGA1UdEwQFMAMBAf8wCwYDVR0P BAQDAgSwMB0GA1UdJQQWMBQGCCsGAQUFBwMBBggrBgEFBQcDAjCBywYDVR0RBIHD MIHAgg9wb2QtMTIwLW5zeHQtbG2CGnBvZC0xMjAtbnN4dC1sbS5zZGRjLmxvY2Fs ghFwb2QtMTIwLW5zeHQtbG0tMYIccG9kLTEyMC1uc3h0LWxtLTEuc2RkYy5sb2Nh bIIRcG9kLTEyMC1uc3h0LWxtLTKCHHBvZC0xMjAtbnN4dC1sbS0yLnNkZGMubG9j YWyCEXBvZC0xMjAtbnN4dC1sbS0zghxwb2QtMTIwLW5zeHQtbG0tMy5zZGRjLmxv Y2FsMA0GCSqGSIb3DQEBCwUAA4IBAQA6fDcPpFJ1ozTMh0F9a7+JCen6s1n9gg3K KOs9uqCBYYsNmRLmH33dM5GifTL7GRpu5vrjyiA7pFwFU7DjWS/NK+sRZAlb5FTV wA678mLkhsXj1HW8HxB6+UuQ/2fBehZ7MkYLukFRYxcBuqupZkGrp/n7NnRj9l5p 1f2gUjfyR3Wn2J8Dp/iFDkJ8feUYIHvRKni44B6NPo6nysGXCOeFclBnQ61gja28 yhhEOzsUwXTmsBSByUzHII9VqyhTP2sdZq0nT7sLhcyy47Q2JtvQ2B7dp6M1kHG1 XvJg/OTrdJE9O+8IRQ3qDn9bSrgW6FUPUgJbL4wSO1u7h2uArcud -----END CERTIFICATE REQUEST-----
-----BEGIN PRIVATE KEY----- MIIEvQIBADANBgkqhkiG9w0BAQEFAASCBKcwggSjAgEAAoIBAQC8OqhVwO7qHGpq WawpHA0ROdVwh+muWXmOjc++RkfxzqPrIflCV0zQq4Jr03QGjgzpUnuGE2LsFB9Z 0vEty1Hs9JLd4tzfG+YvkR3ZY212BerItQDUtogpAFPxf0VBnexqX04cmQMtbDto m+ey6E0YhzKQH4sL0JV333D7Aao1dJVuTUAU4p6QJm5uhD4WY/GNlMfZr8Fy30XO 9BGLkzW0D7iD7K6xWhh7nOfz2Ha7qq0JWkel3/QXcGZIhCxyJKu11Anf7bhE2G8R Ng2HKhcZ9ZVs5tTXqcggp39Ro24bclUpzIPGXsJ1zEkc+M2hRT2Ozk6bsE3Vaq/o bU743o4VAgMBAAECggEAfwn34yi8FzXmfLDZCUXta9rku3Z/uTSaXiRIOdulYwZc i636VVQmfA/FjpDAlkv5WuBYjj03Xq6WGkHMlWPMf2jyVt9uwwZJbYE77CS3FBka RSwky2wGqeWWwj9rtsWncoOwbIy5IEcUMZ5H2u/+WLem4K7pYaf9uVINJtwQzNIg obg7EfuHzfIQAS35kiGUKzwnPCrXBUrriNYkLlfUP7EdRTm6VWecW30cn6jNFeGz pNhiQwWZQKSJZwPn7jx7iui2hvRjGF3kNRUmnBywBXmFYWnlu9o1TBAmM/FdbzYW ycbme2XMtq1ndGPyRio+CcPwV5rQy1EWI/8U0/X2AQKBgQD0b3cYbu1qNmB+Zf4l j4O6S3+xMWEAUnGtKObTpvmU3RgEHQhb+FNxLr0Rl07SX5SeowrAmMu/BkfDLMJB wxWl/XOstxVOn3nJiAQMxll/D6ZWK/xtOzlPaEzRWXJWevKajEOQIAfLcRU9kdzo UMwtyaEUPsu08moGBqctohlTsQKBgQDFIm/wrQD0ZmcT/Zu/uGZoK7eLqLZbudwF KD3IZotx8HLWZY4Q+trvU8PHMX4KC4dknwGnZWBZJVvhgIZVQc7uV3Fw1uvkx6xc LWsSM5OjL7ZMG71nn8X7w0vNwTwOx7Idyye3rR8IQ01ZmNc9FuTrWqwU1pnRek3u nCcgcQ2tpQKBgDVFkbQegNmUDkWd3ty6wV+5kpPAij5yuVmev2fDTUOXR+OlnCvH HBBfuk76JfCNaiuEpxRAeK8iJEOyHogMh0xMx4gNwrQG55j3bsKF+/1IIN1I6tO3 g4790TgTAWs9kmACT7s6b9hzxchMYNO0wDr+ZX+vC+BcsKStkIPOfyyRAoGAIpCW Ngnvh+rImg22mFgZxJwds6QiTVT6SgEzTAcG3jR9vi/SSBHj/2CdjDiWU+aPl8n1 fUdeLGNLh++EHkDKqqm0X0ef1t5Xz1W7V1apxUwhV5jpjdjK2wj0KqB+Ck1jYqvz S9ZUAZvjXRlabACupMGiOIkkMUGTlonUpnCMKG0CgYEAknpiKBTjh/agU99qRWI2 BX6ZEQnEdnX0o5Jb/Ceckjx/gC3H179jjhKztMySvc/Li12S6ViwptetLLgJTtQo HUUV7UzA29zplTJxJUHqM+REk7xQONbUMUX8XjDejfqxR+yvJ1ojIxTx6Rv9qtKF Fm6TSrqXD76hx7P+WrztcVc= -----END PRIVATE KEY-----
Continue with >> Lab: Signing the NSX CSR with a Microsoft (root) CA Server