CA signed certs with NSX-T: Difference between revisions
(Import pages from nsx.ninja) |
|||
| (4 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
This wiki article will guide you through the process of replacing your NSX-T Manager Node self-signed SSL Certificates with your own CA-signed SSL certificates. | This wiki article will guide you through the process of replacing your NSX-T Manager Node self-signed SSL Certificates with your own CA-signed SSL certificates. | ||
There are many ways to generate CSR's, set up Certificate Authorities, and sign CSR's. | There are many ways to generate CSR's, set up Certificate Authorities, and sign CSR's. | ||
| Line 5: | Line 4: | ||
I will show you a full end-to-end process from setting up your own Microsoft Windows CA Server, generating CSR's and how to use this CA Server to sign your own NSX-T SSL Certificates. | I will show you a full end-to-end process from setting up your own Microsoft Windows CA Server, generating CSR's and how to use this CA Server to sign your own NSX-T SSL Certificates. | ||
=The high | =The high–level steps= | ||
In this wiki, the high level following steps will be discussed: | In this wiki, the high level following steps will be discussed: | ||
* STEP 1: Configuring a Microsoft Server to be a Root Certificate Authority (CA) | * STEP 1: Configuring a Microsoft Server to be a Root Certificate Authority (CA) | ||
| Line 16: | Line 15: | ||
* OPTIONAL: Use one single signed certificate for all NSX-T FQDNs (including the VIP) | * OPTIONAL: Use one single signed certificate for all NSX-T FQDNs (including the VIP) | ||
=STEP 1 | =STEP 1{{fqm}} Configuring a Microsoft Server to be a Root Certificate Authority 〈CA〉= | ||
Before we can start generating CSR's and signing these, we first need to have a CA server to sign the CSRs with. | Before we can start generating CSR's and signing these, we first need to have a CA server to sign the CSRs with. | ||
In this step, I am going to show you (one of many ways) how to set up a CA server that is based on Microsoft Windows 2019 Server. | In this step, I am going to show you (one of many ways) how to set up a CA server that is based on Microsoft Windows 2019 Server. | ||
| Line 22: | Line 21: | ||
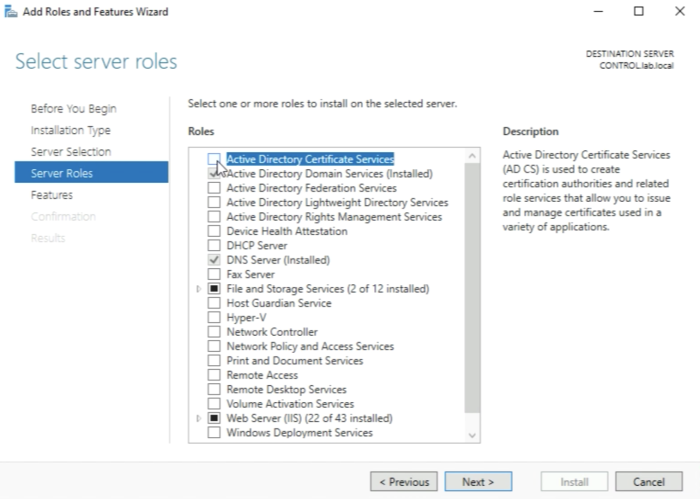
First, we click on “Add roles and features". | First, we click on “Add roles and features". | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:D3E4DC2A-3BD5-47B2-88EC-2AC0BF4ED80B.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Leave the following settings default and click next. | Leave the following settings default and click next. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:71AAE54B-6C59-4789-9E04-A3E1F365CA96.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Leave the following settings default and click next. | Leave the following settings default and click next. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:B29D2597-AAE3-4A7C-96CC-AF15C088F33D.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Leave the following settings default and click next. | Leave the following settings default and click next. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:7A84CE89-1722-4B4F-A5AA-FD84A647ECE2.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
| Line 44: | Line 43: | ||
{{note|This server needs to be configured as an Active Directory Server before you install the “Active Directory Certificate Services"}} | {{note|This server needs to be configured as an Active Directory Server before you install the “Active Directory Certificate Services"}} | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:87633787-B8AF-454E-9BBD-8B61F8CB9A97.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
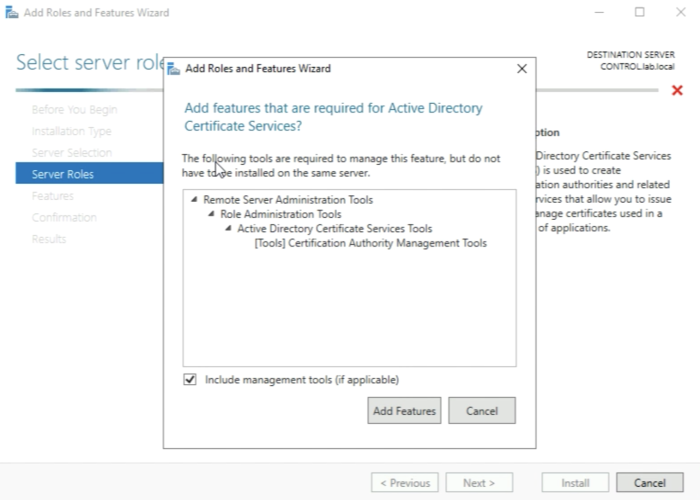
When you have selected the “Active Directory Certificate Services" checkbox the installation will ask you to add some additional tools that are required as a prerequisite. Go ahead and add these features. | When you have selected the “Active Directory Certificate Services" checkbox the installation will ask you to add some additional tools that are required as a prerequisite. Go ahead and add these features. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:209A4C55-E471-4614-AC0E-65F9384CC70A.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
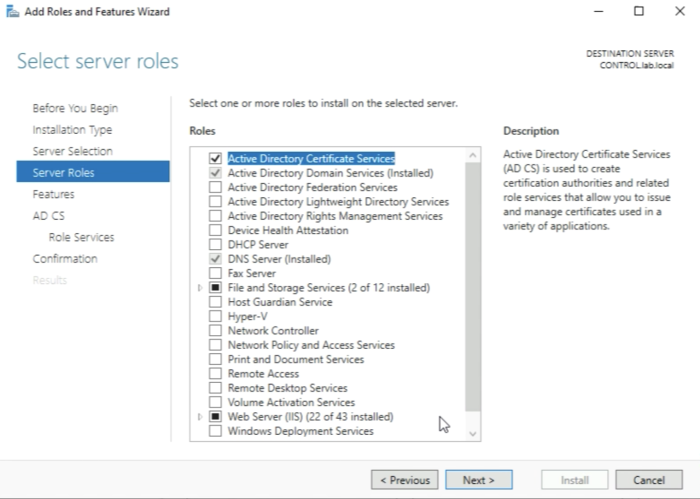
The “Active Directory Certificate Services" role is now selected and you can go ahead and click on next. | The “Active Directory Certificate Services" role is now selected and you can go ahead and click on next. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:1C7AFED3-E092-455D-B187-6E7BE5128041.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Leave the following settings default and click next. | Leave the following settings default and click next. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:0383A10F-F690-4BDB-A4A9-4873F58E8182.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Leave the following settings default and click next. | Leave the following settings default and click next. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:9978850F-6C5C-497C-932F-C4D0B60220F1.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
The “Certification Authority” Role will already be selected for you by default, but before you click on next you need to select additional role services. | The “Certification Authority” Role will already be selected for you by default, but before you click on next you need to select additional role services. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:7F317FA4-30C5-475B-A13E-374CE2CFB166.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
| Line 81: | Line 80: | ||
{{note|Make sure you have installed the Microsoft IIS web server as a prerequisite.}} | {{note|Make sure you have installed the Microsoft IIS web server as a prerequisite.}} | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:97CFF1E7-B621-42DF-8FFC-BDACE1845D88.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
| Line 87: | Line 86: | ||
Click on install. | Click on install. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:C6E1D914-9D43-44D3-825B-4C66A7F16C56.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
The installation process will start and will finish and then you will be able to close the window. | The installation process will start and will finish and then you will be able to close the window. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:D9623423-8FA6-4C00-BDE8-DB8F4B0B8C69.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
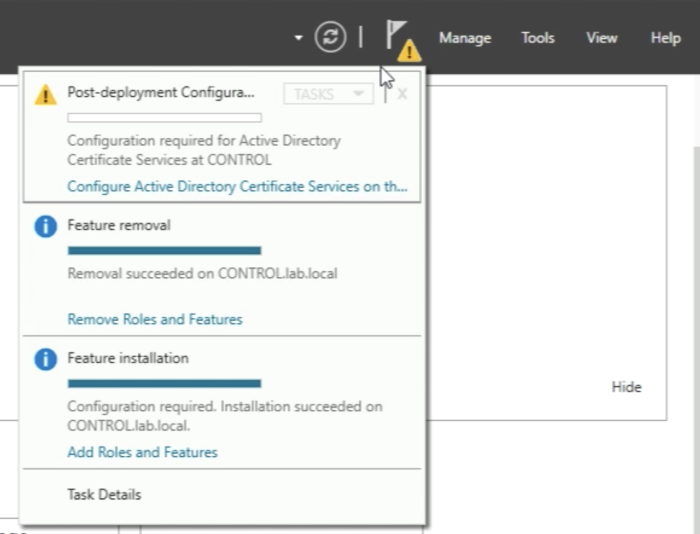
When the installation is done you need to do some additional "Post-deployment Configuration” so you need to look at the yellow exclamation mark in the upper right corner and click on “Configure Active Directory Certificate Services on this server”. | When the installation is done you need to do some additional "Post-deployment Configuration” so you need to look at the yellow exclamation mark in the upper right corner and click on “Configure Active Directory Certificate Services on this server”. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:4E1ECA24-9A1D-4203-8786-33BE2DD455E2.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Leave the following settings default and click next. | Leave the following settings default and click next. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:47CF8C3A-CFDA-40F1-AEB0-CF2E4E75A79D.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
| Line 109: | Line 108: | ||
{{note|These two Role Services needs to be configured first before others can be configured in a later stage.}} | {{note|These two Role Services needs to be configured first before others can be configured in a later stage.}} | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:D28DE286-3C71-4A04-ACB3-0D484A1DFD85.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Leave the following settings default and click next. | Leave the following settings default and click next. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:950F4A34-0DD6-47A1-A4A2-582D01053302.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Leave the following settings default and click next. | Leave the following settings default and click next. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:BDD458AD-F3F7-4745-8C07-F033D90E77CE.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
| Line 125: | Line 124: | ||
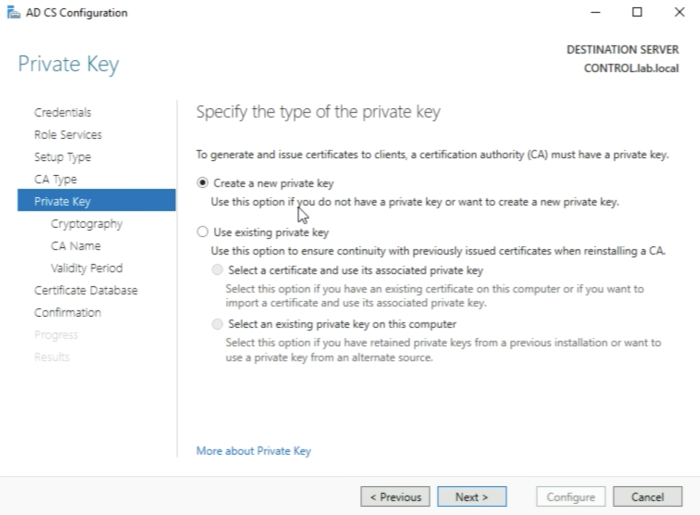
It is important that you create a private key for this new Root Certificate Authority (CA) here. | It is important that you create a private key for this new Root Certificate Authority (CA) here. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:24793705-65A1-4112-8742-BF1DDDBE6C1F.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Leave the following settings default and click next. | Leave the following settings default and click next. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:F57CDA0F-B977-4CF6-8475-D910F3C8CA39.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Leave the following settings default and click next. | Leave the following settings default and click next. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:44580C15-236E-4192-AFDD-2F4F276C0FBC.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Leave the following settings default and click next. | Leave the following settings default and click next. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:5BCB6B40-A92F-45BC-A1BD-30D4C22067A1.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Leave the following settings default and click on next. | Leave the following settings default and click on next. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:3756A9C9-12C0-4CDC-8EB1-816DFD360CA3.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Leave the following settings default and click on Configure. | Leave the following settings default and click on Configure. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:CF575954-C7E6-4D5E-811C-C47DFC157762.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
When the selected services are configured and the below messages are displaced that the Configuration is succeeded you can click on Close. | When the selected services are configured and the below messages are displaced that the Configuration is succeeded you can click on Close. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:AD8521CC-A056-45C1-A021-D477A5878871.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
| Line 161: | Line 160: | ||
SO click on “Yes” when you get the below question to configure additional role services. | SO click on “Yes” when you get the below question to configure additional role services. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:5D88374D-6E9E-43C0-B02F-855D6B2DA9FC.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Leave the following settings default and click on Next. | Leave the following settings default and click on Next. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:96A066CA-7504-4DCF-A013-F23B2A5E11ED.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
| Line 173: | Line 172: | ||
* Certificate Enrolment Policy Web Service | * Certificate Enrolment Policy Web Service | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:D6BE00B3-F5DA-49B7-B308-0709342ED2CD.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Leave the following settings default and click on Next. | Leave the following settings default and click on Next. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:059A7F36-8E4B-4E13-89CB-3664B71ED475.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Leave the following settings default and click on Next. | Leave the following settings default and click on Next. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:B83A50FB-7FF7-446C-BE86-9AD170833B9D.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
| Line 189: | Line 188: | ||
I currently have no account (or user) that is part of this group so I need to add this group to an account. | I currently have no account (or user) that is part of this group so I need to add this group to an account. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:D86C884D-491C-48CB-9D37-5747F8043FA8.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
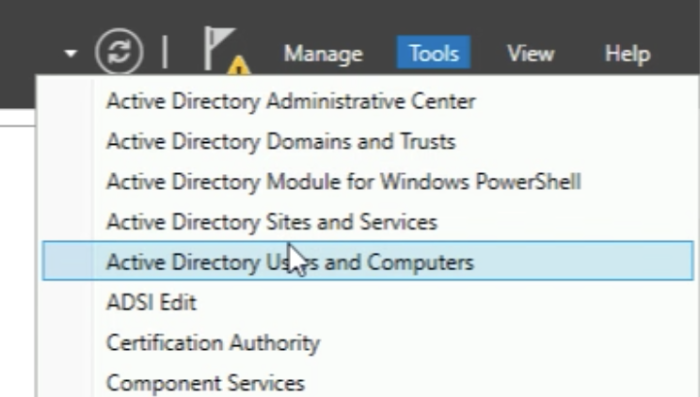
In order to assign the group to the account, You need to open the "Active Directory Users and Computers” Management Console. | In order to assign the group to the account, You need to open the "Active Directory Users and Computers” Management Console. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:31F9BA81-7348-4479-853D-FD5446AFC5E8.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
| Line 200: | Line 199: | ||
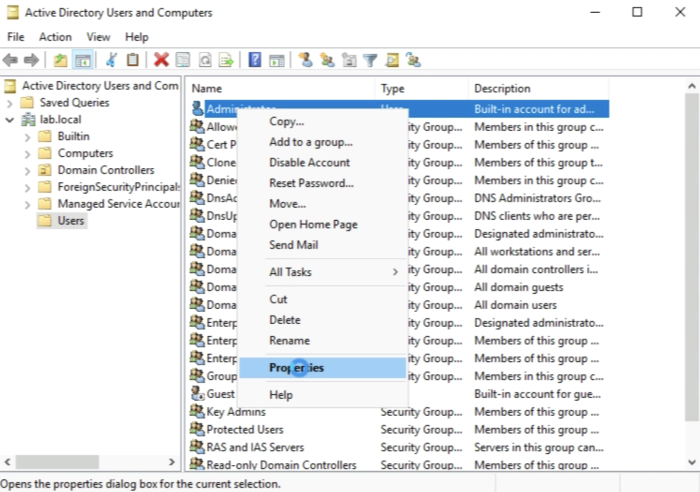
In my case, I will select the "Administrator account". | In my case, I will select the "Administrator account". | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:9963DEBC-96C0-4B2B-8AED-947D166DAF2C.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
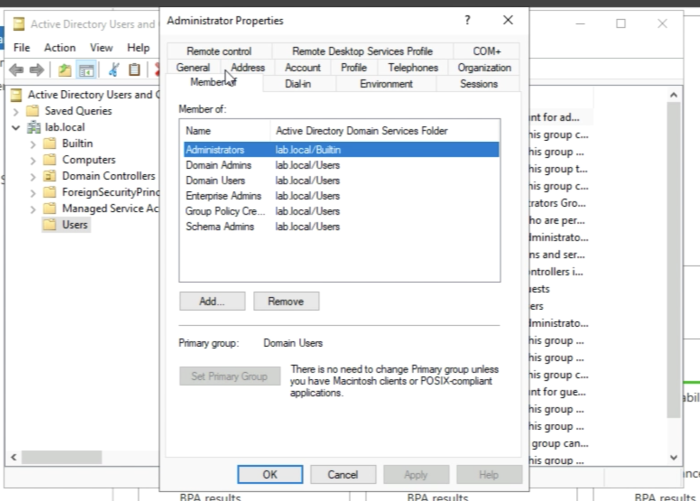
Browse to the “Member of” tab. | Browse to the “Member of” tab. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:821EAB71-5A44-436C-A35E-4F6FEA0504B6.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
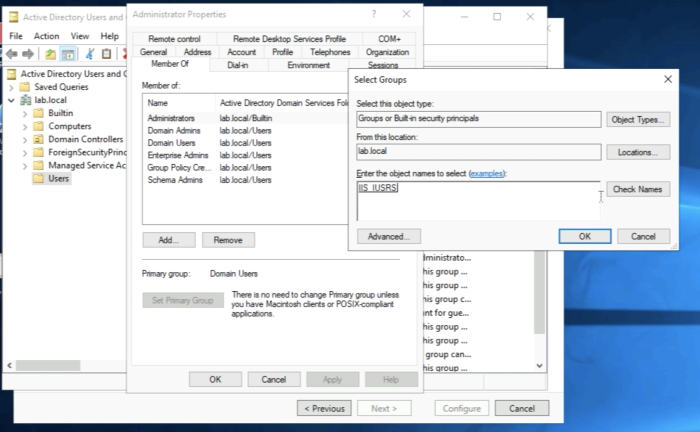
Add the IIS_IUSRS group to the "Administrator" account. | Add the IIS_IUSRS group to the "Administrator" account. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:D94A0B5F-0F4A-4157-8474-018D0A1D937B.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Make sure the IIS_IUSRS is listed in the "Member Of" list of the account. | Make sure the IIS_IUSRS is listed in the "Member Of" list of the account. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:C220AA10-4739-44A7-99EE-AEA7D5369040.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Now that the account has the proper rights we can click on select. | Now that the account has the proper rights we can click on select. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:F9F858A5-5E77-42A2-95F8-0BF723F5AAFF.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
You need to type in the credentials of the service account (in my case the Administrator account) and click on “OK”. | You need to type in the credentials of the service account (in my case the Administrator account) and click on “OK”. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:89F42B81-04FD-4916-BB3C-DE32D7C91577.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Click on “Next” when the service account is specified. | Click on “Next” when the service account is specified. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:CBDFC73B-FCE3-4298-9352-0DF1FC024EFD.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Leave the following settings default and click on Next. | Leave the following settings default and click on Next. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:BB38CCB6-60E3-4800-853B-C1CFFE720B79.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
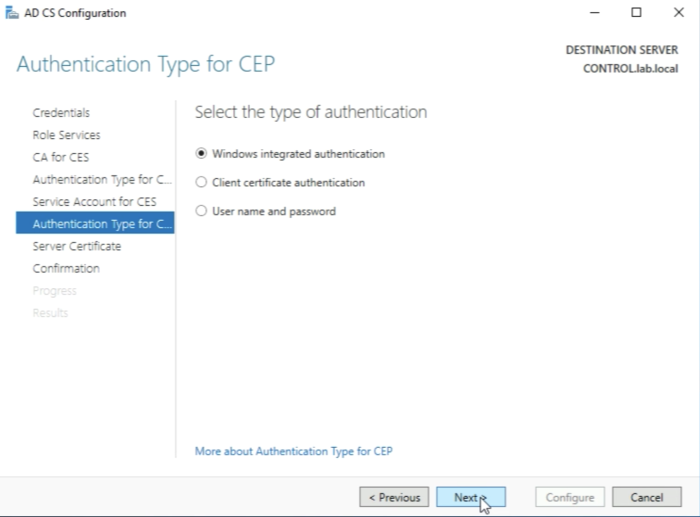
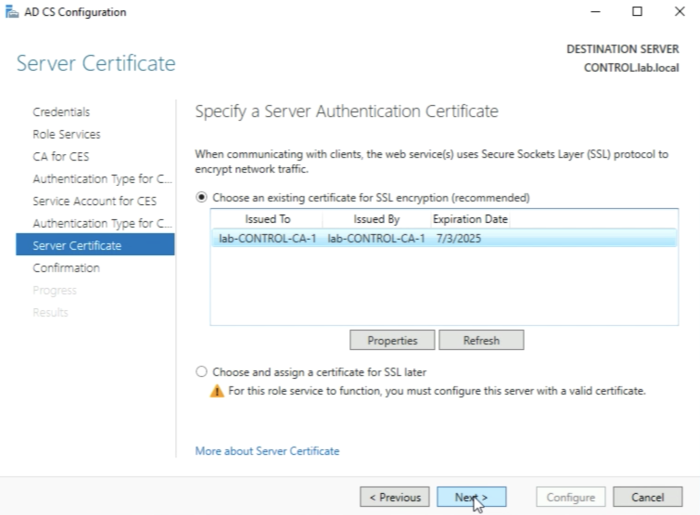
Make sure you select the “certificate" for SSL encryption first before you can click on Next. | Make sure you select the “certificate" for SSL encryption first before you can click on Next. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:9555B615-307B-4D99-A760-E4B1F1592B67.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Click on “Configure”. | Click on “Configure”. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:C1B78DCD-D59A-4599-972C-9B6A32A99F73.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
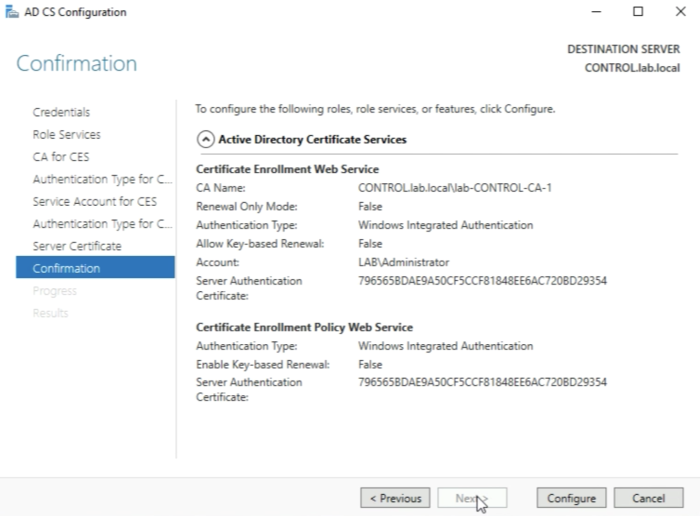
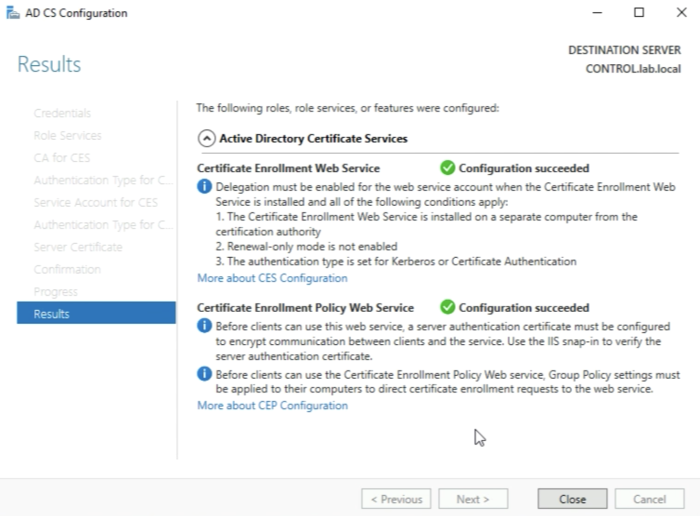
When you see the message “Configuration succeed" click on Close. | When you see the message “Configuration succeed" click on Close. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:0A449EE4-529D-4669-9D7A-66E6C5471D79.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
| Line 258: | Line 257: | ||
You can click on it. | You can click on it. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:EAA9670F-7E1B-446C-8077-90ADF2DC8D8E.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
When you click on it you can see that the AD server is online and activated. | When you click on it you can see that the AD server is online and activated. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:1442CF2C-9FF8-442B-9520-9982AC3C69D2.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
| Line 269: | Line 268: | ||
You will need this later to do some additional preparation before we can start signing the CSRs for the NSX-T Manager nodes. | You will need this later to do some additional preparation before we can start signing the CSRs for the NSX-T Manager nodes. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:76C427A3-F3EA-4C24-9675-9E62265D4C66.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
When you have opened the “Certification Authority" Management Console you will see the following screen. | When you have opened the “Certification Authority" Management Console you will see the following screen. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:6D5A755D-CD6C-4BDA-86A6-C5F61AFBF946.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
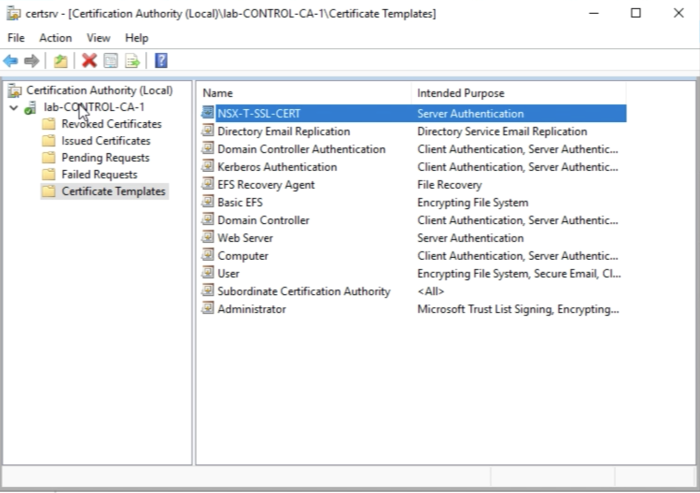
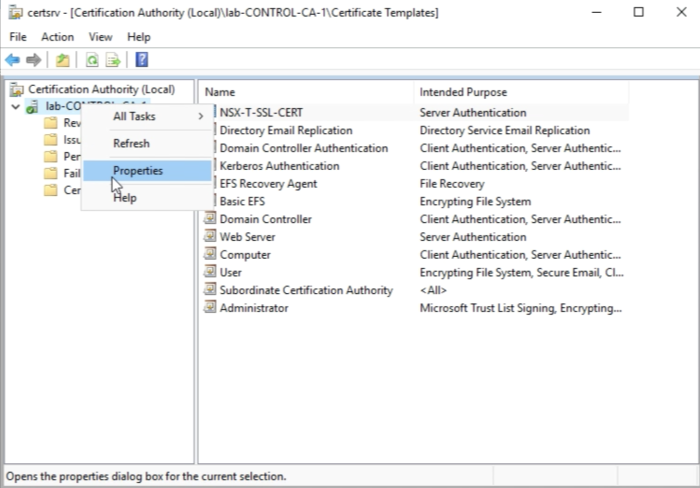
Select the name to right-click and go to the properties. | Select the name to right-click and go to the properties. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:E5A5B232-8BD5-4148-9C71-96A0155CDF58.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
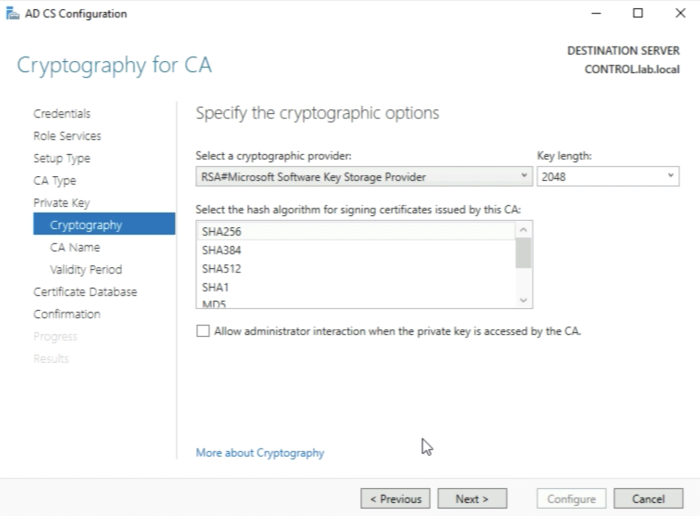
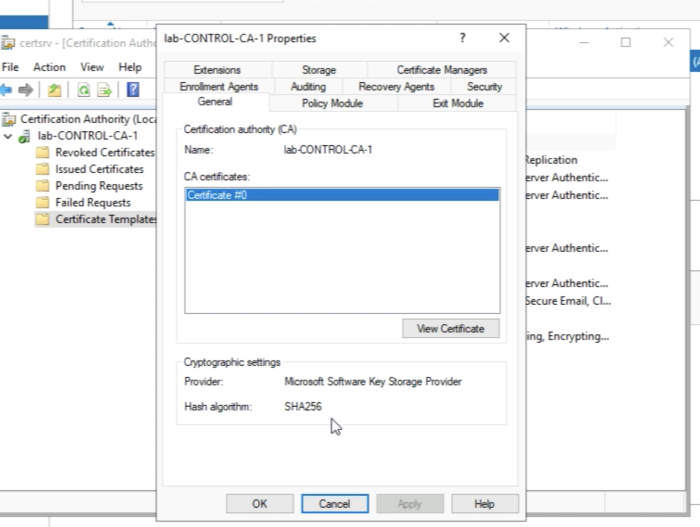
Make sure the hash algorithm is SHA256. | Make sure the hash algorithm is SHA256. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:B67F9ADD-254A-43FA-8BFE-6B658B7C6DF6.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
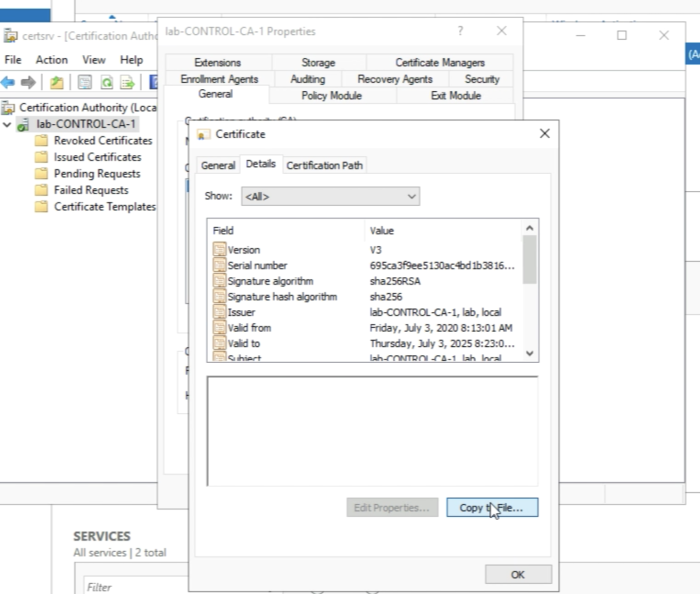
Click on “View Certificate”. | Click on “View Certificate”. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:E37DBC47-31DD-4938-8D96-2E3FB9DEA688.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
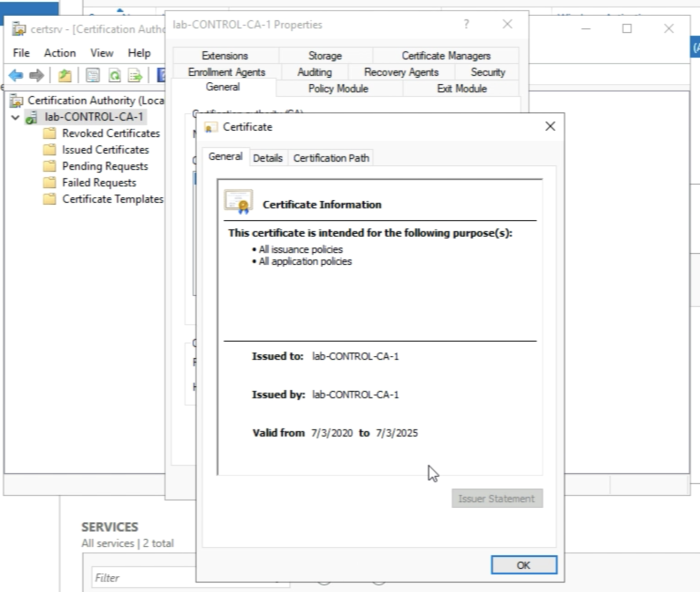
You will see the information on the Root Certificate of this CA Server. | You will see the information on the Root Certificate of this CA Server. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:222E421B-F907-4D7F-AD3A-ED86CDC27F27.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
| Line 301: | Line 300: | ||
You will need this later when you import the Root CA certificate and the signed NSX-T node certificates in NSX-T. | You will need this later when you import the Root CA certificate and the signed NSX-T node certificates in NSX-T. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:12C95C9F-4399-4B05-A6CB-D543FC2F2EA8.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Click on Next. | Click on Next. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:BD016859-B94E-4027-932E-1A6C7E24D973.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
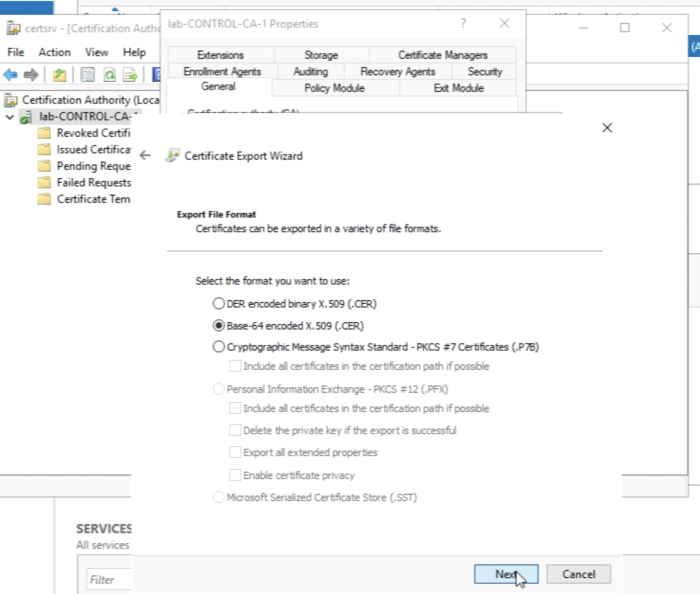
Select the “Base-64 encoded X.509 (.CER)" File Format for the export and click Next” | Select the “Base-64 encoded X.509 (.CER)" File Format for the export and click Next” | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:F3E3CC2C-4508-42A5-A05A-A65C3DBBFE71.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Specify a valid path that you want to export the files to. | Specify a valid path that you want to export the files to. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:738D4AE4-F6C0-4183-893C-AA281532C8BC.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
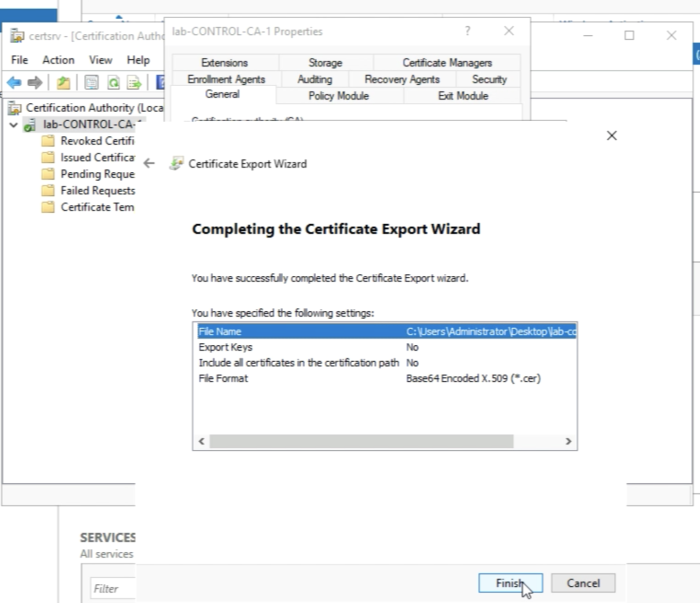
Click on Finish to complete the export of the Root Certificate files. | Click on Finish to complete the export of the Root Certificate files. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:8ACFFF04-3802-4D0A-B3D1-F4F678DFAB28.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
| Line 327: | Line 326: | ||
Click on OK to clone the message. | Click on OK to clone the message. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:80957045-FF68-4A5E-A70B-51F04C578ED1.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
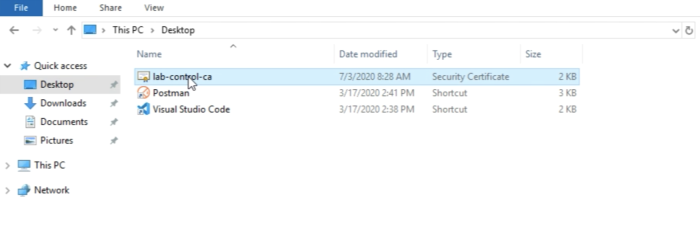
It’s always good practice to browse to the file and make sure it is really there. | It’s always good practice to browse to the file and make sure it is really there. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:89F4D1F0-50B7-4220-86CA-33B033406808.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
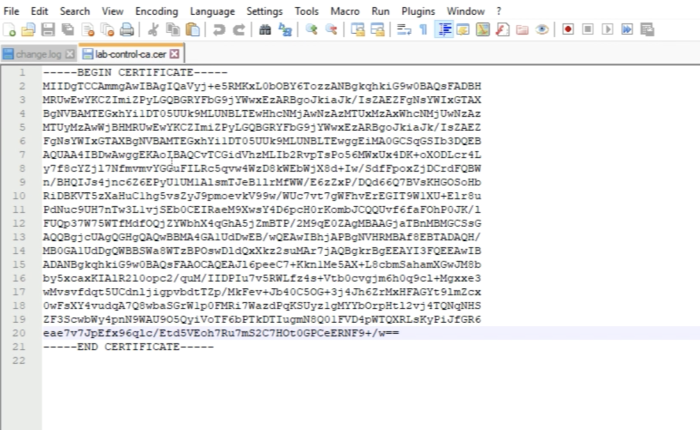
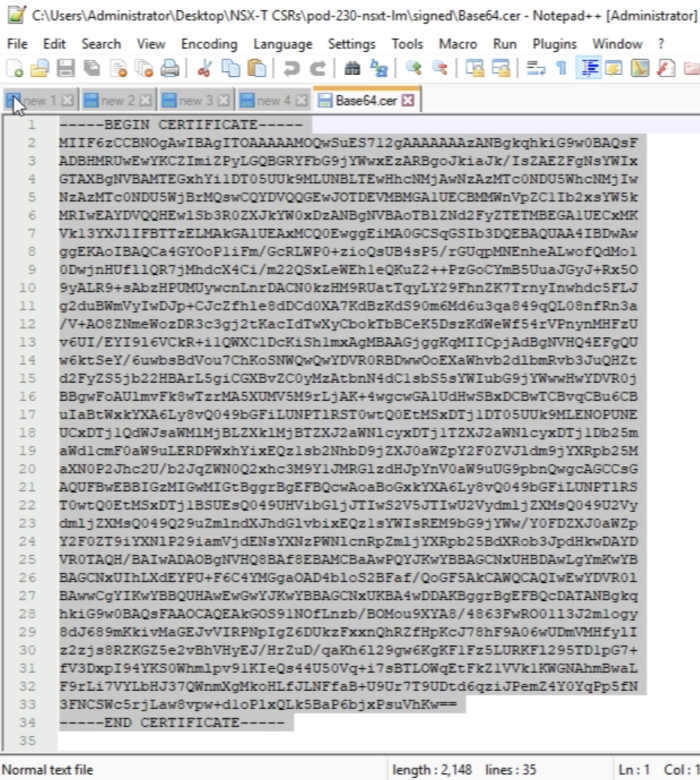
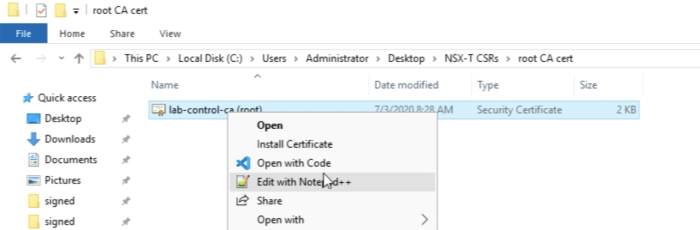
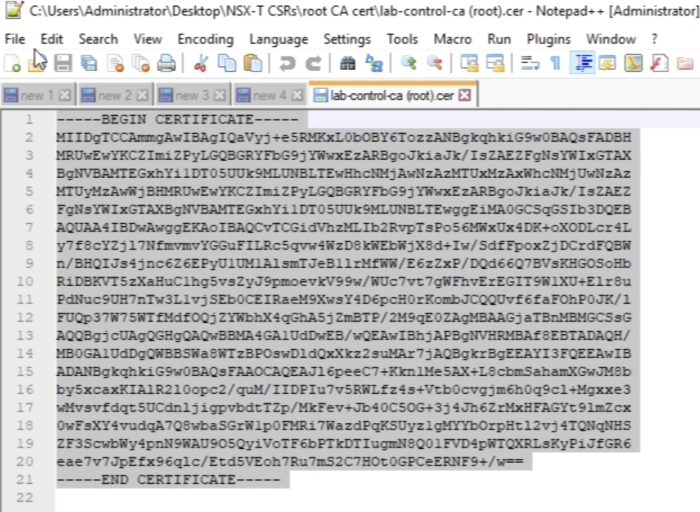
You can view the content as well, as I am doing here with Notepad++. | You can view the content as well, as I am doing here with Notepad++. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:D2E0E5C1-1B55-4800-92CC-2876BBCDA2F3.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
The content of the root certificate authority certificate is displayed below. | The content of the root certificate authority certificate is displayed below. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:31CC0055-84E6-41BC-9FF3-E91404A90B6B.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
So now we have all the prerequisites in place to start with the next step. | So now we have all the prerequisites in place to start with the next step. | ||
=STEP 2 | =STEP 2{{fqm}} Verification on the Microsoft CA Server= | ||
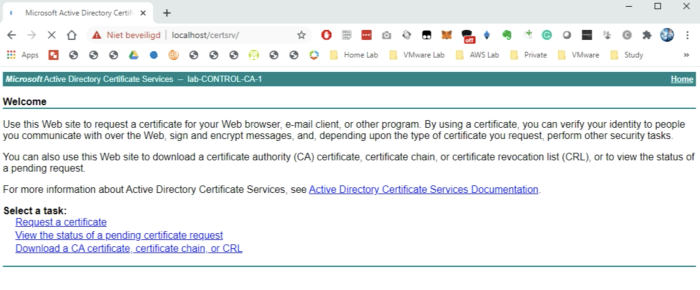
Now that the CA Server and its underlying role services we need to use the web browser and browse to the following URL: | Now that the CA Server and its underlying role services we need to use the web browser and browse to the following URL: | ||
| Line 354: | Line 353: | ||
</pre> | </pre> | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:5C34C38D-4C90-4AF1-A369-86577DE4A148.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Do the additional actions to access the website, this is browser-specific, I am using Google Chrome as you can see. | Do the additional actions to access the website, this is browser-specific, I am using Google Chrome as you can see. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:DF1DB134-4624-4BE6-9F4F-5D8A07D054AA.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
This confirms we can use this (web) server to sign our Certificates with. | This confirms we can use this (web) server to sign our Certificates with. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:03F6E8FD-F951-45D9-961E-A451D009AD3F.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
=STEP 3 | =STEP 3{{fqm}} Preparing the Microsoft CA Server for NSX–T Certificate Signing= | ||
Before we start we need to create a new Certificate Template with some specific settings for the NSX-T Node CA-signed certificates. | Before we start we need to create a new Certificate Template with some specific settings for the NSX-T Node CA-signed certificates. | ||
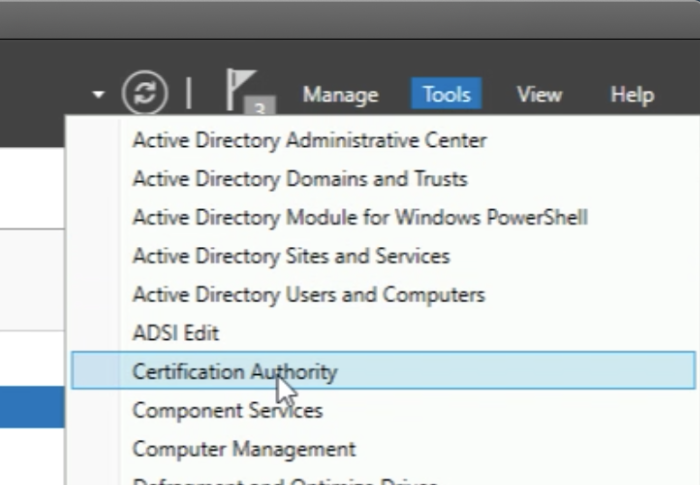
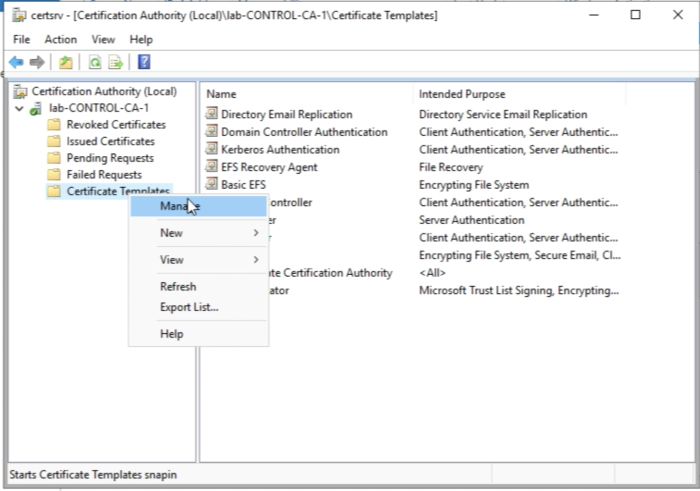
So let's open the Certification Authority Management Console again. | So let's open the Certification Authority Management Console again. | ||
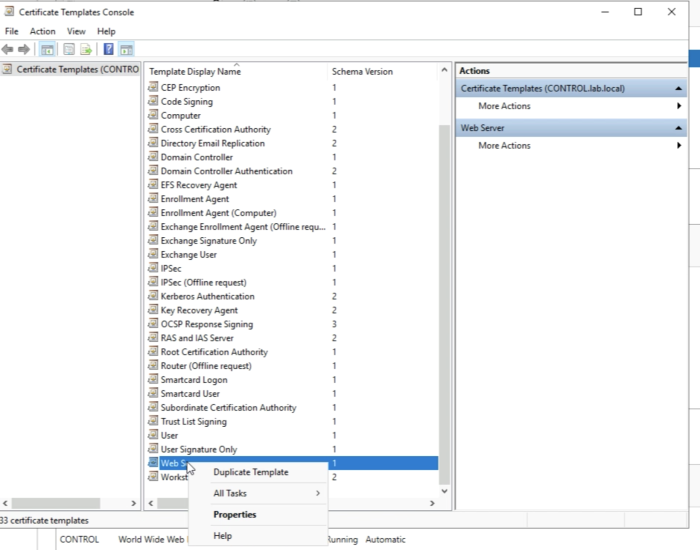
Select Certificate Templates and right-click this and select "Manage". | Select Certificate Templates and right-click this and select "Manage". | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:6E5C9A8E-C135-4552-9CF8-F8ED4460BFA6.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Select the “Web Server” Template and right-click and select "Duplicate Template”. | Select the “Web Server” Template and right-click and select "Duplicate Template”. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:21CB00B6-DC1D-41E6-BD7B-0F48F92D5F78.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
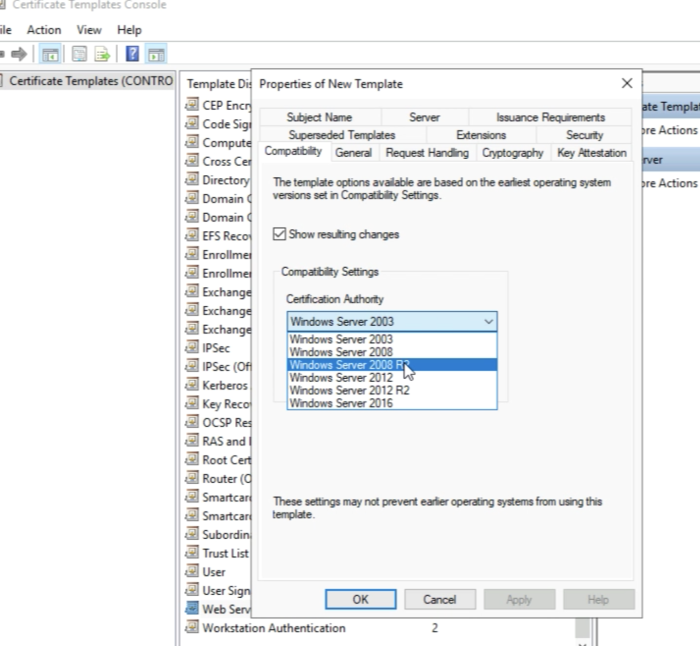
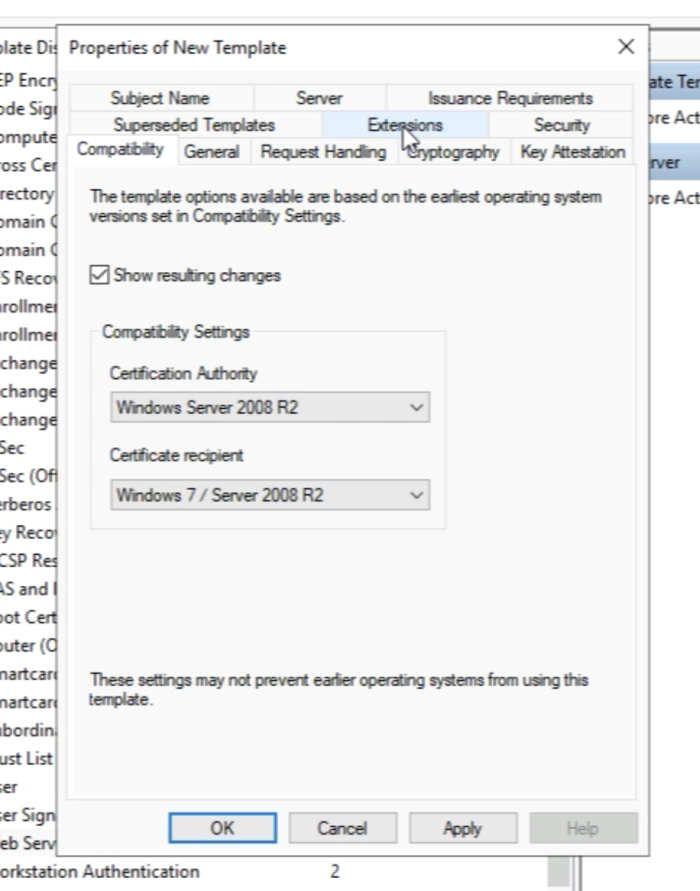
Go to the “Compatibility” tab and select "Windows Server 2008 R2" as the Certificate Authority Compatibility. | Go to the “Compatibility” tab and select "Windows Server 2008 R2" as the Certificate Authority Compatibility. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:8BD68AED-664D-4012-A1CC-D47A0C49EAB5.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
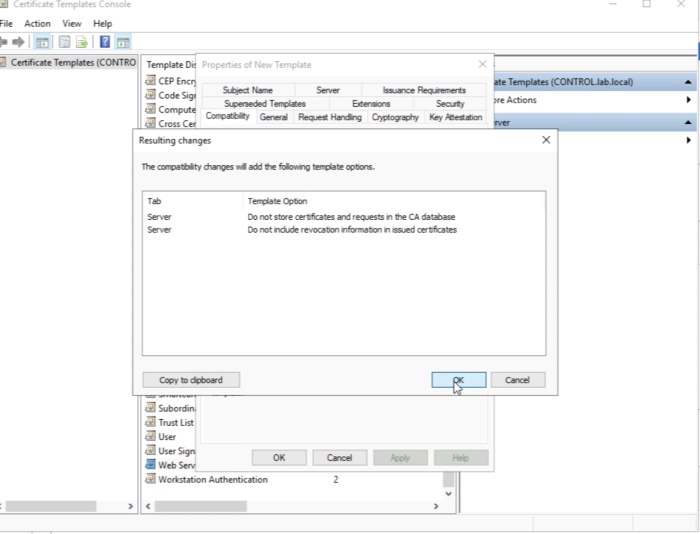
Just click ok on the pop-up window. | Just click ok on the pop-up window. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:3211BA79-824D-4A22-BEAD-BBD53CA95EA4.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Select “Windows 7/Windows 2008 R2" as the "Certificate Recipient". | Select “Windows 7/Windows 2008 R2" as the "Certificate Recipient". | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:D4724F99-D9D0-4DB1-A6E7-59A975DDCEEE.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Just click ok on the pop-up window. | Just click ok on the pop-up window. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:858DEC4D-9031-4705-A954-C53A38913313.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
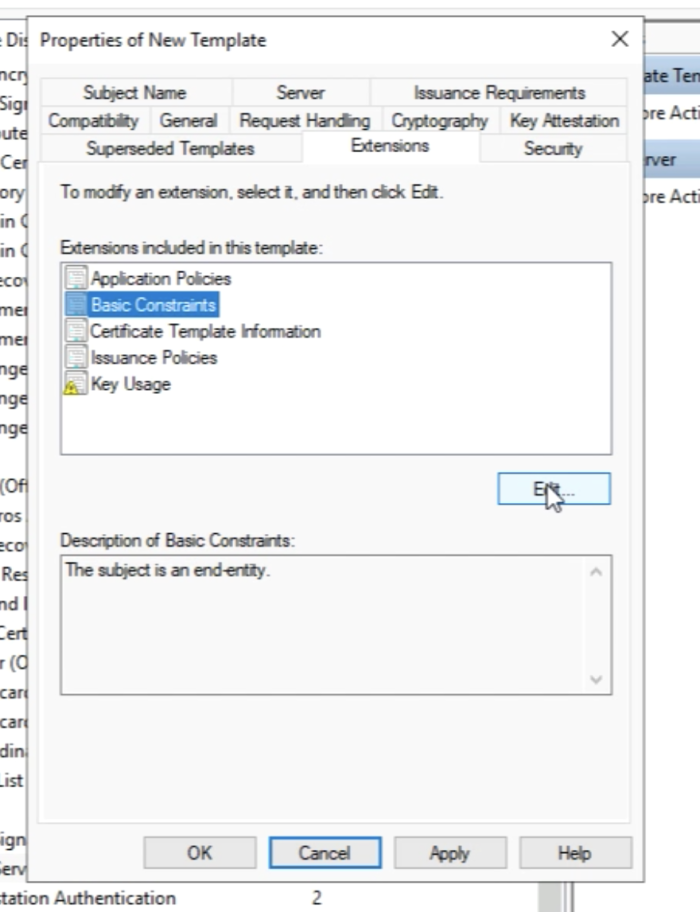
Go to the “Extensions” tab. | Go to the “Extensions” tab. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:F700154C-EDBD-4924-AA46-D18ABCAF5809.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
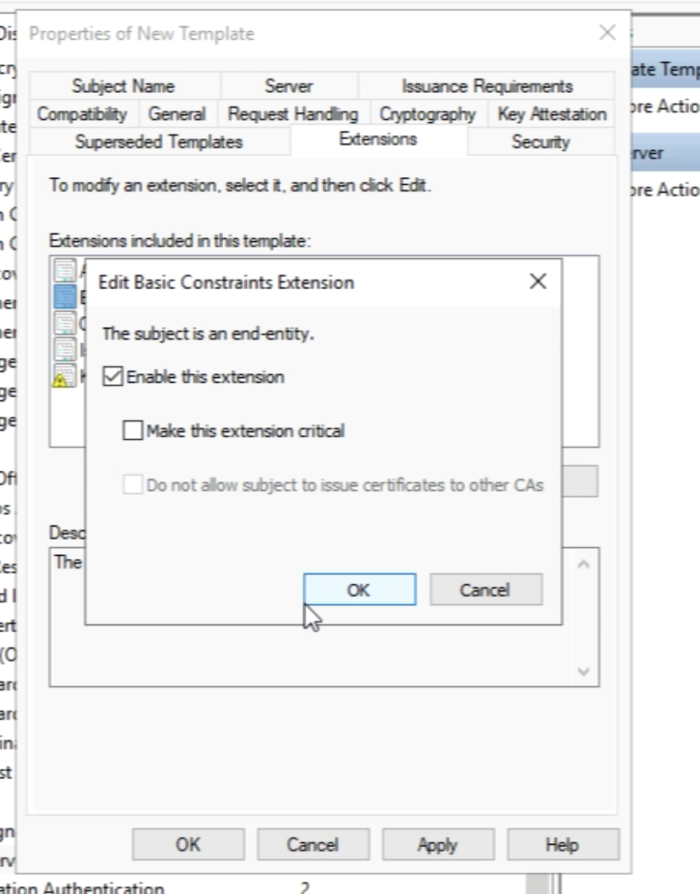
Select “Basic Constraints” and click on "Edit". | Select “Basic Constraints” and click on "Edit". | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:1D3D537F-D352-40A1-BA87-EF4DA2166AE1.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Make sure this extension is enabled by checking the box. | Make sure this extension is enabled by checking the box. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:1418E6AA-2C83-4920-BC07-89553A82C2A0.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
| Line 419: | Line 418: | ||
Close the window with “OK”. | Close the window with “OK”. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:71FA9C79-A5D7-4E05-875A-B2D91D3E4811.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
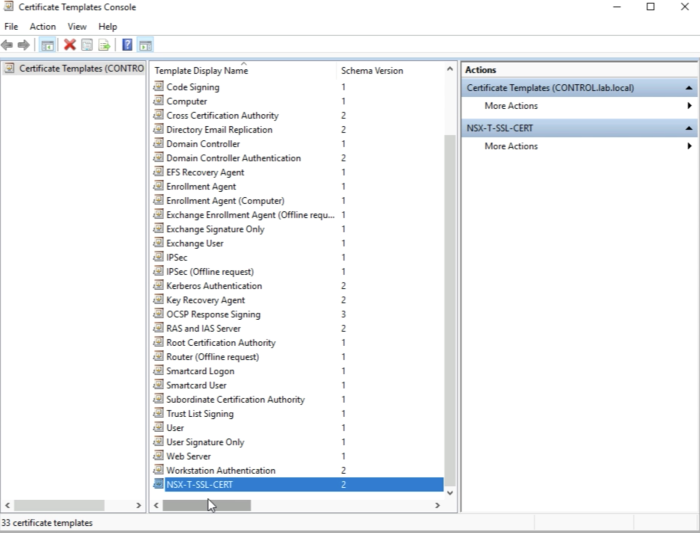
In the list of the Certificates Templates, you now see the new Template. | In the list of the Certificates Templates, you now see the new Template. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:FEDC8B6E-115A-478D-8FC6-CC53EBC5622C.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:A65D67FE-336D-4064-B175-C54C9FDBD075.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
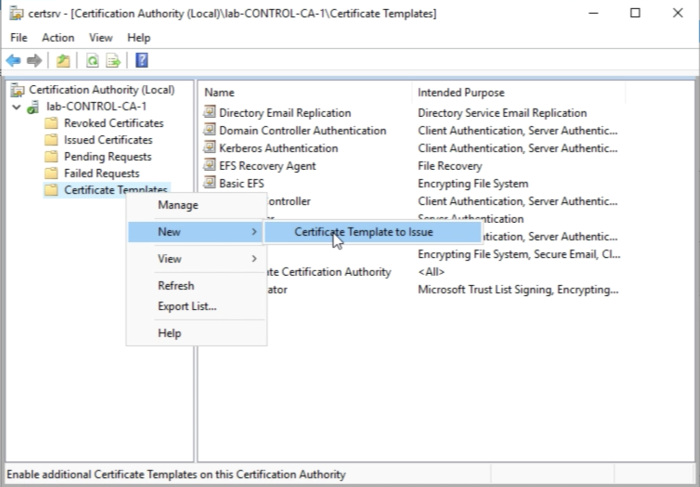
Select the Certificate Templates again and now select "New" and then "Certificate Template to Issue”. | Select the Certificate Templates again and now select "New" and then "Certificate Template to Issue”. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:7D424606-1526-4610-B1B6-A180B75BE624.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
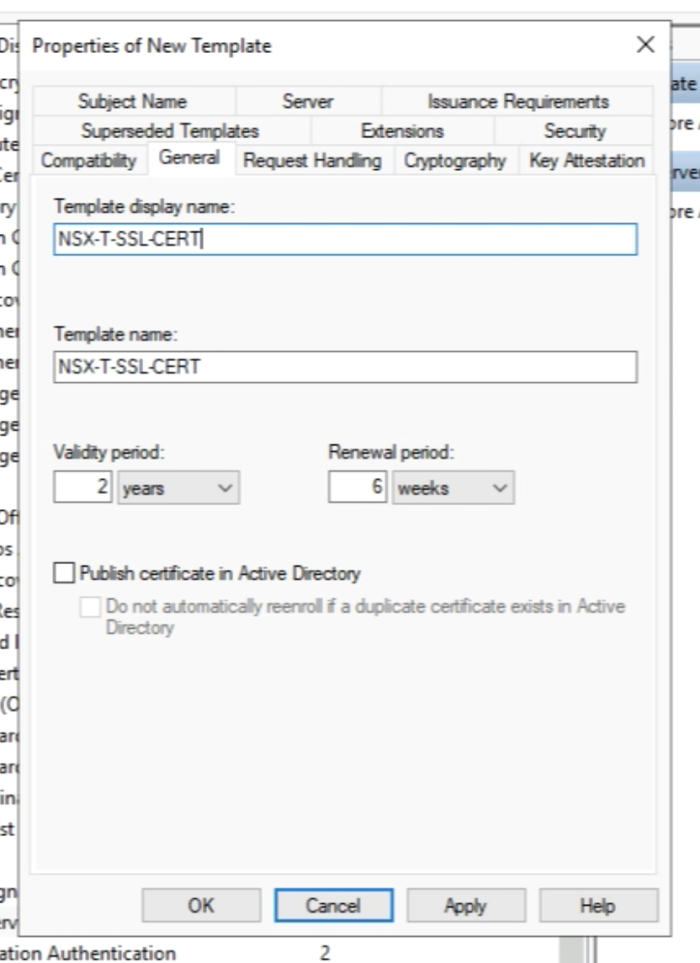
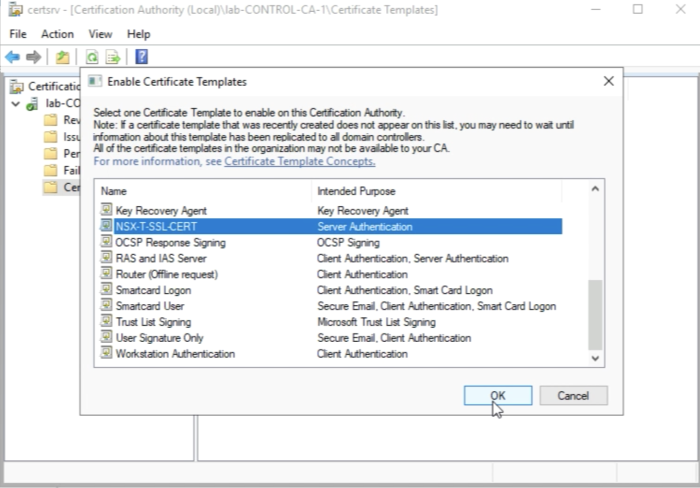
Select the template you just created "NSX-T-SSL-CERT" and click ok "OK". | Select the template you just created "NSX-T-SSL-CERT" and click ok "OK". | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:8C66BDD0-F192-48DA-A3B3-7E1784355A97.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Now you see the new Template listed on the Certificate Templates list. | Now you see the new Template listed on the Certificate Templates list. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:21F42D2E-D88B-47BA-92F3-5E7E1BFF22A9.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
| Line 448: | Line 447: | ||
Select the CA server and right-click and select "Properties" | Select the CA server and right-click and select "Properties" | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:FFC2C012-CA5B-4BF3-A8F3-6ED65845F908.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Validate that that the hash algorithm is set to SHA256. | Validate that that the hash algorithm is set to SHA256. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:6655DB2B-E49E-4FC8-907A-6D164536F736.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Now we have created a Certificate Template with the correct settings that we can use to sign our CSRs. | Now we have created a Certificate Template with the correct settings that we can use to sign our CSRs. | ||
=STEP 4 | =STEP 4{{fqm}} Create Certificate Signing Request 〈CSR〉 for the NSX–T FQDNs= | ||
In this example I am (ab)using me vCenter Server to create Certificate Signing Request for each FQDN we require in NSX-T. | In this example I am (ab)using me vCenter Server to create Certificate Signing Request for each FQDN we require in NSX-T. | ||
| Line 968: | Line 967: | ||
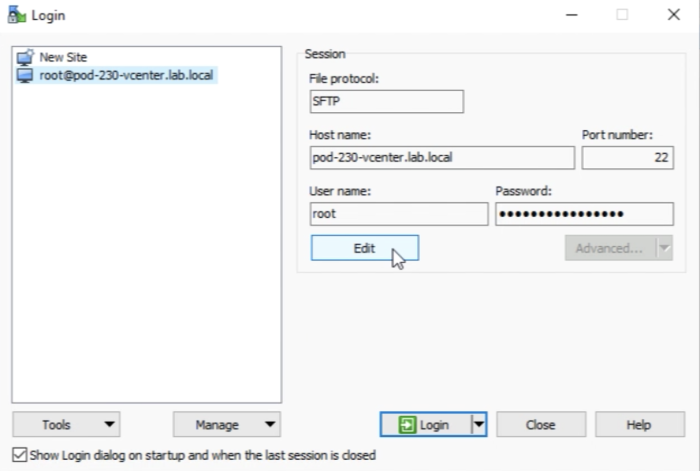
I am using WinSCP for file transfers. | I am using WinSCP for file transfers. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:CB18F040-FA2A-49B5-850E-5B14CEF45427.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
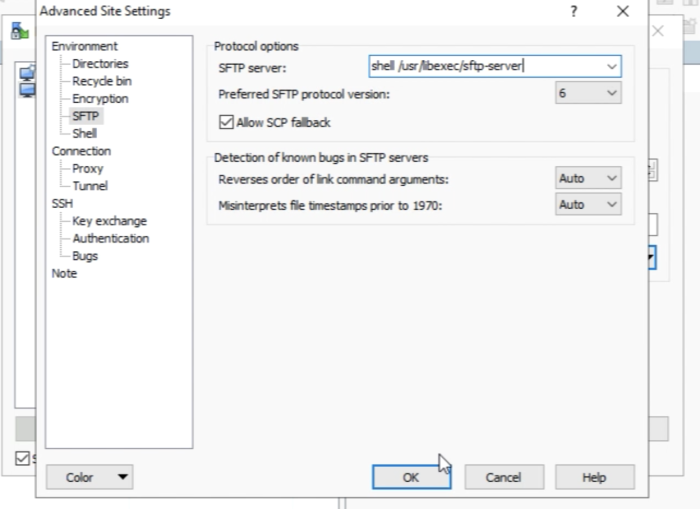
Before we can log in to the vCenter Server with WinSCP we first need to edit a few advanced settings in WinSCP. | Before we can log in to the vCenter Server with WinSCP we first need to edit a few advanced settings in WinSCP. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:6E78F069-6E30-4191-BF8E-3B4F87264015.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Go to the Advanced settings of this session you just saved. | Go to the Advanced settings of this session you just saved. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:B36F5E04-5989-467B-B0BC-63394CC67178.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
| Line 985: | Line 984: | ||
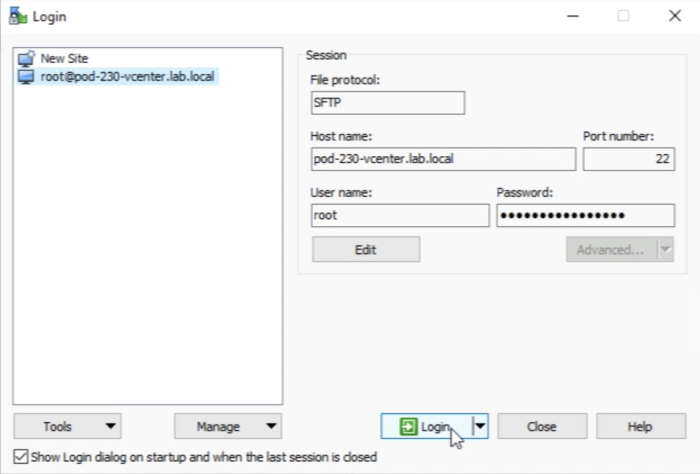
Click on “OK” | Click on “OK” | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:616CEFA1-2BBE-45D2-A905-F063A777E32C.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
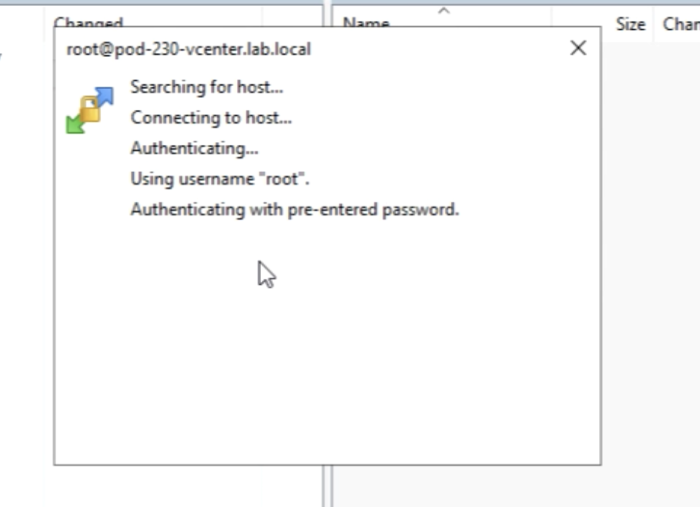
Click on “Login”. | Click on “Login”. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:ED930494-8677-4289-B783-D9EBC9A90107.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
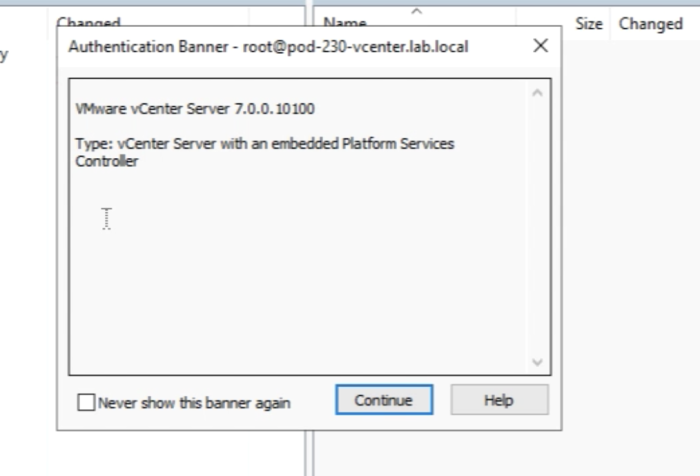
You will get a message and you can click on "continue". | You will get a message and you can click on "continue". | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:4A03FCEE-5506-48F4-B3F7-379EA0223F64.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
You are authenticated. | You are authenticated. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:E06155A5-9F8D-4564-A8CD-8B0D75562ED1.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
And you are in … | And you are in … | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:211DBA5F-9C38-420C-99BF-16BA92529870.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
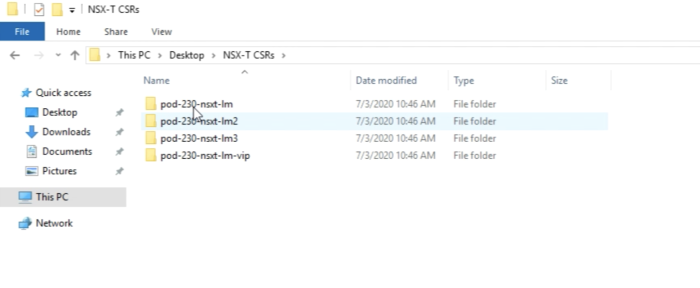
Now to keep things Clean on my computer I am going to create a separate directory for the CSRs I am going to transfer from the vCenter Server to my computer. | Now to keep things Clean on my computer I am going to create a separate directory for the CSRs I am going to transfer from the vCenter Server to my computer. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:1564191A-6ED7-4934-A7C6-E1815D80A8A3.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
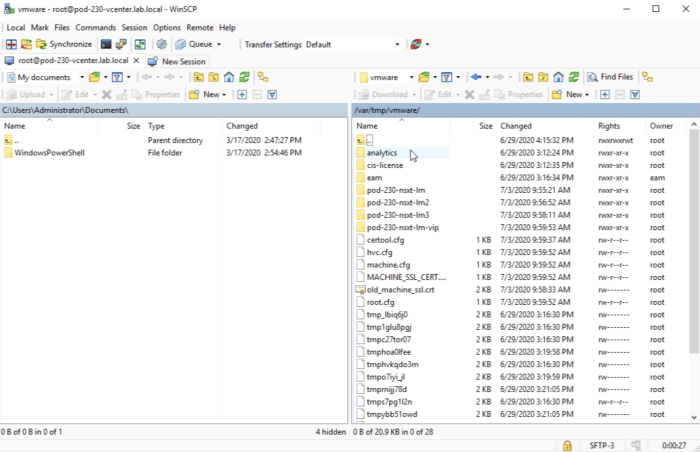
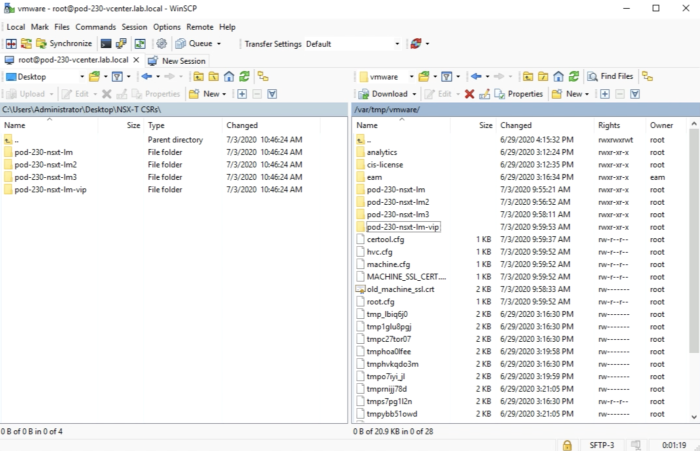
After the fire transfer is done it should look like this inside WinSCP. | After the fire transfer is done it should look like this inside WinSCP. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:3509414A-7E5C-4A1D-A8A5-C36515CB9A83.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
After the fire transfer is done it should look like this inside your computer. | After the fire transfer is done it should look like this inside your computer. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:0A8ED34C-872B-4DB8-8B6D-5FEF6F1235DD.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
| Line 1,026: | Line 1,025: | ||
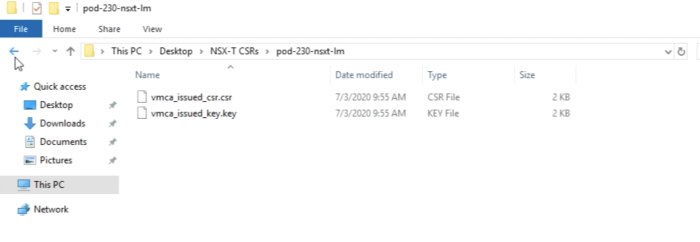
You should see the following files inside each directory. | You should see the following files inside each directory. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:E0886F62-7CB2-49C2-8DC5-E1455BA5D103.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
=STEP 5 | =STEP 5{{fqm}} Signing the generated CSRs with the Microsoft Root Certificate Authority 〈CA〉= | ||
Now you are ready to sign the CSRs with your brand new Microsoft CA Server. | Now you are ready to sign the CSRs with your brand new Microsoft CA Server. | ||
| Line 1,038: | Line 1,037: | ||
Do this on your CA Server. | Do this on your CA Server. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:84AA3FF5-6B1C-41AD-92EF-72B85FFF5482.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Click on Submit an“advanced certificate request". | Click on Submit an“advanced certificate request". | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:CA3ACB39-7C67-4472-9AAA-009B9AC03B19.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
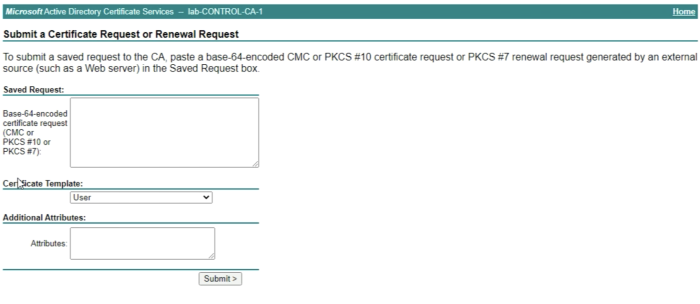
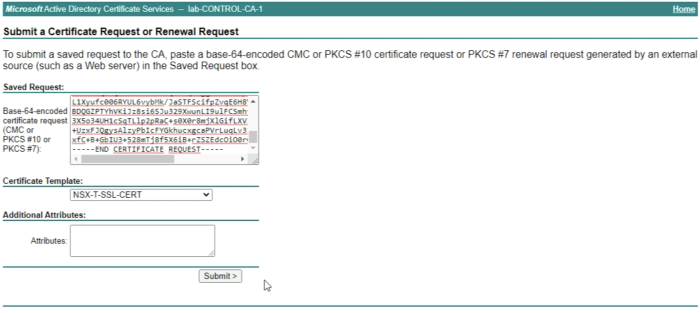
In the “Saved Request” field we need to copy the content of the CSR that we generated on the vCenter Server inside this textbox. | In the “Saved Request” field we need to copy the content of the CSR that we generated on the vCenter Server inside this textbox. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:71DB345A-D5F7-4928-9A3D-644D25A7F22C.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
| Line 1,055: | Line 1,054: | ||
{{note|This is the signing for the first FQDN: pod-230-nsxt-lm1, but the other CSR signing will be done using the same process.}} | {{note|This is the signing for the first FQDN: pod-230-nsxt-lm1, but the other CSR signing will be done using the same process.}} | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:563EF93E-7E4E-4139-9132-553199AA0401.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
'Copy the content of the .csr file | 'Copy the content of the .csr file | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:40BE5C61-62CF-4B22-A7CA-1E9FDFC7D1F0.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Paste the content of the .csr file in the textbox. | Paste the content of the .csr file in the textbox. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:D323D35E-D89F-41E9-A408-CCF7177BDC67.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Select the Certificate Template you created in a previous step, NSX-T-SSL-CERT. | Select the Certificate Template you created in a previous step, NSX-T-SSL-CERT. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:0818E6A4-9B21-4C8D-80A7-6F9A8FFAC54A.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
And click on “Next”. | And click on “Next”. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:CDC820FB-4B71-466B-9FC5-8D32127C8A8D.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
I have created a separate folder to download the "signed" certificates to on the computer, to use for the import later on the NSX-T Manager Nodes. | I have created a separate folder to download the "signed" certificates to on the computer, to use for the import later on the NSX-T Manager Nodes. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:AAC311F0-7A24-4828-BA85-5C219A615528.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
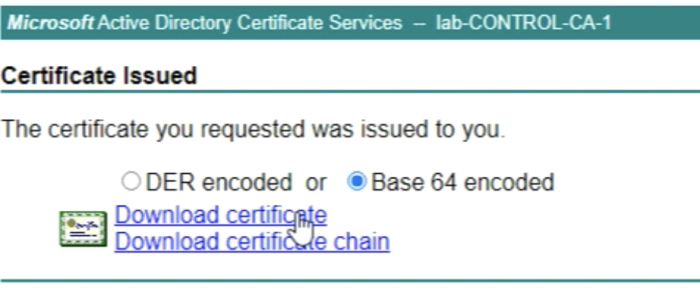
When you clicked on “Submit” you will be able to "Download the certificate" and you need to do this in the “Base 64 encoded” format. | When you clicked on “Submit” you will be able to "Download the certificate" and you need to do this in the “Base 64 encoded” format. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:FA786499-DC4D-4F7E-8AB3-FF9B9A2F1452.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Give your certificate a name and save this in the right directory. | Give your certificate a name and save this in the right directory. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:682D2EB4-1A56-4C91-A445-067172A022E3.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Also save the “certificate chain" by downloading it in the "Base 64 encoded" format. | Also save the “certificate chain" by downloading it in the "Base 64 encoded" format. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:FF90E749-CB46-438A-8493-F2A1C170758D.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Give your certificate a name and save this in the right directory. | Give your certificate a name and save this in the right directory. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:5C1BFC46-DF81-4D67-9099-43CD2052787A.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
When you are finished with the first FQDN you can click on home. | When you are finished with the first FQDN you can click on home. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:1EDB6EB5-4DAD-4B9C-8BFD-E8D662DF56D5.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Now you can restart the process again for the remaining FQDN CSRs. | Now you can restart the process again for the remaining FQDN CSRs. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:B2797589-C3C6-4E78-95A8-34F84869C674.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
You can do a verification when you open the Certificate Authority Management Console. | You can do a verification when you open the Certificate Authority Management Console. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:C4951168-EAD8-475E-B20E-79600791B2FD.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Select the “Issued Certificates" on the right menu to verify all your signed certificates. | Select the “Issued Certificates" on the right menu to verify all your signed certificates. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:33A19B54-FC04-4977-AB56-438A9E9DC871.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
A good practice is to look up the "root" certificate on your computer. | A good practice is to look up the "root" certificate on your computer. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:678EB3ED-03FC-4C81-8F2E-2C54B57466EB.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
And rename it so it is clear that this is the "root" CA Certificate. | And rename it so it is clear that this is the "root" CA Certificate. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:67C28B40-CFE8-4DE7-96C6-CA1D9C45A5FE.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Also, create a separate folder for the root certificate and place the root certificate in there. | Also, create a separate folder for the root certificate and place the root certificate in there. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:7FD5CEEF-2671-430B-9E12-FAA33DA89D74.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
At this point, you should have a clean folder structure with all your CSRs, the signed CSRs, and the Root Certificate of your Certificate Authority. | At this point, you should have a clean folder structure with all your CSRs, the signed CSRs, and the Root Certificate of your Certificate Authority. | ||
=STEP 6 | =STEP 6{{fqm}} Import the CA–signed certificates into the NSX–T Manager Nodes= | ||
You can import all certificates by browsing to the VIP FQDN of your NSX-T Manager Cluster. | You can import all certificates by browsing to the VIP FQDN of your NSX-T Manager Cluster. | ||
| Line 1,148: | Line 1,147: | ||
</pre> | </pre> | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:A8A34BF0-149E-468F-BE34-99214DC76D16.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Log in to the NSX-T Manager. | Log in to the NSX-T Manager. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:EF927D12-06D1-4BCF-9F48-E376D6D154C7.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Browse to “System”. | Browse to “System”. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:C5FE7323-1462-48D8-85FA-A7F6013DCFEA.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
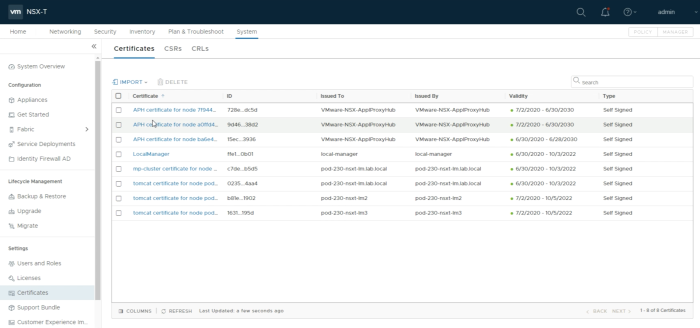
Go to Settings => Certificates. | Go to Settings => Certificates. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:A5FBDB2A-D78D-4D7F-8275-F5997427420A.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
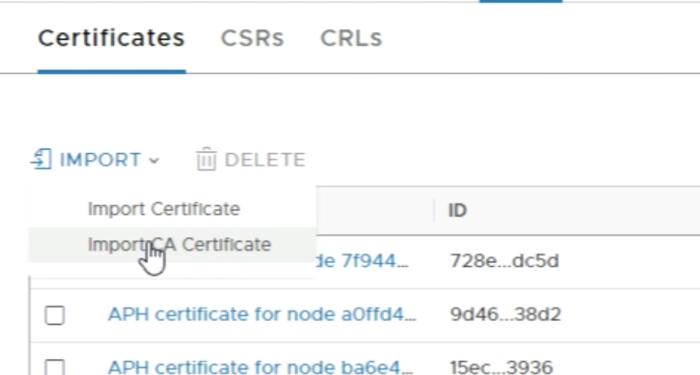
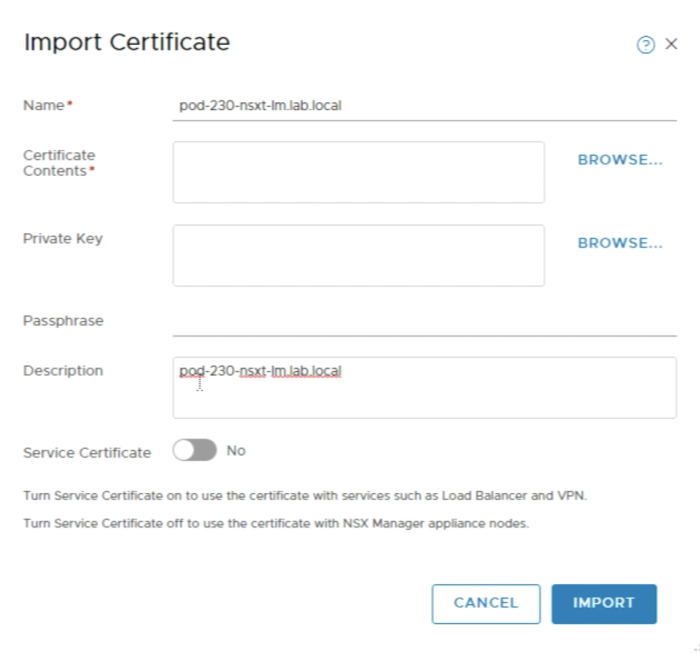
First you need to import the root certificate of out Microsoft Certificate Authority Server. | First you need to import the root certificate of out Microsoft Certificate Authority Server. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:BF7F90A0-9D9E-466E-8334-87E6D115C67A.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
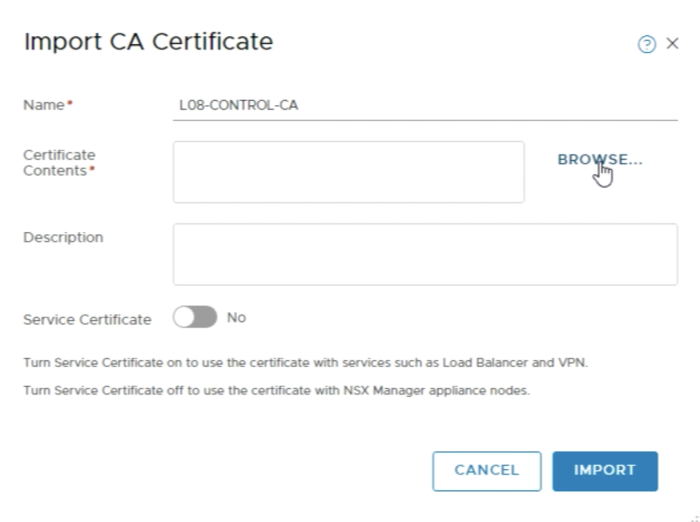
You can import the root certificate using the browse button. | You can import the root certificate using the browse button. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:41C9549F-6082-4B32-9D9D-C3860E9C5243.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
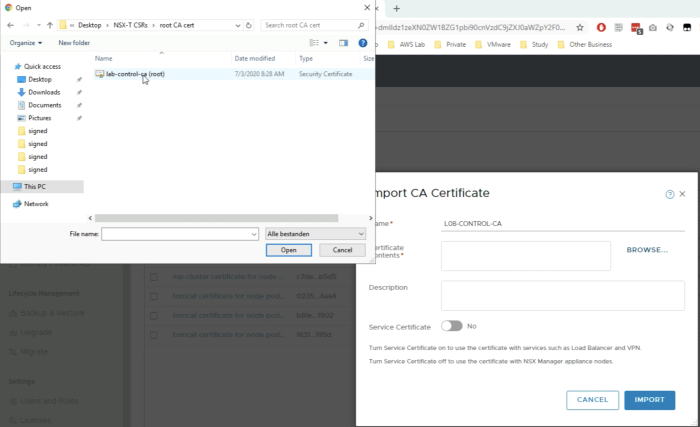
And you select the root certificate file. | And you select the root certificate file. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:B1309736-A3DC-4F4E-AC38-8E7C98A10D5F.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
| Line 1,184: | Line 1,183: | ||
And click “Import”. | And click “Import”. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:5B78CEB0-0275-4D11-91A2-E3CF166FF188.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
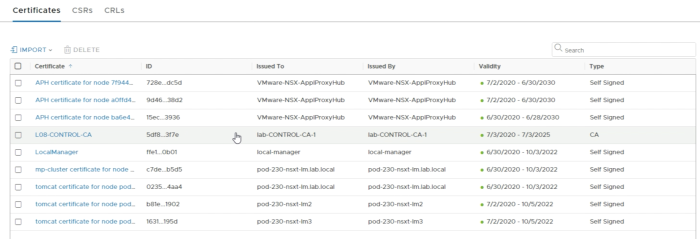
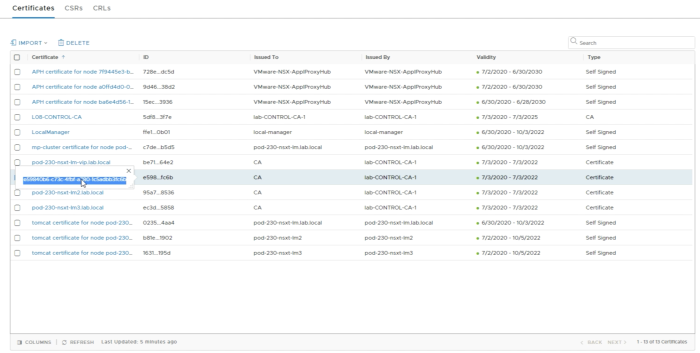
In the overview, you see that the CA certificate is now imported. | In the overview, you see that the CA certificate is now imported. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:1315E473-C1F0-4C61-95DF-56C446879BF6.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Now we are going to import the FQDN signed Certificates. | Now we are going to import the FQDN signed Certificates. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:5F536B04-9B56-4D55-9188-CA4F33525DB6.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
| Line 1,204: | Line 1,203: | ||
So we start with the Signed Certificate and we end with the Root Certificate. | So we start with the Signed Certificate and we end with the Root Certificate. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:9D4B9499-6673-470E-B81A-92B6EA7B4536.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
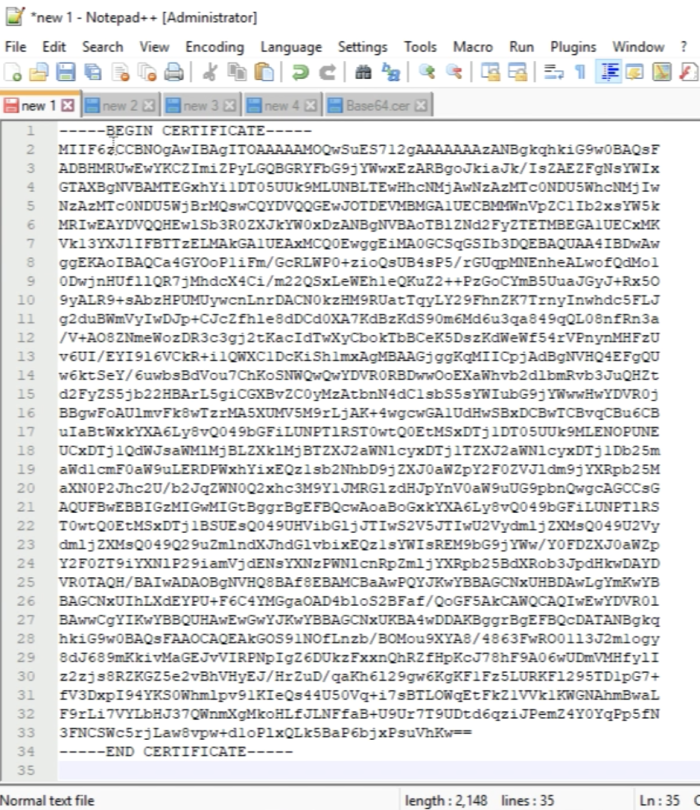
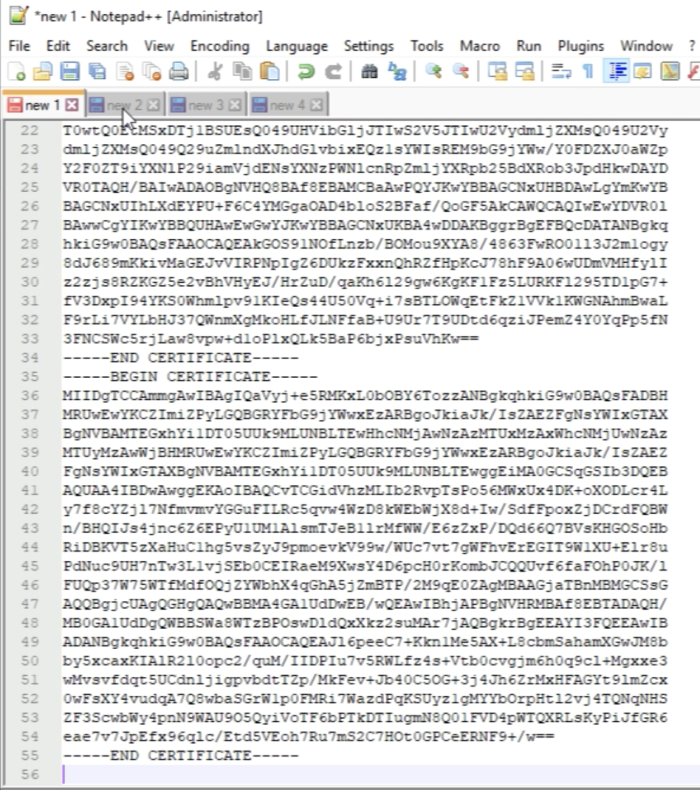
The best way is to open a blank notepad for all signed certificates. | The best way is to open a blank notepad for all signed certificates. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:D1FDF680-C2F8-4B22-82F6-1EF5AE381B65.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Open the Base64 Certificate with Notepad++. | Open the Base64 Certificate with Notepad++. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:63EA7382-78C2-4BBD-B91F-5C3B4E15EE39.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
'Copy the output of the Certificate. | 'Copy the output of the Certificate. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:6BCB68DA-8DBC-4B3E-ACB7-5AD480DB719C.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Paste the Certificate into a blank text file. | Paste the Certificate into a blank text file. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:C028B290-42C7-4548-B8B9-0DBA0FA05BE1.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Open the root certificate into Notepad++. | Open the root certificate into Notepad++. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:6878D686-48EA-4F6A-883E-F0F374C055F9.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
'Copy the content of the root certificate. | 'Copy the content of the root certificate. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:EE66A8DD-69E1-47E6-8AAA-DD5A6F80D089.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
| Line 1,267: | Line 1,266: | ||
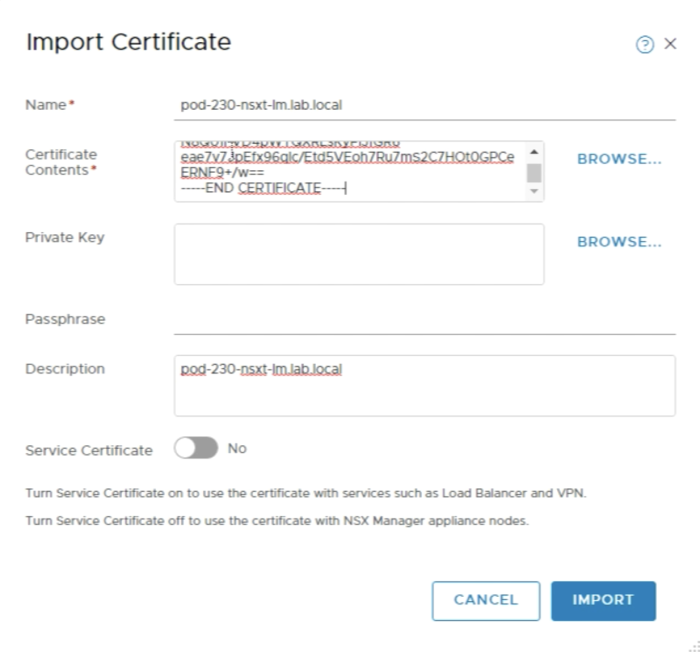
An example of this is given in the figure below. | An example of this is given in the figure below. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:56936794-2BF2-413B-88B0-288A4584688E.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
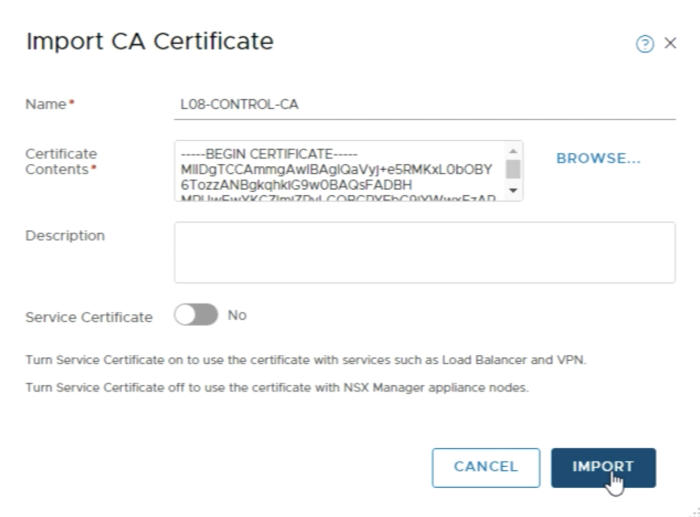
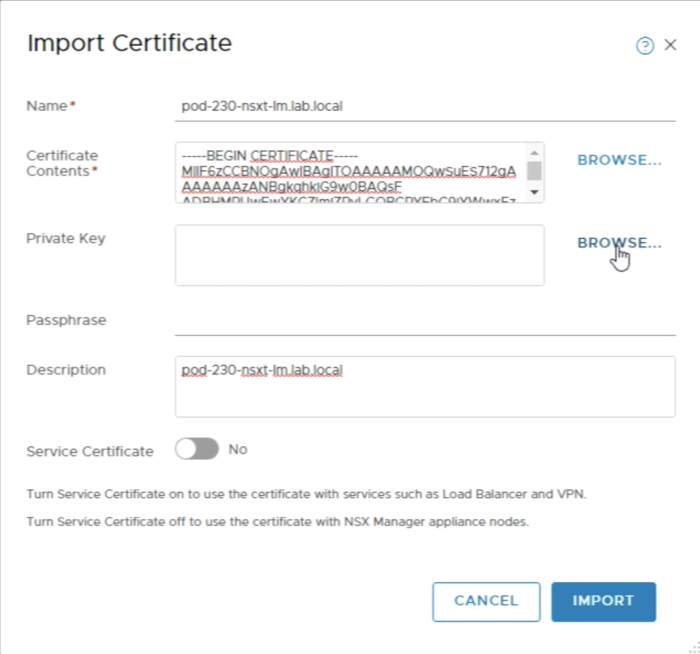
Paste in the content of the signed certificate including the root certificate into the Certificate Contents field. | Paste in the content of the signed certificate including the root certificate into the Certificate Contents field. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:0916FA20-EB7C-422D-9179-0B8E305216AB.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
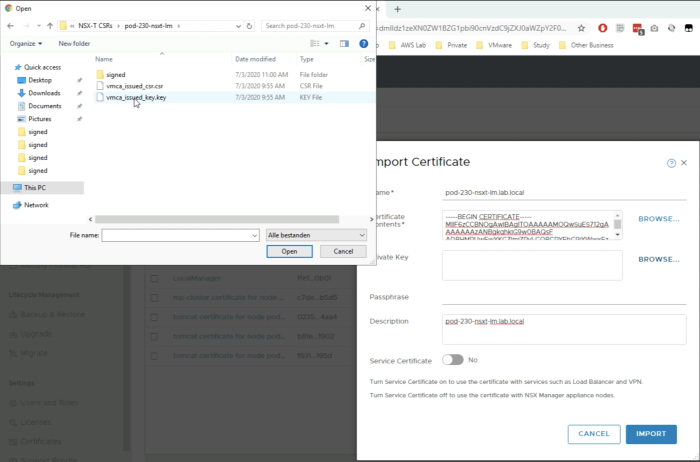
Click browse to import the “Private Key" that belongs to the signed certificate file. | Click browse to import the “Private Key" that belongs to the signed certificate file. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:653A6429-2BFF-4358-9DFC-848C0B9978F8.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Select the .key file. | Select the .key file. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:DF34E5F2-D10D-4D3A-9994-F34FC9B6E9AB.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
| Line 1,288: | Line 1,287: | ||
Eventually, you will have all the signed certificates imported for all FQDNs. | Eventually, you will have all the signed certificates imported for all FQDNs. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:3CC6D680-D110-492E-93C7-58A9D68A7AEB.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Now all the signed certificates for all FQDNs and the Root Certificate should be imported. | Now all the signed certificates for all FQDNs and the Root Certificate should be imported. | ||
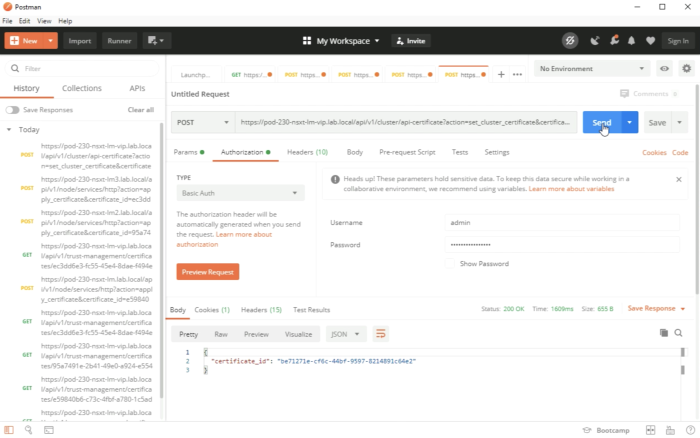
=STEP 7 | =STEP 7{{fqm}} Activate uploaded CA–signed certificates with REST API calls= | ||
In order to “activate” the uploaded certificates, you need to do this with REST API calls. | In order to “activate” the uploaded certificates, you need to do this with REST API calls. | ||
I used the Postman application to do this. | I used the Postman application to do this. | ||
| Line 1,299: | Line 1,298: | ||
My good friend Rutger Blom has written a very good blog article using PostMan with NSX-T [https://rutgerblom.com/2019/06/16/getting-started-with-the-nsx-t-api-and-postman/ here]. | My good friend Rutger Blom has written a very good blog article using PostMan with NSX-T [https://rutgerblom.com/2019/06/16/getting-started-with-the-nsx-t-api-and-postman/ here]. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:C202F200-6D83-44BD-AAF8-0F9EC5A663AE.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
In order to start, we need to create a new request. | In order to start, we need to create a new request. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:4C72F5BD-654D-4FD9-B68A-6384E39F22FA.png|200px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
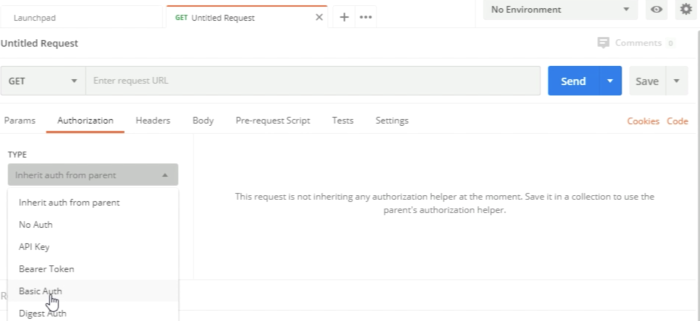
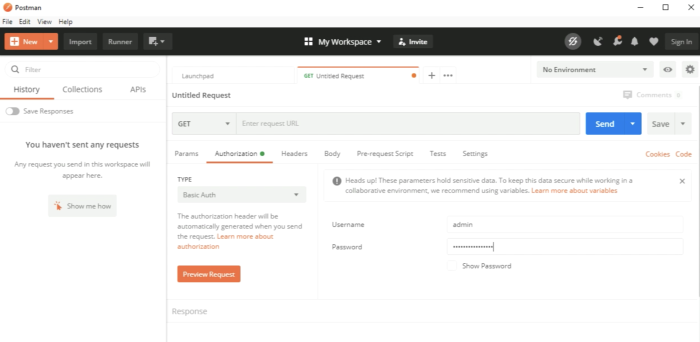
Configure the authorization by choosing "Basic Auth". | Configure the authorization by choosing "Basic Auth". | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:533BA2AB-1C88-40C3-B2C3-7314E7F9FA4D.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Type in the NSX-T credentials. | Type in the NSX-T credentials. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:B591B26E-884F-45EB-8ABB-C176738D3386.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
| Line 1,324: | Line 1,323: | ||
</pre> | </pre> | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:8F12DA9E-AEFE-47D4-9A4C-DE34A5703FFF.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
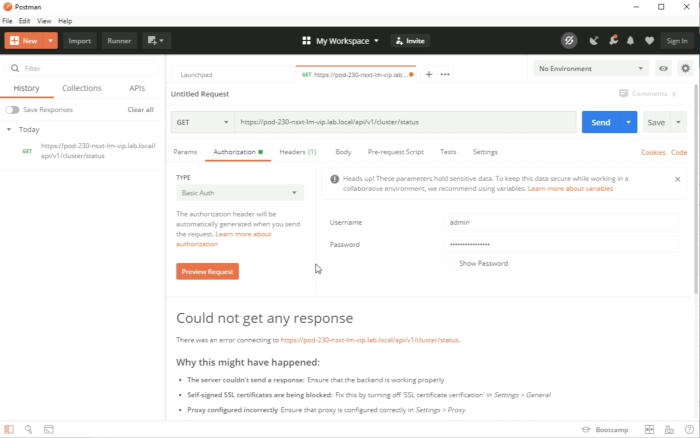
We can see that the GET request wat not successful and it gives you a hint that the SSL certificates are being blocked. | We can see that the GET request wat not successful and it gives you a hint that the SSL certificates are being blocked. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:2AC0FE41-CDC2-4783-9B0D-37C5D4043FAB.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
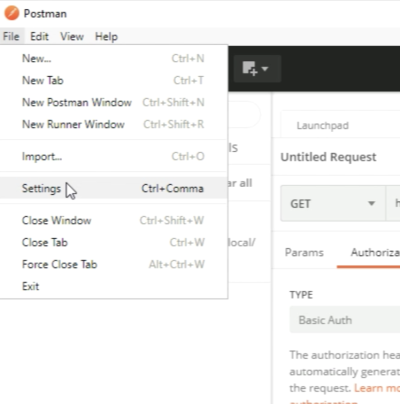
Go to File and select Settings in the menu of the Postman application. | Go to File and select Settings in the menu of the Postman application. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:CEDF7878-DF76-4436-9A25-595469C72284.png|400px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
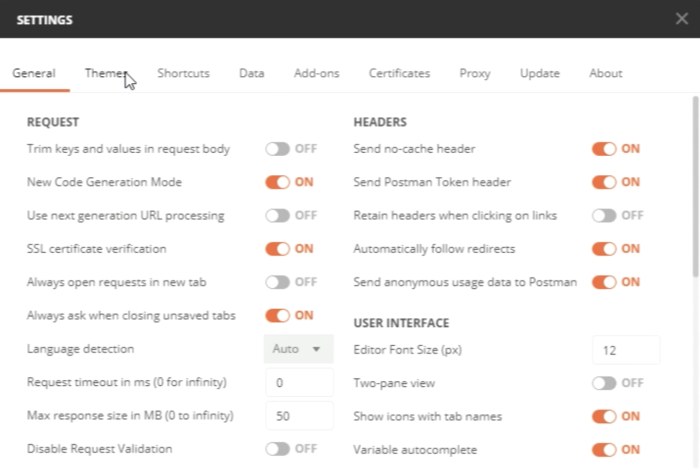
You can see that by default the "SSL certificate verification" is set to "ON". | You can see that by default the "SSL certificate verification" is set to "ON". | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:D57D7152-09BA-4215-A399-05D3C725B385.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Make sure the "SSL certificate verification" is set to "OFF". | Make sure the "SSL certificate verification" is set to "OFF". | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:73F68FE1-0887-4D87-904D-A63E95FB38B9.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
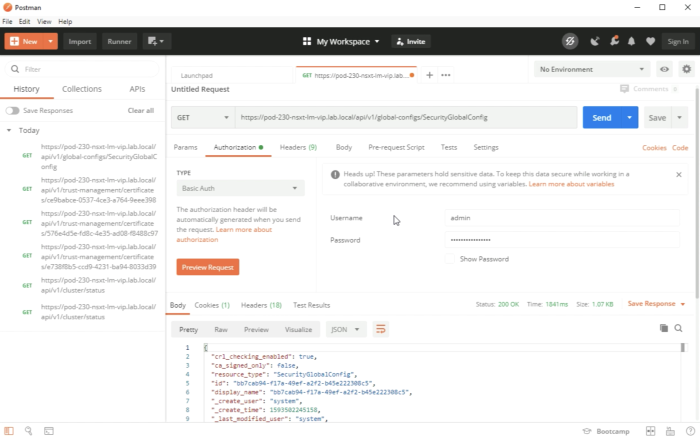
Now when we execute out test REST API call again we can see a STATUS: 200 OK, and some JSON code with information about the NSX-T Cluster. | Now when we execute out test REST API call again we can see a STATUS: 200 OK, and some JSON code with information about the NSX-T Cluster. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:56C40E28-EDBC-453F-AC11-F1031EC8385E.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
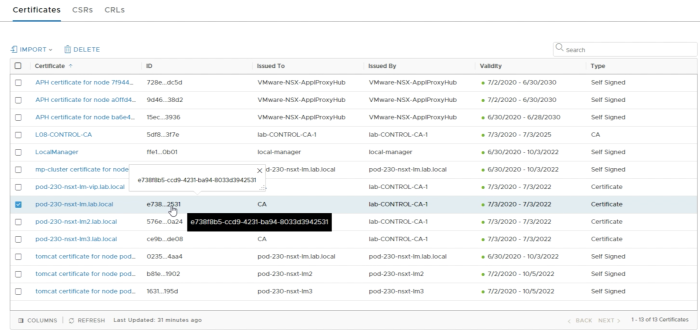
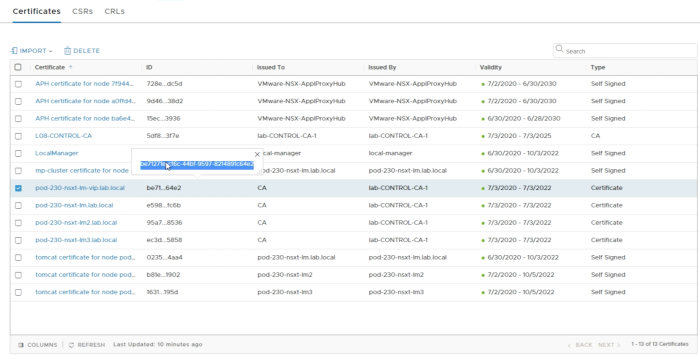
In order to “activate” the new certificates, we need to collect the certificate ID’s from the GUI as these are required to refer to the certificates during the activation process. | In order to “activate” the new certificates, we need to collect the certificate ID’s from the GUI as these are required to refer to the certificates during the activation process. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:2A2378AF-A362-47B9-B45A-0AA967F8E3D9.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
| Line 1,371: | Line 1,370: | ||
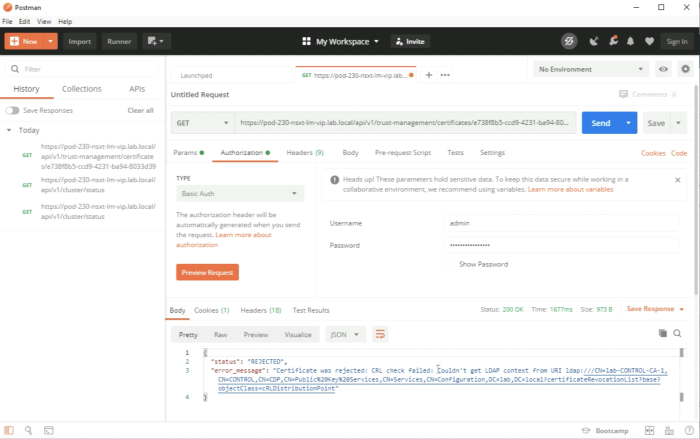
If the CRL check cannot be performed, the certificate cannot be applied to a Manager node or cluster. | If the CRL check cannot be performed, the certificate cannot be applied to a Manager node or cluster. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:117F95A2-D34E-4AB3-837B-4DA97D1AC212.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
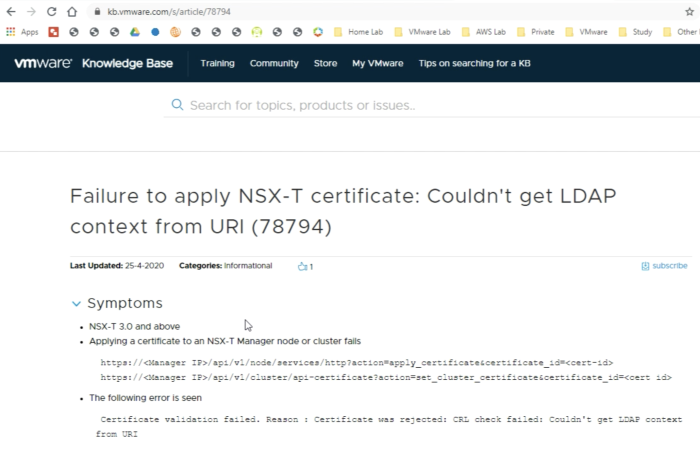
You can turn this off by following the content of [https://kb.vmware.com/s/article/78794 this VMware KB (78794)]. | You can turn this off by following the content of [https://kb.vmware.com/s/article/78794 this VMware KB (78794)]. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:A4FE4A53-81A8-4FFB-9F59-23B6A3FEBABE.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
| Line 1,386: | Line 1,385: | ||
</pre> | </pre> | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:FA50ABD9-C688-41B3-AAAD-9FDCAB99F40E.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
| Line 1,405: | Line 1,404: | ||
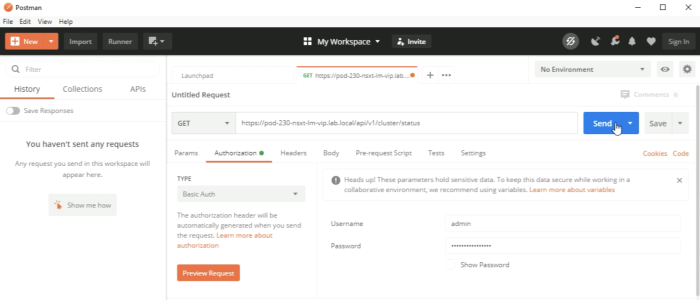
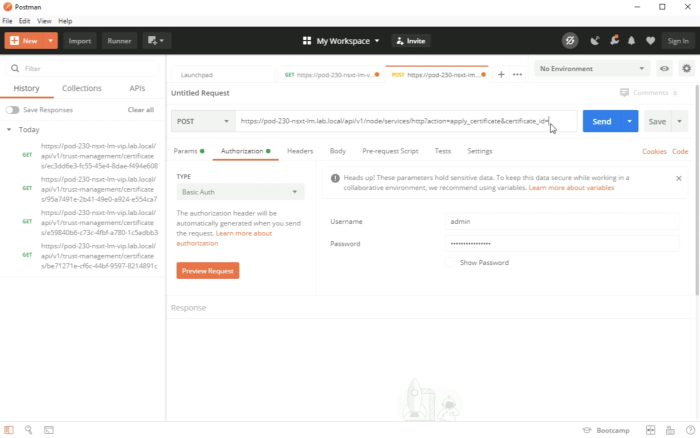
Execute the REST API call. | Execute the REST API call. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:1FF09BF9-E72C-4AFD-8751-3FA81192CE7D.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
| Line 1,412: | Line 1,411: | ||
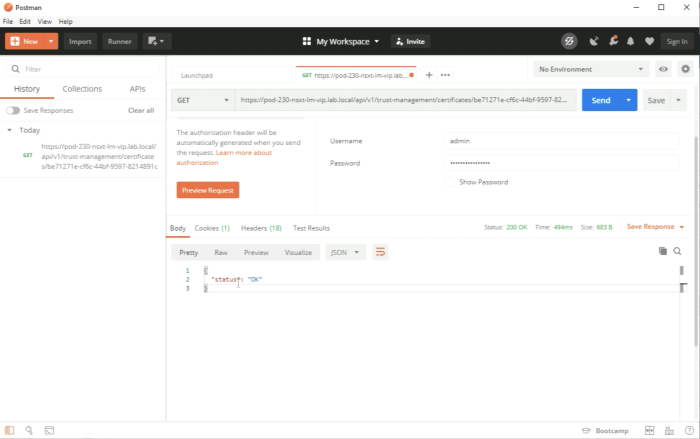
You should get a “status” : “OK" back from the call and a Status: 200 OK. | You should get a “status” : “OK" back from the call and a Status: 200 OK. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:4F5FAB0E-2A4F-4E67-9277-8E5C0418FAFA.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
| Line 1,435: | Line 1,434: | ||
An example of the first manager is shown in the figure below. | An example of the first manager is shown in the figure below. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:7781A39C-D542-483A-9FD6-53FDF38956F9.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Make sure you 'copy the certificate ID that is retrieved fomr the NSX-T GUI. | Make sure you 'copy the certificate ID that is retrieved fomr the NSX-T GUI. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:517397AA-B210-4532-8952-99D88D038B16.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
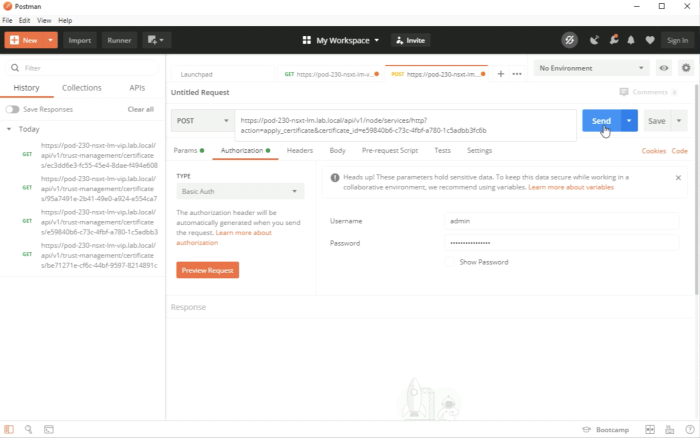
Complete the full REST API URL and click on Send. | Complete the full REST API URL and click on Send. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:DCF26E22-D60D-47CC-A0C6-44D3FF25D905.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
| Line 1,455: | Line 1,454: | ||
An example of this is given in the figure below. | An example of this is given in the figure below. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:170CA1EB-0F4A-4209-AB72-CF2BE77899AE.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
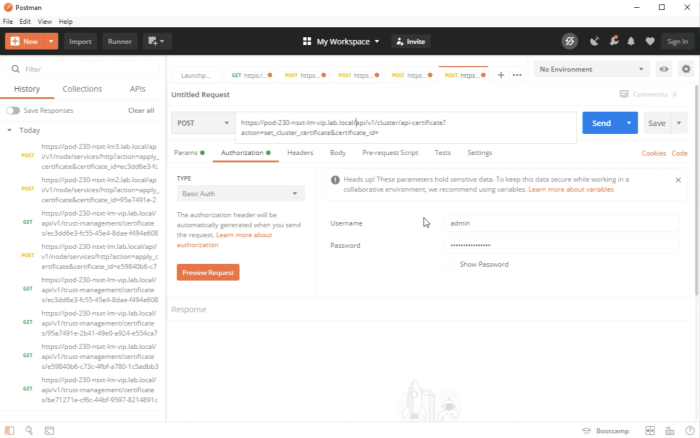
Make sure you 'copy the Certificate ID from the NSX-T GUI for the VIP FQDN. | Make sure you 'copy the Certificate ID from the NSX-T GUI for the VIP FQDN. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:C6D1E1A2-2651-4221-A94A-89EC91C2E41E.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
Execute the REST API call. | Execute the REST API call. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:EC46C708-8941-49FC-8DCE-ADE55E306F1B.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
| Line 1,471: | Line 1,470: | ||
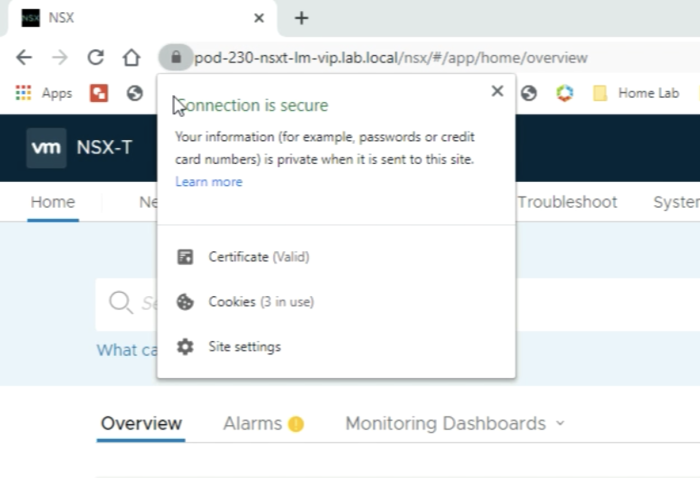
Notice age little lock in front of the URL. | Notice age little lock in front of the URL. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:C0438075-1512-492F-A057-F2AB48121F2E.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
When you click on the lock you can see the message that the connection is secure and that the certificate is valid for the VIP FQDN. | When you click on the lock you can see the message that the connection is secure and that the certificate is valid for the VIP FQDN. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:214463AB-F09B-44CA-87AA-64A8C13EF59F.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
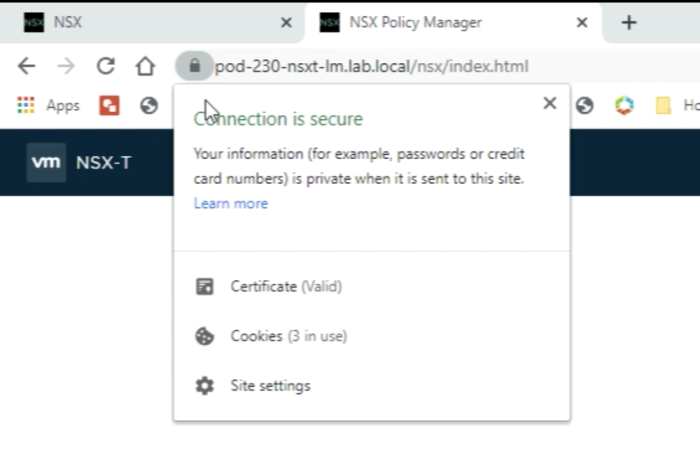
You will get the same result when you go to the URL of one of the NSX-T Manager nodes directly. | You will get the same result when you go to the URL of one of the NSX-T Manager nodes directly. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:0FFD2DDD-1663-4563-8EB1-D4FD4CF6D5BD.png|700px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
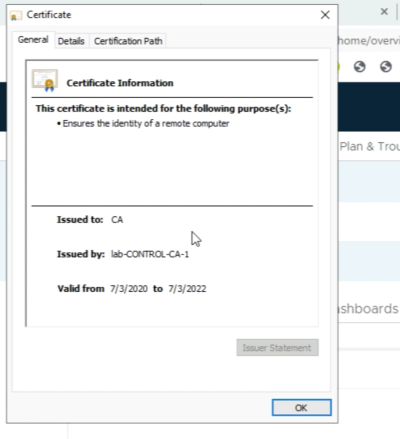
When you click on the Certificate you can look at other certificate details in the General Tab where you can see the Root CA that signed the certificate. | When you click on the Certificate you can look at other certificate details in the General Tab where you can see the Root CA that signed the certificate. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:D1CC847D-1459-4DA0-95DD-79FFE260C0C6.png|400px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
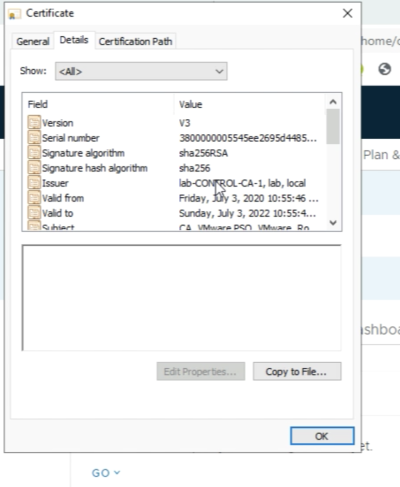
When you click on the “Details" tab you can see more details about the certificate. | When you click on the “Details" tab you can see more details about the certificate. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:4CB18101-4ACC-4EF8-BBF4-1E90149763E2.png|400px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
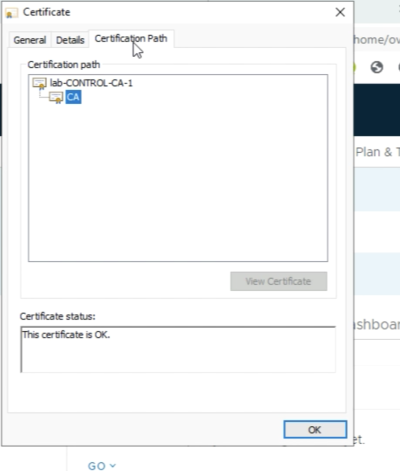
And finally, you can view the "Certification Path" by going to the "Certification Path” tab. | And finally, you can view the "Certification Path" by going to the "Certification Path” tab. | ||
<span style="border:3px solid | <span style="border:3px solid #f4c613;display: inline-block;">[[File:13A32B3C-CD6B-45DB-A728-8F40E7CCDAD3.png|400px]]</span> | ||
<div style="clear:both"></div> | <div style="clear:both"></div> | ||
You have reached the end of this article, and I know it was a long one, but I hope you have learned something so that you can replicate this in your test of the production environment. | You have reached the end of this article, and I know it was a long one, but I hope you have learned something so that you can replicate this in your test of the production environment. | ||
= | =OPTIONAL» Use one single signed certificate for all NSX-T FQDNs - including the VIP= | ||
In the steps above I have shown you how to generate CSRs for all separate FQDNs of all separate NSX-T Manager Nodes and the NSX-T VIP address. | In the steps above I have shown you how to generate CSRs for all separate FQDNs of all separate NSX-T Manager Nodes and the NSX-T VIP address. | ||
One of my US-based | One of my US-based colleagues ([https://www.linkedin.com/in/mifye/ Michael (Cobi) Fye]) asked me the question if he could also use ONE SINGLE CSR only with all the Subject Alternative Names (SANs) and get this CSR signed by the (root) Certificate Authority (CA) and use this single-signed Certificate for all of the Manager Nodes including the NSX-T VIP address. | ||
I did not test this, but fortunately, he did. | I did not test this, but fortunately, he did. | ||
| Line 1,513: | Line 1,512: | ||
# Import the (root) Certificate into the NSX-T Manager(s) | # Import the (root) Certificate into the NSX-T Manager(s) | ||
# Import the CA-signed certificates into the NSX-T Manager Nodes | # Import the CA-signed certificates into the NSX-T Manager Nodes | ||
## Like I am doing in [[ | ## Like I am doing in [[CA signed certs with NSX-T#STEP 6: Import the CA-signed certificates into the NSX-T Manager Nodes|Step 6]] | ||
# Activate uploaded CA-signed certificates with REST API calls | # Activate uploaded CA-signed certificates with REST API calls | ||
## Like I am doing in [[ | ## Like I am doing in [[CA signed certs with NSX-T#STEP 7: Activate uploaded CA-signed certificates with REST API calls|Step 7]] | ||
## Only now you are only using one single certificate with the same Certificate ID using 4 different API calls (3 x for the NSX-T Manager Nodes, and 1 x for the VIP address) | ## Only now you are only using one single certificate with the same Certificate ID using 4 different API calls (3 x for the NSX-T Manager Nodes, and 1 x for the VIP address) | ||
| Line 1,583: | Line 1,582: | ||
|- | |- | ||
| Bode Fatona || [https://www.linkedin.com/in/bode-fatona-2602ba1/ Link] | | Bode Fatona || [https://www.linkedin.com/in/bode-fatona-2602ba1/ Link] | ||
|} | |} | ||
I am always trying to improve the quality of my articles so if you see any errors, mistakes in this article or you have suggestions for improvement, [[Special:Contact|please contact me]] and I will fix this. | I am always trying to improve the quality of my articles so if you see any errors, mistakes in this article or you have suggestions for improvement, [[Special:Contact|please contact me]] and I will fix this. | ||
[[Category:NSX | [[Category: NSX]] | ||
[[Category: | [[Category:Networking]] | ||
[[Category:VMware]] | |||
Latest revision as of 16:39, 17 March 2024
This wiki article will guide you through the process of replacing your NSX-T Manager Node self-signed SSL Certificates with your own CA-signed SSL certificates. There are many ways to generate CSR's, set up Certificate Authorities, and sign CSR's. In this article, however, I am explaining how this is done using one of these methods. I will show you a full end-to-end process from setting up your own Microsoft Windows CA Server, generating CSR's and how to use this CA Server to sign your own NSX-T SSL Certificates.
The high–level steps
In this wiki, the high level following steps will be discussed:
- STEP 1: Configuring a Microsoft Server to be a Root Certificate Authority (CA)
- STEP 2: Verification on the Microsoft CA Server
- STEP 3: Preparing the Microsoft CA Server for NSX-T Certificate Signing
- STEP 4: Create Certificate Signing Request (CSR) for the NSX-T FQDNs
- STEP 5: Signing the generated CSRs with the Microsoft Root Certificate Authority (CA)
- STEP 6: Import the CA-signed certificates into the NSX-T Manager Nodes
- STEP 7: Activate uploaded CA-signed certificates with REST API calls
- OPTIONAL: Use one single signed certificate for all NSX-T FQDNs (including the VIP)
STEP 1» Configuring a Microsoft Server to be a Root Certificate Authority 〈CA〉
Before we can start generating CSR's and signing these, we first need to have a CA server to sign the CSRs with. In this step, I am going to show you (one of many ways) how to set up a CA server that is based on Microsoft Windows 2019 Server.
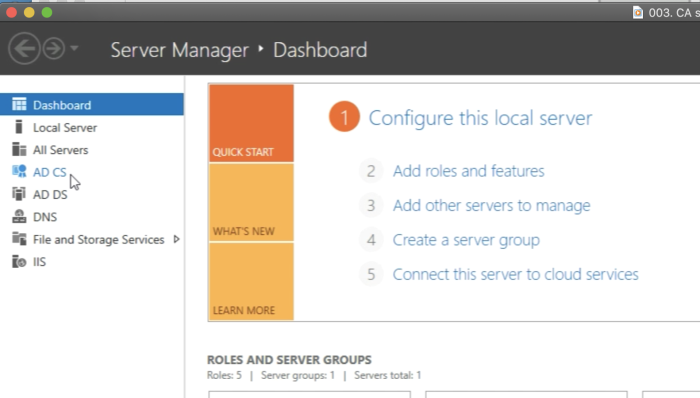
First, we click on “Add roles and features".
Leave the following settings default and click next.
Leave the following settings default and click next.
Leave the following settings default and click next.
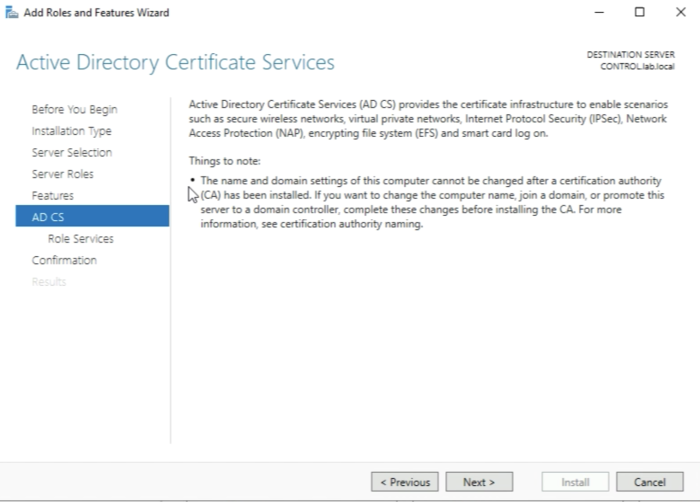
Make sure you select “Active Directory Certificate Services".
This server needs to be configured as an Active Directory Server before you install the “Active Directory Certificate Services"
When you have selected the “Active Directory Certificate Services" checkbox the installation will ask you to add some additional tools that are required as a prerequisite. Go ahead and add these features.
The “Active Directory Certificate Services" role is now selected and you can go ahead and click on next.
Leave the following settings default and click next.
Leave the following settings default and click next.
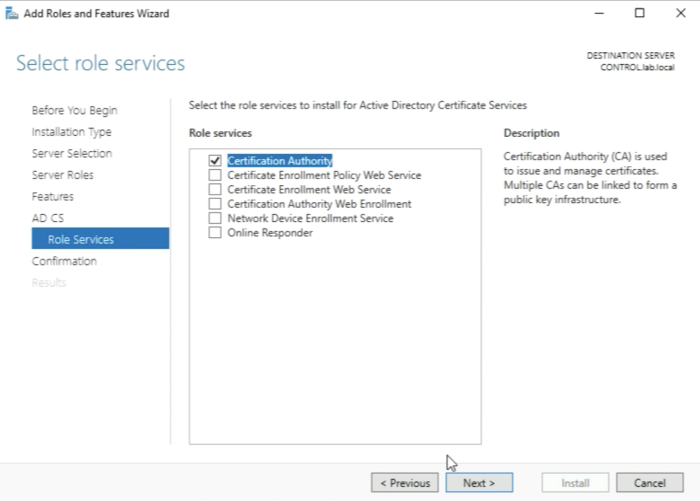
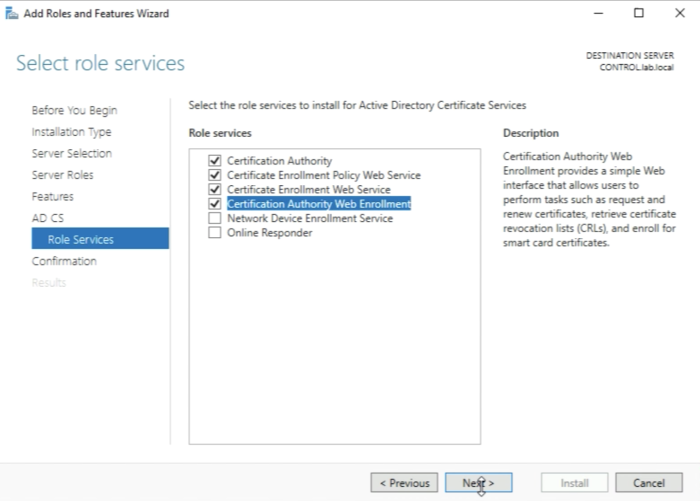
The “Certification Authority” Role will already be selected for you by default, but before you click on next you need to select additional role services.
Select the following role services:
- Certificate Enrolment Policy Web Service
- Certificate Enrolment Web Service
- Certification Authority Web Enrollment
And click next
Make sure you have installed the Microsoft IIS web server as a prerequisite.
Check the box “Restart the destination server automatically if required" Click on install.
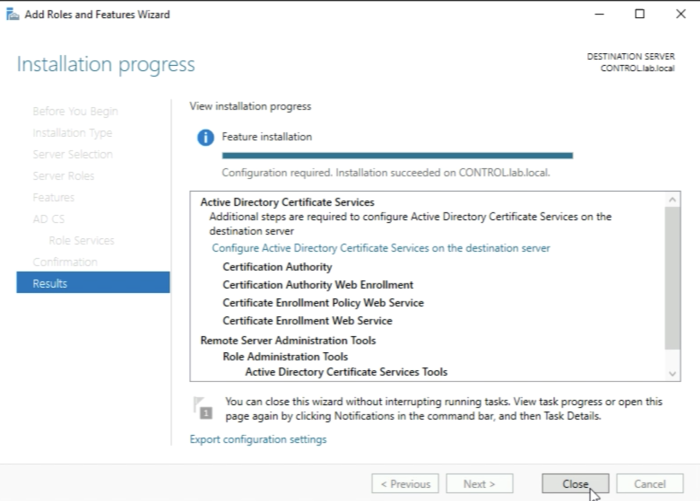
The installation process will start and will finish and then you will be able to close the window.
When the installation is done you need to do some additional "Post-deployment Configuration” so you need to look at the yellow exclamation mark in the upper right corner and click on “Configure Active Directory Certificate Services on this server”.
Leave the following settings default and click next.
Make sure the “Certification Authority” and "Certification Authority Web-Enrollment” Role Services are selected and click on Next.
These two Role Services needs to be configured first before others can be configured in a later stage.
Leave the following settings default and click next.
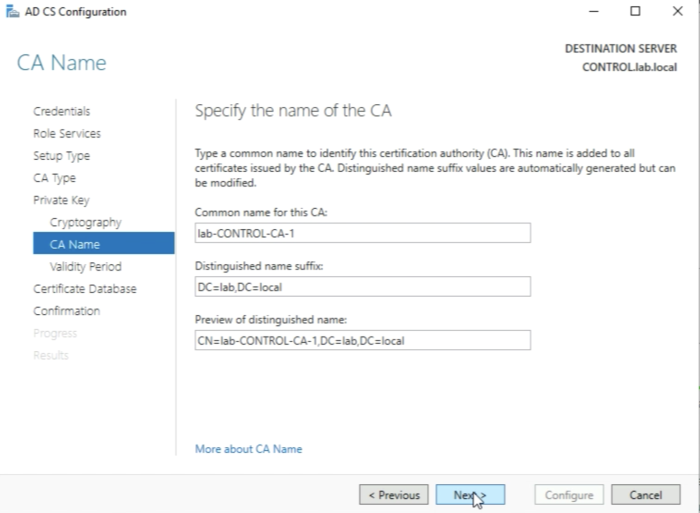
Leave the following settings default and click next.
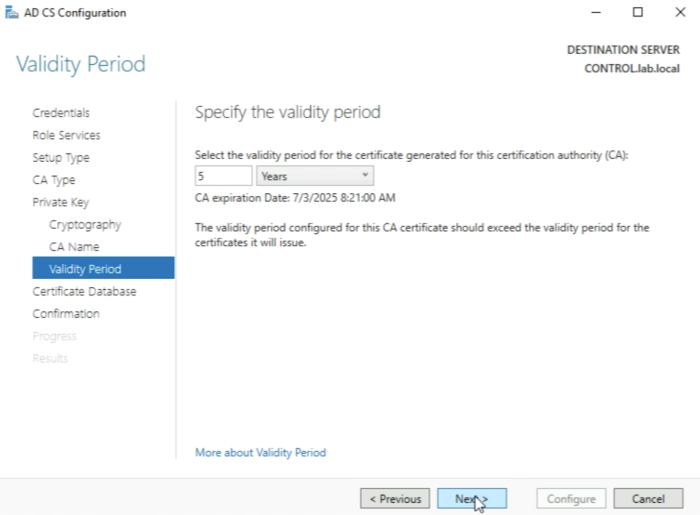
Leave the following settings default and click next. It is important that you create a private key for this new Root Certificate Authority (CA) here.
Leave the following settings default and click next.
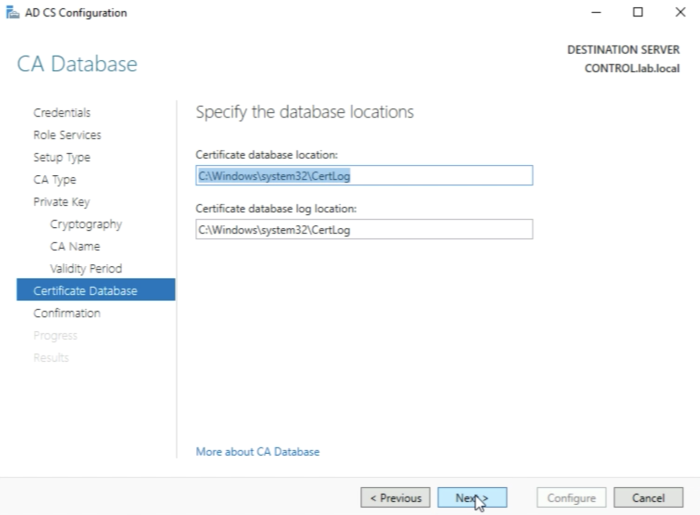
Leave the following settings default and click next.
Leave the following settings default and click next.
Leave the following settings default and click on next.
Leave the following settings default and click on Configure.
When the selected services are configured and the below messages are displaced that the Configuration is succeeded you can click on Close.
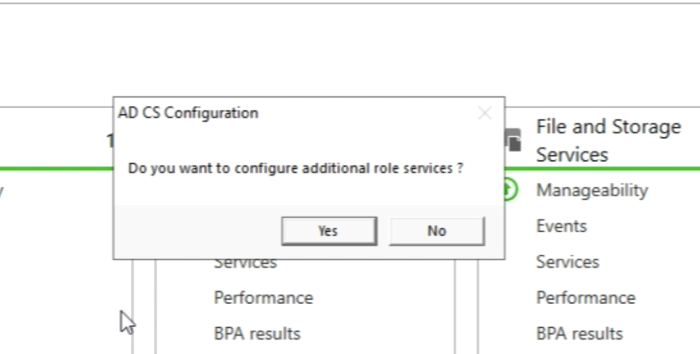
Now it’s time to configure the additional role services. SO click on “Yes” when you get the below question to configure additional role services.
Leave the following settings default and click on Next.
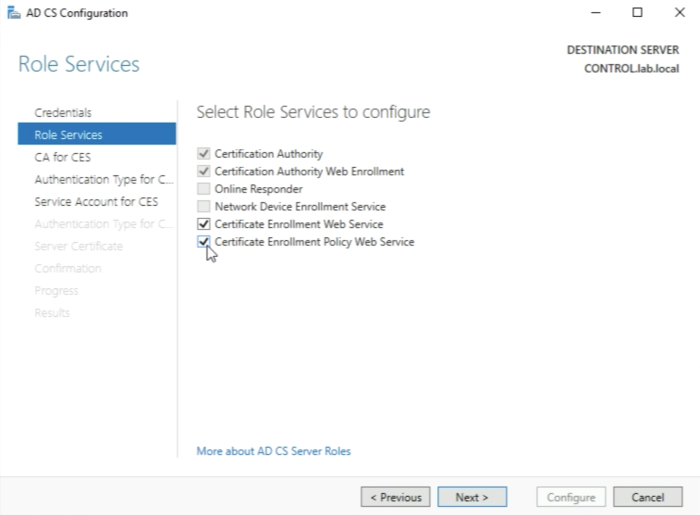
Now select to configure the following additional "Role Services":
- Certificate Enrolment Web Service
- Certificate Enrolment Policy Web Service
Leave the following settings default and click on Next.
Leave the following settings default and click on Next.
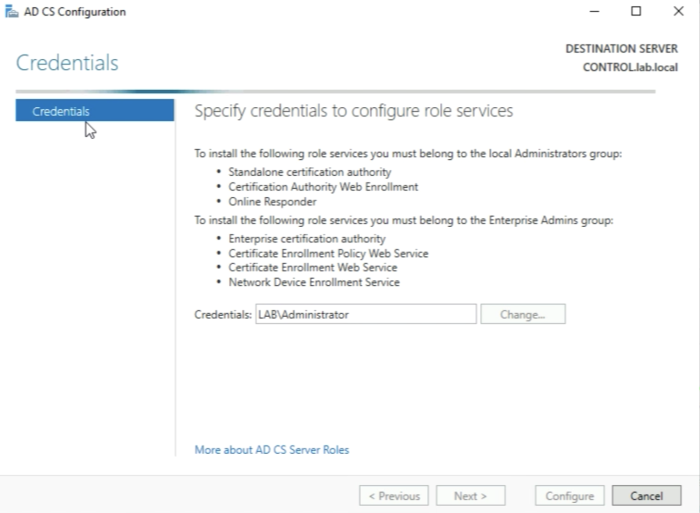
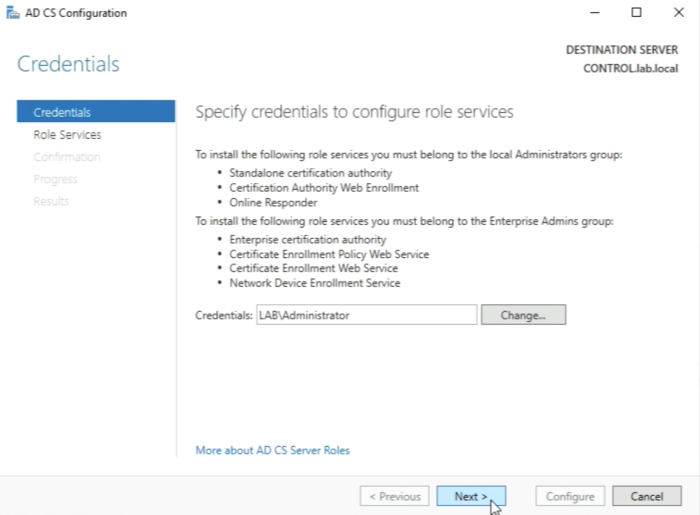
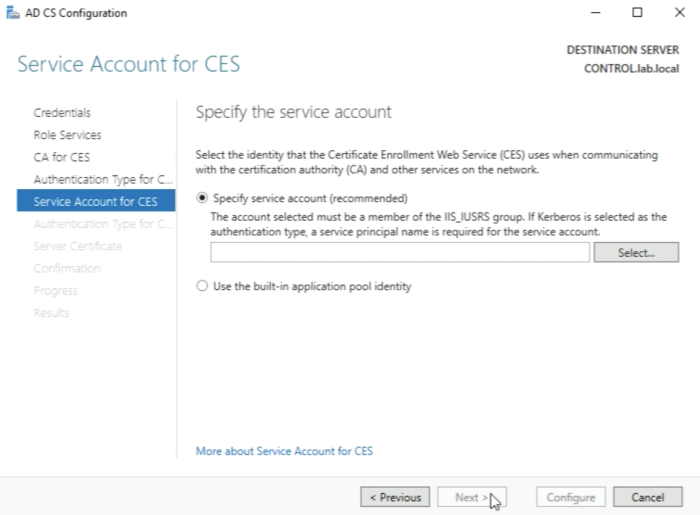
We need to specify a service account here that is a member of the IIS_IUSRS group. I currently have no account (or user) that is part of this group so I need to add this group to an account.
In order to assign the group to the account, You need to open the "Active Directory Users and Computers” Management Console.
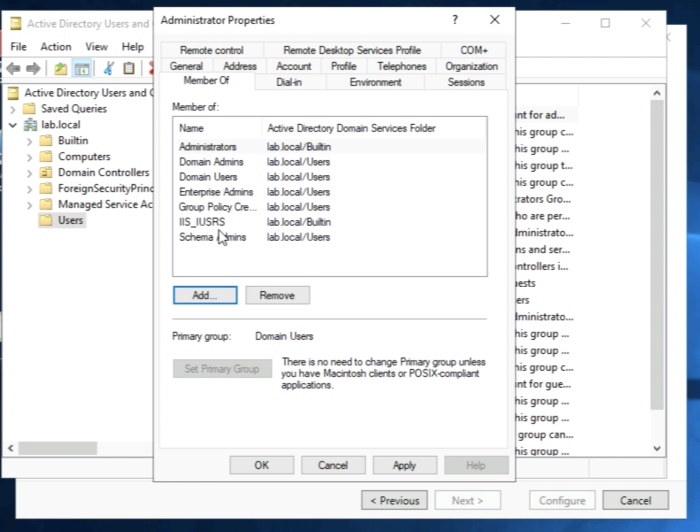
You need to select the account you want to use as a service account and go to the properties. In my case, I will select the "Administrator account".
Browse to the “Member of” tab.
Add the IIS_IUSRS group to the "Administrator" account.
Make sure the IIS_IUSRS is listed in the "Member Of" list of the account.
Now that the account has the proper rights we can click on select.
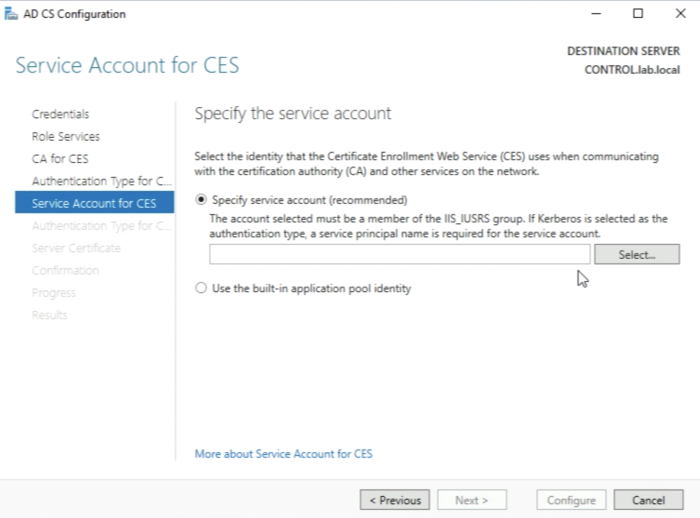
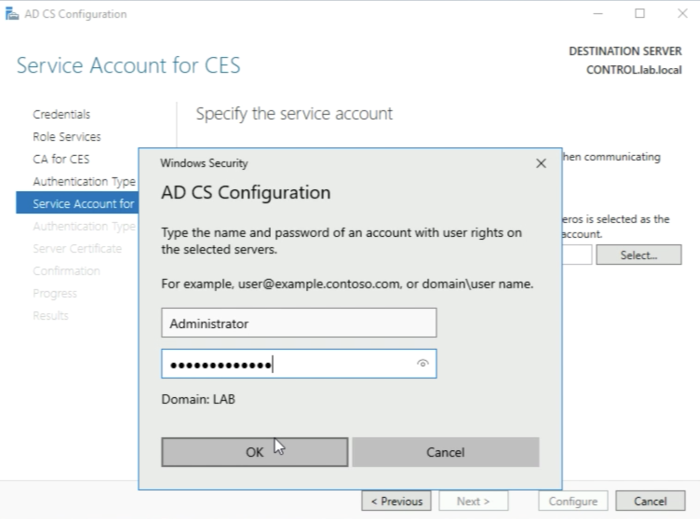
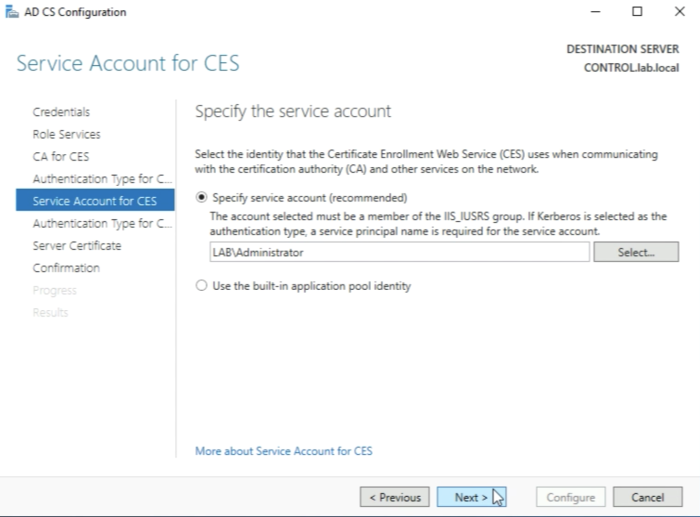
You need to type in the credentials of the service account (in my case the Administrator account) and click on “OK”.
Click on “Next” when the service account is specified.
Leave the following settings default and click on Next.
Make sure you select the “certificate" for SSL encryption first before you can click on Next.
Click on “Configure”.
When you see the message “Configuration succeed" click on Close.
Now we have installed on configured the CA Server with its underlying Roles and Services completely.
Now we can verify is the “AD CS" option appears in the Server Manager menu. You can click on it.
When you click on it you can see that the AD server is online and activated.
You should also be able to open the "Certification Authority" Management Console. You will need this later to do some additional preparation before we can start signing the CSRs for the NSX-T Manager nodes.
When you have opened the “Certification Authority" Management Console you will see the following screen.
Select the name to right-click and go to the properties.
Make sure the hash algorithm is SHA256.
Click on “View Certificate”.
You will see the information on the Root Certificate of this CA Server.
Click on the details. And click on “Copy to File” in order to export the Root Certificate to your Computer. You will need this later when you import the Root CA certificate and the signed NSX-T node certificates in NSX-T.
Click on Next.
Select the “Base-64 encoded X.509 (.CER)" File Format for the export and click Next”
Specify a valid path that you want to export the files to.
Click on Finish to complete the export of the Root Certificate files.
A message should pop up with that the export was successful. Click on OK to clone the message.
It’s always good practice to browse to the file and make sure it is really there.
You can view the content as well, as I am doing here with Notepad++.
The content of the root certificate authority certificate is displayed below.
So now we have all the prerequisites in place to start with the next step.
STEP 2» Verification on the Microsoft CA Server
Now that the CA Server and its underlying role services we need to use the web browser and browse to the following URL:
https://localhost//certsrv
Do the additional actions to access the website, this is browser-specific, I am using Google Chrome as you can see.
This confirms we can use this (web) server to sign our Certificates with.
STEP 3» Preparing the Microsoft CA Server for NSX–T Certificate Signing
Before we start we need to create a new Certificate Template with some specific settings for the NSX-T Node CA-signed certificates. So let's open the Certification Authority Management Console again. Select Certificate Templates and right-click this and select "Manage".
Select the “Web Server” Template and right-click and select "Duplicate Template”.
Go to the “Compatibility” tab and select "Windows Server 2008 R2" as the Certificate Authority Compatibility.
Just click ok on the pop-up window.
Select “Windows 7/Windows 2008 R2" as the "Certificate Recipient".
Just click ok on the pop-up window.
Go to the “Extensions” tab.
Select “Basic Constraints” and click on "Edit".
Make sure this extension is enabled by checking the box.
Go to the “General” tab and provide a new name for this cloned template. My name is NSX-T-SSL-CERT. Close the window with “OK”.
In the list of the Certificates Templates, you now see the new Template.
Select the Certificate Templates again and now select "New" and then "Certificate Template to Issue”.
Select the template you just created "NSX-T-SSL-CERT" and click ok "OK".
Now you see the new Template listed on the Certificate Templates list.
You need to make sure one more time that the hash algorithm is set to SHA256. Select the CA server and right-click and select "Properties"
Validate that that the hash algorithm is set to SHA256.
Now we have created a Certificate Template with the correct settings that we can use to sign our CSRs.
STEP 4» Create Certificate Signing Request 〈CSR〉 for the NSX–T FQDNs
In this example I am (ab)using me vCenter Server to create Certificate Signing Request for each FQDN we require in NSX-T.
You can also use another tool to generate your CSR's as long as your tool supports Subject Alternative Names (SAN) that is required for the VIP FQDN.
First, you log in to the vCenter Server.
The authenticity of host '10.203.230.5 (10.203.230.5)' can't be established.
ECDSA key fingerprint is SHA256:E076z5ftrnCpDe+S10uQpNPk7SHV4NFfwlVn0jB1zSs.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.203.230.5' (ECDSA) to the list of known hosts.
VMware vCenter Server 7.0.0.10400
Type: vCenter Server with an embedded Platform Services Controller
root@10.203.230.5’s password:
Connected to service
* List APIs: "help api list"
* List Plugins: "help pi list"
* Launch BASH: "shell"
Command>
Make sure you launch the BASH shell.
Command> shell Shell access is granted to root root@Pod-230-vCenter [ ~ ]#
Start the vCenter Server Certificate Manager.
root@Pod-230-vCenter [ ~ ]# /usr/lib/vmware-vmca/bin/certificate-manager
_ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _
* *
* *** Welcome to the vSphere 6.8 Certificate Manager *** *
* *
* -- Select Operation -- *
* *
* 1. Replace Machine SSL certificate with Custom Certificate *
* *
* 2. Replace VMCA Root certificate with Custom Signing *
* Certificate and replace all Certificates *
* *
* 3. Replace Machine SSL certificate with VMCA Certificate *
* *
* 4. Regenerate a new VMCA Root Certificate and *
* replace all certificates *
* *
* 5. Replace Solution user certificates with *
* Custom Certificate *
* NOTE: Solution user certs will be deprecated in a future *
* release of vCenter. Refer to release notes for more details.*
* *
* 6. Replace Solution user certificates with VMCA certificates *
* *
* 7. Revert last performed operation by re-publishing old *
* certificates *
* *
* 8. Reset all Certificates *
*_ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _*
Note : Use Ctrl-D to exit.
Option[1 to 8]: 1
Please provide valid SSO and VC privileged user credential to perform certificate operations.
Enter username [Administrator@vsphere.local]:
Enter password:
1. Generate Certificate Signing Request(s) and Key(s) for Machine SSL certificate
2. Import custom certificate(s) and key(s) to replace existing Machine SSL certificate
Option [1 or 2]: 1
Please provide a directory location to write the CSR(s) and PrivateKey(s) to:
Output directory path: /var/tmp/vmware/pod-230-nsxt-lm
Error in output directory path
Please see log file at /var/log/vmware/vmcad/certificate-manager.log for more information
Notice that I wanted to generate a CSR to a path that does not exist. In order to keep things clean and structured, I am going to create a separate directory for each FQDN I want to generate a CSR for.
root@Pod-230-vCenter [ ~ ]# cd /var/tmp/vmware/ root@Pod-230-vCenter [ /var/tmp/vmware ]# mkdir pod-230-nsxt-lm1 root@Pod-230-vCenter [ /var/tmp/vmware ]# mkdir pod-230-nsxt-lm2 root@Pod-230-vCenter [ /var/tmp/vmware ]# mkdir pod-230-nsxt-lm3 root@Pod-230-vCenter [ /var/tmp/vmware ]# mkdir pod-230-nsxt-lm-vip
Now let’s start the generation of our first CSR. Use the following details the generate all the CSRs for all the FQDNs you require:
| NSX-T Manager Node | Output directory path | Country | Name | Organization | OrgUnit | State | Locality | IPAddress | Hostname | |
|---|---|---|---|---|---|---|---|---|---|---|
| pod-230-nsxt-lm1 | /var/tmp/vmware/pod-230-nsxt-lm1 | NL | CA | VMware | VMware PSO | Zuid Holland | Rotterdam | 10.203.230.8 | myemail@vmware.com | pod-230-nsxt-lm1.lab.local |
| pod-230-nsxt-lm2 | /var/tmp/vmware/pod-230-nsxt-lm2 | NL | CA | VMware | VMware PSO | Zuid Holland | Rotterdam | 10.203.230.9 | myemail@vmware.com | pod-230-nsxt-lm2.lab.local |
| pod-230-nsxt-lm3 | /var/tmp/vmware/pod-230-nsxt-lm3 | NL | CA | VMware | VMware PSO | Zuid Holland | Rotterdam | 10.203.230.10 | myemail@vmware.com | pod-230-nsxt-lm3.lab.local |
| pod-230-nsxt-lm-vip | /var/tmp/vmware/pod-230-nsxt-lm-vip | NL | CA | VMware | VMware PSO | Zuid Holland | Rotterdam | 10.203.230.7 | myemail@vmware.com | pod-230-nsxt-lm-vip.lab.local pod-230-nsxt-lm1.lab.local pod-230-nsxt-lm2.lab.local pod-230-nsxt-lm3.lab.local |
This is the CSR Generating output for "pod-230-nsxt-lm1.lab.local"
CLICK ON EXPAND ===> ON THE RIGHT ===> TO SEE THE OUTPUT ===> :
root@Pod-230-vCenter [ ~ ]# /usr/lib/vmware-vmca/bin/certificate-manager
_ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _
* *
* *** Welcome to the vSphere 6.8 Certificate Manager *** *
* *
* -- Select Operation -- *
* *
* 1. Replace Machine SSL certificate with Custom Certificate *
* *
* 2. Replace VMCA Root certificate with Custom Signing *
* Certificate and replace all Certificates *
* *
* 3. Replace Machine SSL certificate with VMCA Certificate *
* *
* 4. Regenerate a new VMCA Root Certificate and *
* replace all certificates *
* *
* 5. Replace Solution user certificates with *
* Custom Certificate *
* NOTE: Solution user certs will be deprecated in a future *
* release of vCenter. Refer to release notes for more details.*
* *
* 6. Replace Solution user certificates with VMCA certificates *
* *
* 7. Revert last performed operation by re-publishing old *
* certificates *
* *
* 8. Reset all Certificates *
*_ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _*
Note : Use Ctrl-D to exit.
Option[1 to 8]: 1
Please provide valid SSO and VC privileged user credential to perform certificate operations.
Enter username [Administrator@vsphere.local]:
Enter password:
1. Generate Certificate Signing Request(s) and Key(s) for Machine SSL certificate
2. Import custom certificate(s) and key(s) to replace existing Machine SSL certificate
Option [1 or 2]: 1
Please provide a directory location to write the CSR(s) and PrivateKey(s) to:
Output directory path: /var/tmp/vmware/pod-230-nsxt-lm1
Please configure certool.cfg with proper values before proceeding to next step.
Press Enter key to skip optional parameters or use Default value.
Enter proper value for 'Country' [Default value : US] : NL
Enter proper value for 'Name' [Default value : CA] :
Enter proper value for 'Organization' [Default value : VMware] :
Enter proper value for 'OrgUnit' [Default value : VMware Engineering] : VMware PSO
Enter proper value for 'State' [Default value : California] : Zuid Holland
Enter proper value for 'Locality' [Default value : Palo Alto] : Rotterdam
Enter proper value for 'IPAddress' (Provide comma separated values for multiple IP addresses) [optional] : 10.203.230.8
Enter proper value for 'Email' [Default value : email@acme.com] : myemail@vmware.com
Enter proper value for 'Hostname' (Provide comma separated values for multiple Hostname entries) [Enter valid Fully Qualified Domain Name(FQDN), For Example : example.domain.com] : pod-230-nsxt-lm1.lab.local
Enter proper value for VMCA 'Name' :pod-230-nsxt-lm1
2020-08-16T06:05:30.959Z Running command: ['/usr/lib/vmware-vmca/bin/certool', '--genkey', '--privkey', '/var/tmp/vmware/pod-230-nsxt-lm1/vmca_issued_key.key', '--pubkey', '/tmp/pubkey.pub']
2020-08-16T06:05:31.280Z Done running command
2020-08-16T06:05:31.282Z Running command: ['/usr/lib/vmware-vmca/bin/certool', '--gencsr', '--privkey', '/var/tmp/vmware/pod-230-nsxt-lm1/vmca_issued_key.key', '--pubkey', '/tmp/pubkey.pub', '--config', '/var/tmp/vmware/certool.cfg', '--csrfile', '/var/tmp/vmware/pod-230-nsxt-lm1/vmca_issued_csr.csr']
2020-08-16T06:05:32.437Z Done running command
CSR generated at: /var/tmp/vmware/pod-230-nsxt-lm1/vmca_issued_csr.csr
1. Continue to importing Custom certificate(s) and key(s) for Machine SSL certificate
2. Exit certificate-manager
Option [1 or 2]: 2
root@Pod-240-vCenter [ ~ ]#This is the CSR Generating output for "pod-230-nsxt-lm2.lab.local"
CLICK ON EXPAND ===> ON THE RIGHT ===> TO SEE THE OUTPUT ===> :
root@Pod-230-vCenter [ ~ ]# /usr/lib/vmware-vmca/bin/certificate-manager
_ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _
* *
* *** Welcome to the vSphere 6.8 Certificate Manager *** *
* *
* -- Select Operation -- *
* *
* 1. Replace Machine SSL certificate with Custom Certificate *
* *
* 2. Replace VMCA Root certificate with Custom Signing *
* Certificate and replace all Certificates *
* *
* 3. Replace Machine SSL certificate with VMCA Certificate *
* *
* 4. Regenerate a new VMCA Root Certificate and *
* replace all certificates *
* *
* 5. Replace Solution user certificates with *
* Custom Certificate *
* NOTE: Solution user certs will be deprecated in a future *
* release of vCenter. Refer to release notes for more details.*
* *
* 6. Replace Solution user certificates with VMCA certificates *
* *
* 7. Revert last performed operation by re-publishing old *
* certificates *
* *
* 8. Reset all Certificates *
*_ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _*
Note : Use Ctrl-D to exit.
Option[1 to 8]: 1
Please provide valid SSO and VC privileged user credential to perform certificate operations.
Enter username [Administrator@vsphere.local]:
Enter password:
1. Generate Certificate Signing Request(s) and Key(s) for Machine SSL certificate
2. Import custom certificate(s) and key(s) to replace existing Machine SSL certificate
Option [1 or 2]: 1
Please provide a directory location to write the CSR(s) and PrivateKey(s) to:
Output directory path: /var/tmp/vmware/pod-230-nsxt-lm2
Please configure certool.cfg with proper values before proceeding to next step.
Press Enter key to skip optional parameters or use Default value.
Enter proper value for 'Country' [Default value : US] : NL
Enter proper value for 'Name' [Default value : CA] :
Enter proper value for 'Organization' [Default value : VMware] :
Enter proper value for 'OrgUnit' [Default value : VMware Engineering] : VMware PSO
Enter proper value for 'State' [Default value : California] : Zuid Holland
Enter proper value for 'Locality' [Default value : Palo Alto] : Rotterdam
Enter proper value for 'IPAddress' (Provide comma separated values for multiple IP addresses) [optional] : 10.203.230.9
Enter proper value for 'Email' [Default value : email@acme.com] : myemail@vmware.com
Enter proper value for 'Hostname' (Provide comma separated values for multiple Hostname entries) [Enter valid Fully Qualified Domain Name(FQDN), For Example : example.domain.com] : pod-230-nsxt-lm2.lab.local
Enter proper value for VMCA 'Name' :pod-230-nsxt-lm2
2020-08-16T06:05:30.959Z Running command: ['/usr/lib/vmware-vmca/bin/certool', '--genkey', '--privkey', '/var/tmp/vmware/pod-230-nsxt-lm2/vmca_issued_key.key', '--pubkey', '/tmp/pubkey.pub']
2020-08-16T06:05:31.280Z Done running command
2020-08-16T06:05:31.282Z Running command: ['/usr/lib/vmware-vmca/bin/certool', '--gencsr', '--privkey', '/var/tmp/vmware/pod-230-nsxt-lm2/vmca_issued_key.key', '--pubkey', '/tmp/pubkey.pub', '--config', '/var/tmp/vmware/certool.cfg', '--csrfile', '/var/tmp/vmware/pod-230-nsxt-lm2/vmca_issued_csr.csr']
2020-08-16T06:05:32.437Z Done running command
CSR generated at: /var/tmp/vmware/pod-230-nsxt-lm2/vmca_issued_csr.csr
1. Continue to importing Custom certificate(s) and key(s) for Machine SSL certificate
2. Exit certificate-manager
Option [1 or 2]: 2
root@Pod-240-vCenter [ ~ ]#This is the CSR Generating output for "pod-230-nsxt-lm3.lab.local"
CLICK ON EXPAND ===> ON THE RIGHT ===> TO SEE THE OUTPUT ===> :
root@Pod-230-vCenter [ ~ ]# /usr/lib/vmware-vmca/bin/certificate-manager
_ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _
* *
* *** Welcome to the vSphere 6.8 Certificate Manager *** *
* *
* -- Select Operation -- *
* *
* 1. Replace Machine SSL certificate with Custom Certificate *
* *
* 2. Replace VMCA Root certificate with Custom Signing *
* Certificate and replace all Certificates *
* *
* 3. Replace Machine SSL certificate with VMCA Certificate *
* *
* 4. Regenerate a new VMCA Root Certificate and *
* replace all certificates *
* *
* 5. Replace Solution user certificates with *
* Custom Certificate *
* NOTE: Solution user certs will be deprecated in a future *
* release of vCenter. Refer to release notes for more details.*
* *
* 6. Replace Solution user certificates with VMCA certificates *
* *
* 7. Revert last performed operation by re-publishing old *
* certificates *
* *
* 8. Reset all Certificates *
*_ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _*
Note : Use Ctrl-D to exit.
Option[1 to 8]: 1
Please provide valid SSO and VC privileged user credential to perform certificate operations.
Enter username [Administrator@vsphere.local]:
Enter password:
1. Generate Certificate Signing Request(s) and Key(s) for Machine SSL certificate
2. Import custom certificate(s) and key(s) to replace existing Machine SSL certificate
Option [1 or 2]: 1
Please provide a directory location to write the CSR(s) and PrivateKey(s) to:
Output directory path: /var/tmp/vmware/pod-230-nsxt-lm3
Please configure certool.cfg with proper values before proceeding to next step.
Press Enter key to skip optional parameters or use Default value.
Enter proper value for 'Country' [Default value : US] : NL
Enter proper value for 'Name' [Default value : CA] :
Enter proper value for 'Organization' [Default value : VMware] :
Enter proper value for 'OrgUnit' [Default value : VMware Engineering] : VMware PSO
Enter proper value for 'State' [Default value : California] : Zuid Holland
Enter proper value for 'Locality' [Default value : Palo Alto] : Rotterdam
Enter proper value for 'IPAddress' (Provide comma separated values for multiple IP addresses) [optional] : 10.203.230.10
Enter proper value for 'Email' [Default value : email@acme.com] : myemail@vmware.com
Enter proper value for 'Hostname' (Provide comma separated values for multiple Hostname entries) [Enter valid Fully Qualified Domain Name(FQDN), For Example : example.domain.com] : pod-230-nsxt-lm3.lab.local
Enter proper value for VMCA 'Name' :pod-230-nsxt-lm3
2020-08-16T06:05:30.959Z Running command: ['/usr/lib/vmware-vmca/bin/certool', '--genkey', '--privkey', '/var/tmp/vmware/pod-230-nsxt-lm3/vmca_issued_key.key', '--pubkey', '/tmp/pubkey.pub']
2020-08-16T06:05:31.280Z Done running command
2020-08-16T06:05:31.282Z Running command: ['/usr/lib/vmware-vmca/bin/certool', '--gencsr', '--privkey', '/var/tmp/vmware/pod-230-nsxt-lm3/vmca_issued_key.key', '--pubkey', '/tmp/pubkey.pub', '--config', '/var/tmp/vmware/certool.cfg', '--csrfile', '/var/tmp/vmware/pod-230-nsxt-lm3/vmca_issued_csr.csr']
2020-08-16T06:05:32.437Z Done running command
CSR generated at: /var/tmp/vmware/pod-230-nsxt-lm3/vmca_issued_csr.csr
1. Continue to importing Custom certificate(s) and key(s) for Machine SSL certificate
2. Exit certificate-manager
Option [1 or 2]: 2
root@Pod-240-vCenter [ ~ ]#This is the CSR Generating output for "pod-230-nsxt-lm-vip.lab.local"
The VIP FQDN CSR uses Subject Alternative Names (SAN) and this is different to the previously generated CSRs
CLICK ON EXPAND ===> ON THE RIGHT ===> TO SEE THE OUTPUT ===> :
root@Pod-230-vCenter [ ~ ]# /usr/lib/vmware-vmca/bin/certificate-manager
_ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _
* *
* *** Welcome to the vSphere 6.8 Certificate Manager *** *
* *
* -- Select Operation -- *
* *
* 1. Replace Machine SSL certificate with Custom Certificate *
* *
* 2. Replace VMCA Root certificate with Custom Signing *
* Certificate and replace all Certificates *
* *
* 3. Replace Machine SSL certificate with VMCA Certificate *
* *
* 4. Regenerate a new VMCA Root Certificate and *
* replace all certificates *
* *
* 5. Replace Solution user certificates with *
* Custom Certificate *
* NOTE: Solution user certs will be deprecated in a future *
* release of vCenter. Refer to release notes for more details.*
* *
* 6. Replace Solution user certificates with VMCA certificates *
* *
* 7. Revert last performed operation by re-publishing old *
* certificates *
* *
* 8. Reset all Certificates *
*_ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _*
Note : Use Ctrl-D to exit.
Option[1 to 8]: 1
Please provide valid SSO and VC privileged user credential to perform certificate operations.
Enter username [Administrator@vsphere.local]:
Enter password:
1. Generate Certificate Signing Request(s) and Key(s) for Machine SSL certificate
2. Import custom certificate(s) and key(s) to replace existing Machine SSL certificate
Option [1 or 2]: 1
Please provide a directory location to write the CSR(s) and PrivateKey(s) to:
Output directory path: /var/tmp/vmware/pod-230-nsxt-lm-vip
Please configure certool.cfg with proper values before proceeding to next step.
Press Enter key to skip optional parameters or use Default value.
Enter proper value for 'Country' [Default value : US] : NL
Enter proper value for 'Name' [Default value : CA] :
Enter proper value for 'Organization' [Default value : VMware] :
Enter proper value for 'OrgUnit' [Default value : VMware Engineering] : VMware PSO
Enter proper value for 'State' [Default value : California] : Zuid Holland
Enter proper value for 'Locality' [Default value : Palo Alto] : Rotterdam
Enter proper value for 'IPAddress' (Provide comma separated values for multiple IP addresses) [optional] : 10.203.230.7
Enter proper value for 'Email' [Default value : email@acme.com] : myemail@vmware.com
Enter proper value for 'Hostname' (Provide comma separated values for multiple Hostname entries) [Enter valid Fully Qualified Domain Name(FQDN), For Example : example.domain.com] : pod-230-nsxt-lm-vip.lab.local pod-230-nsxt-lm1.lab.local pod-230-nsxt-lm2.lab.local pod-230-nsxt-lm3.lab.local
Enter proper value for VMCA 'Name' :pod-230-nsxt-lm-vip
2020-08-16T06:05:30.959Z Running command: ['/usr/lib/vmware-vmca/bin/certool', '--genkey', '--privkey', '/var/tmp/vmware/pod-230-nsxt-lm-vip/vmca_issued_key.key', '--pubkey', '/tmp/pubkey.pub']
2020-08-16T06:05:31.280Z Done running command
2020-08-16T06:05:31.282Z Running command: ['/usr/lib/vmware-vmca/bin/certool', '--gencsr', '--privkey', '/var/tmp/vmware/pod-230-nsxt-lm-vip/vmca_issued_key.key', '--pubkey', '/tmp/pubkey.pub', '--config', '/var/tmp/vmware/certool.cfg', '--csrfile', '/var/tmp/vmware/pod-230-nsxt-lm-vip/vmca_issued_csr.csr']
2020-08-16T06:05:32.437Z Done running command
CSR generated at: /var/tmp/vmware/pod-230-nsxt-lm-vip/vmca_issued_csr.csr
1. Continue to importing Custom certificate(s) and key(s) for Machine SSL certificate
2. Exit certificate-manager
Option [1 or 2]: 2
root@Pod-240-vCenter [ ~ ]#Now that all the CSRs are generated lets to a quick check if they are really there.
root@Pod-240-vCenter [ ~ ]# cd /var/tmp/vmware/ root@Pod-240-vCenter [ /var/tmp/vmware ]# ls -l total 100 drwxr-xr-x 3 root root 4096 Aug 6 22:51 analytics -rw-r--r-- 1 root root 203 Aug 16 06:05 certool.cfg drwxr-xr-x 3 root root 4096 Aug 6 22:51 cis-license drwxr-xr-x 3 eam root 4096 Aug 6 22:55 eam -rw-r--r-- 1 root root 241 Aug 16 06:05 hvc.cfg -rw-r--r-- 1 root root 245 Aug 16 06:05 machine.cfg -rw-r--r-- 1 root root 225 Aug 16 06:05 MACHINE_SSL_CERT.cfg -rw------- 1 root root 1473 Aug 16 06:00 old_machine_ssl.crt drwxr-xr-x 2 root root 4096 Aug 16 06:05 pod-230-nsxt-lm1 drwxr-xr-x 2 root root 4096 Aug 16 05:59 pod-230-nsxt-lm2 drwxr-xr-x 2 root root 4096 Aug 16 05:59 pod-230-nsxt-lm3 -rw-r--r-- 1 root root 104 Aug 16 06:05 root.cfg -rw-r--r-- 1 root root 1506 Aug 6 22:55 tmp24v6efrh -rw------- 1 root root 1506 Aug 6 22:55 tmp755um1mj -rw------- 1 root root 1473 Aug 6 22:55 tmpa4vd8mkx -rw------- 1 root root 1595 Aug 6 22:59 tmpny4hffel -rw------- 1 root root 1595 Aug 6 22:55 tmpsieshzoz -rw------- 1 root root 1705 Aug 6 22:59 tmpsqul8kjb -rw------- 1 root root 1595 Aug 6 22:58 tmpsxbh6427 -rw------- 1 root root 1705 Aug 6 22:58 tmpveqb1z4q -rw------- 1 root root 1705 Aug 6 22:55 tmpy_74bryf -rw-r--r-- 1 root root 242 Aug 16 06:05 vpxd.cfg -rw-r--r-- 1 root root 252 Aug 16 06:05 vpxd-extension.cfg -rw-r--r-- 1 root root 255 Aug 16 06:05 vsphere-webclient.cfg -rw-r--r-- 1 root root 203 Aug 16 06:05 wcp.cfg root@Pod-240-vCenter [ /var/tmp/vmware ]# cd pod-230-nsxt-lm1pod-230-nsxt-lm1 bash: cd: pod-230-nsxt-lm1pod-230-nsxt-lm1: No such file or directory root@Pod-240-vCenter [ /var/tmp/vmware ]# cd pod-230-nsxt-lm1 root@Pod-240-vCenter [ /var/tmp/vmware/pod-230-nsxt-lm1 ]# ls -l total 8 -rw-r--r-- 1 root root 1166 Aug 16 06:05 vmca_issued_csr.csr -rw-r--r-- 1 root root 1703 Aug 16 06:05 vmca_issued_key.key root@Pod-240-vCenter [ /var/tmp/vmware/pod-230-nsxt-lm1 ]#
You now need to transfer the CSRs to your Computer in order to import them the proper way to NSX-T. I am using WinSCP for file transfers.
Before we can log in to the vCenter Server with WinSCP we first need to edit a few advanced settings in WinSCP.
Go to the Advanced settings of this session you just saved.
Select “SFTP” in the Environment menu tree. And populate the “SFTP server” field with "shell _usr_libexec/sftp-server Click on “OK”
Click on “Login”.
You will get a message and you can click on "continue".
You are authenticated.
And you are in …
Now to keep things Clean on my computer I am going to create a separate directory for the CSRs I am going to transfer from the vCenter Server to my computer.
After the fire transfer is done it should look like this inside WinSCP.
After the fire transfer is done it should look like this inside your computer.
Now you can verify if all the required files are there. You should see the following files inside each directory.
STEP 5» Signing the generated CSRs with the Microsoft Root Certificate Authority 〈CA〉
Now you are ready to sign the CSRs with your brand new Microsoft CA Server.
Browse to the website:
https://localhost/certsrv
Do this on your CA Server.
Click on Submit an“advanced certificate request".
In the “Saved Request” field we need to copy the content of the CSR that we generated on the vCenter Server inside this textbox.
Make sure you open the .csr file in a text editor.
This is the signing for the first FQDN: pod-230-nsxt-lm1, but the other CSR signing will be done using the same process.
'Copy the content of the .csr file
Paste the content of the .csr file in the textbox.
Select the Certificate Template you created in a previous step, NSX-T-SSL-CERT.
And click on “Next”.
I have created a separate folder to download the "signed" certificates to on the computer, to use for the import later on the NSX-T Manager Nodes.
When you clicked on “Submit” you will be able to "Download the certificate" and you need to do this in the “Base 64 encoded” format.
Give your certificate a name and save this in the right directory.
Also save the “certificate chain" by downloading it in the "Base 64 encoded" format.
Give your certificate a name and save this in the right directory.
When you are finished with the first FQDN you can click on home.
Now you can restart the process again for the remaining FQDN CSRs.
You can do a verification when you open the Certificate Authority Management Console.
Select the “Issued Certificates" on the right menu to verify all your signed certificates.
A good practice is to look up the "root" certificate on your computer.
And rename it so it is clear that this is the "root" CA Certificate.
Also, create a separate folder for the root certificate and place the root certificate in there.
At this point, you should have a clean folder structure with all your CSRs, the signed CSRs, and the Root Certificate of your Certificate Authority.
STEP 6» Import the CA–signed certificates into the NSX–T Manager Nodes
You can import all certificates by browsing to the VIP FQDN of your NSX-T Manager Cluster. In my case this is
https://pod-230-nsxt-lm-vip.lab.local
Log in to the NSX-T Manager.
Browse to “System”.
Go to Settings => Certificates.
First you need to import the root certificate of out Microsoft Certificate Authority Server.
You can import the root certificate using the browse button.
And you select the root certificate file.
Make sure the “Service Certificate" is set to "No". And click “Import”.
In the overview, you see that the CA certificate is now imported.
Now we are going to import the FQDN signed Certificates.
Specify the “name”. I used the first part of the full FQDN. Also, type in the same name in the description field,. This is optional. Make sure the “Service Certificate" is set to "No".
The certificate Contents need to be imported using the full chain. So we start with the Signed Certificate and we end with the Root Certificate.
The best way is to open a blank notepad for all signed certificates.
Open the Base64 Certificate with Notepad++.
'Copy the output of the Certificate.
Paste the Certificate into a blank text file.
Open the root certificate into Notepad++.
'Copy the content of the root certificate.
And paste this behind the content of the signed FQDN Certificate.
The order of the certificates is important as you need BOTH certificates imported for the FQDN certificate imports.
—–BEGIN CERTIFICATE—– NSX-T FQDN Node Certificate —–END CERTIFICATE—– —–BEGIN CERTIFICATE—– CA Root Certificate —–END CERTIFICATE—–
If you have a subordinate CA:
—–BEGIN CERTIFICATE—– NSX-T FQDN Node Certificate —–END CERTIFICATE—– —–BEGIN CERTIFICATE—– Subordinate CA Certificate —–END CERTIFICATE—– —–BEGIN CERTIFICATE—– CA Root Certificate —–END CERTIFICATE—–
An example of this is given in the figure below.
Paste in the content of the signed certificate including the root certificate into the Certificate Contents field.
Click browse to import the “Private Key" that belongs to the signed certificate file.
Select the .key file.
Make sure you repeat this with all FQDNs so it will be easy to paste the content in the “Certificate Contents” field for the import of the remaining FQDNs. Eventually, you will have all the signed certificates imported for all FQDNs.
Now all the signed certificates for all FQDNs and the Root Certificate should be imported.
STEP 7» Activate uploaded CA–signed certificates with REST API calls
In order to “activate” the uploaded certificates, you need to do this with REST API calls. I used the Postman application to do this.
My good friend Rutger Blom has written a very good blog article using PostMan with NSX-T here.
In order to start, we need to create a new request.
Configure the authorization by choosing "Basic Auth".
Type in the NSX-T credentials.
In order to juicily test if the REST API calls are working properly I used the following call:
'GET https://pod-230-nsxt-lm-vip>/api/v1/cluster/status
We can see that the GET request wat not successful and it gives you a hint that the SSL certificates are being blocked.
Go to File and select Settings in the menu of the Postman application.
You can see that by default the "SSL certificate verification" is set to "ON".
Make sure the "SSL certificate verification" is set to "OFF".
Now when we execute out test REST API call again we can see a STATUS: 200 OK, and some JSON code with information about the NSX-T Cluster.
In order to “activate” the new certificates, we need to collect the certificate ID’s from the GUI as these are required to refer to the certificates during the activation process.
Before we are going to do the actual activation we are going to test the quality of the certificate first. We do this by executing the following REST API call:
'GET https://pod-230-nsxt-lmX/api/v1/trust-management/certificates/<certificate-id>?action=validate
An example of this is given in the figure below. You can see that you will get an error.
NSX-T 3.0 added Certificate Revocation List (CRL) checking when applying a certificate to a Manager node/cluster. If the CRL check cannot be performed, the certificate cannot be applied to a Manager node or cluster.
You can turn this off by following the content of this VMware KB (78794).
First, we need to execute the following TEST API call to get the existing configuration setting around the CRL checking.
'GET https://pod-230-nsxt-lm-vip>/api/v1/global-configs/SecurityGlobalConfig
When you take the JSON config and change the following line:
crl_checking_enabled” : true,
To
crl_checking_enabled” : false,
Make sure you use the full JSON code output and only change "true" to "false”.
Execute the REST API call.
Restart the validation of the Certificate again.
You should get a “status” : “OK" back from the call and a Status: 200 OK.
Repeat this process for all certificates for all FQDNs.
Now that all the certificates are validated and are "OK" we can start the process of the actual activation of these certificates. We do this with the following REST API calls:
| FQDN | Action | API call | NSX-T Manager node | Certificate ID |
|---|---|---|---|---|
| pod-230-nsxt-lm1.lab.local | POST | https://pod-230-nsxt-lm1/api/v1/node/services/http?action=apply_certificate&certificate_id=<certificate-id> |
pod-230-nsxt-lm1 | Get from NSX-T GUI |
| pod-230-nsxt-lm2.lab.local | POST | https://pod-230-nsxt-lm2/api/v1/node/services/http?action=apply_certificate&certificate_id=<certificate-id> |
pod-230-nsxt-lm2 | Get from NSX-T GUI |
| pod-230-nsxt-lm3.lab.local | POST | https://pod-230-nsxt-lm3/api/v1/node/services/http?action=apply_certificate&certificate_id=<certificate-id> |
pod-230-nsxt-lm3 | Get from NSX-T GUI |
| pod-230-nsxt-lm-vip.lab.local | POST | https://pod-230-nsxt-lm-vip/api/v1/cluster/api-certificate?action=set_cluster_certificate&certificate_id=<certificate-id |
pod-230-nsxt-lm-vip | Get from NSX-T GUI |
An example of the first manager is shown in the figure below.
Make sure you 'copy the certificate ID that is retrieved fomr the NSX-T GUI.
Complete the full REST API URL and click on Send.
Repeat this process for all certificates for all FQDNs, except for the VIP FQDN.
Make sure you use the corresponding FQDN of the NSX-T Manager is used in the REST API call for what the certificate is activated for.
For the VIP cert, the REST API call is a little bit different like I mentioned in the table above. An example of this is given in the figure below.
Make sure you 'copy the Certificate ID from the NSX-T GUI for the VIP FQDN.
Execute the REST API call.
Now that the certificates are all activated you can use a browser to browse to the URL using the FQDN that was used the CSR. Notice age little lock in front of the URL.
When you click on the lock you can see the message that the connection is secure and that the certificate is valid for the VIP FQDN.
You will get the same result when you go to the URL of one of the NSX-T Manager nodes directly.
When you click on the Certificate you can look at other certificate details in the General Tab where you can see the Root CA that signed the certificate.
When you click on the “Details" tab you can see more details about the certificate.
And finally, you can view the "Certification Path" by going to the "Certification Path” tab.
You have reached the end of this article, and I know it was a long one, but I hope you have learned something so that you can replicate this in your test of the production environment.
OPTIONAL» Use one single signed certificate for all NSX-T FQDNs - including the VIP
In the steps above I have shown you how to generate CSRs for all separate FQDNs of all separate NSX-T Manager Nodes and the NSX-T VIP address.
One of my US-based colleagues (Michael (Cobi) Fye) asked me the question if he could also use ONE SINGLE CSR only with all the Subject Alternative Names (SANs) and get this CSR signed by the (root) Certificate Authority (CA) and use this single-signed Certificate for all of the Manager Nodes including the NSX-T VIP address.
I did not test this, but fortunately, he did. The steps are summarized below that Michael did:
- Generate the CSR (only using Subject Alternative Names)(with OpenSSL
- The output is provided in an example below
- Get the CSR signed by the (root) Certificate Authority (CA)
- Import the (root) Certificate into the NSX-T Manager(s)
- Import the CA-signed certificates into the NSX-T Manager Nodes
- Like I am doing in Step 6
- Activate uploaded CA-signed certificates with REST API calls
- Like I am doing in Step 7
- Only now you are only using one single certificate with the same Certificate ID using 4 different API calls (3 x for the NSX-T Manager Nodes, and 1 x for the VIP address)
After performing these steps Michael confirmed this was working. Below you will see the request Michael used to generate the CSR for this single-cert-solution.
Using OpenSSL to generate a single CSR
The commands used to generate the CSR using OpenSSL:
set remotehost=pod-230-nsxt-lm-vip cd x:\certs\%remotehost% openssl req -new -nodes -out %remotehost%.csr -keyout %remotehost%-orig.key -config %remotehost%.cfg openssl rsa -in %remotehost%-orig.key -out %remotehost%.key
The config file that was used to generate the CSR using OpenSSL:
[ req ] default_bits = 2048 default_keyfile = rui.key distinguished_name = req_distinguished_name encrypt_key = no prompt = no string_mask = nombstr req_extensions = v3_req [ v3_req ] basicConstraints = CA:TRUE keyUsage = digitalSignature, keyEncipherment, dataEncipherment extendedKeyUsage = serverAuth, clientAuth subjectAltName = DNS:pod-230-nsxt-lm-vip, DNS:pod-230-nsxt-lm-vip.lab.local, DNS:pod-230-nsxt-lm1, DNS:pod-230-nsxt-lm1.lab.local, DNS:pod-230-nsxt-lm2, DNS:pod-230-nsxt-lm2.lab.local, DNS:pod-230-nsxt-lm3, DNS:pod-230-nsxt-lm3.lab.local [ req_distinguished_name ] countryName = NL stateOrProvinceName = Zuid Holland localityName = Washington 0.organizationName = CA organizationalUnitName = VMware PSO commonName = pod-230-nsxt-lm-vip.lab.local
The verification when the CSR was imported into the Certificate Authority for signing:
I have used my own values in order to reflect the same parameters that I used in this article, just to keep everything in line and easier to understand.
CSR Information: Common Name: pod-230-nsxt-lm-vip.lab.local Subject Alternative Names: pod-230-nsxt-lm-vip, pod-230-nsxt-lm-vip.lab.local, pod-230-nsxt-lm1, pod-230-nsxt-lm1.lab.local, pod-230-nsxt-lm2, pod-230-nsxt-lm2.lab.local, pod-230-nsxt-lm3, pod-230-nsxt-lm3.lab.local Organization: CA Organization Unit: VMware PSO Locality: Washington State: Zuid Holland Country: NL
YouTube Video
In the video below I will show you how to perform all the steps to replace your self-signed certificates for CA-signed certificates taking the same steps described in this wiki article.
Technical Reviews
This article was technically reviewed by the following SME's:
| Name | LinkedIn Profile |
|---|---|
| Bode Fatona | Link |
I am always trying to improve the quality of my articles so if you see any errors, mistakes in this article or you have suggestions for improvement, please contact me and I will fix this.