RPF setting and NSX Edges in ECMP mode: Difference between revisions
No edit summary |
No edit summary |
||
| (12 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
RPF stands for Route Path Filtering. | |||
When RPF is enabled, the Edge only forwards packets if they are received on the same interface that would be used to forward the traffic to the source of the packet. If the route to the source address of the packet is through a different interface than the one it is received on, the packet is dropped. | |||
{{important|With this article, I am not saying that disabling RPF is a recommendation, I am simply saying that when you have a topology where asynchronous routing is accepted in your design, you have no other choice than to change the setting from enabled to loose or disabled.}} | {{important|With this article, I am not saying that disabling RPF is a recommendation, I am simply saying that when you have a topology where asynchronous routing is accepted in your design, you have no other choice than to change the setting from enabled to loose or disabled.}} | ||
== | == What is ECMP == | ||
In case of ECMP networks are reachable through multiple paths/interfaces, and the routing updates are received through multiple paths. | In case of ECMP networks are reachable through multiple paths/interfaces, and the routing updates are received through multiple paths. | ||
| Line 20: | Line 17: | ||
Because asymmetric routing and traffic data paths can occur when we go for the ECMP deployment model you should set the RPF feature to either loose or disable it completely. | Because asymmetric routing and traffic data paths can occur when we go for the ECMP deployment model you should set the RPF feature to either loose or disable it completely. | ||
==Disable RPF== | == Disable RPF == | ||
Another thing that should be done when deploying NSX Edges in ECMP is that the (local) Edge firewall should be disabled. | Another thing that should be done when deploying NSX Edges in ECMP is that the (local) Edge firewall should be disabled. | ||
The “disable” firewall action is documented very well, but the RPF setting is not. | The “disable” firewall action is documented very well, but the RPF setting is not. | ||
== Other Sources == | |||
{{important|With this article, I am not saying that disabling RPF is a recommendation, I am simply saying that when you have a topology where asynchronous routing is accepted in your design, you have no other choice than to change the setting from enabled to loose or disabled.}} | {{important|With this article, I am not saying that disabling RPF is a recommendation, I am simply saying that when you have a topology where asynchronous routing is accepted in your design, you have no other choice than to change the setting from enabled to loose or disabled.}} | ||
=== Bayu Wibo === | |||
Bayu Wibowo came to the same conclusion [https://communities.vmware.com/thread/581351 here] but does not really explain the reasoning behind this, and this article tries to explain this. | Bayu Wibowo came to the same conclusion [https://communities.vmware.com/thread/581351 here] but does not really explain the reasoning behind this, and this article tries to explain this. | ||
=== Livefire === | |||
In [https://www.livefire.solutions/nsx/nsx-edge-internal-interface-reachability-failure/ this Livefire link], VMware recommends that this RPF “security” feature should be enabled because RPF can be a desirable security feature filtering traffic that should not originate from certain networks. | In [https://www.livefire.solutions/nsx/nsx-edge-internal-interface-reachability-failure/ this Livefire link], VMware recommends that this RPF “security” feature should be enabled because RPF can be a desirable security feature filtering traffic that should not originate from certain networks. | ||
But when using ECMP this is out of the question that we should NOT leave it enabled. | But when using ECMP this is out of the question that we should NOT leave it enabled. | ||
[[Category: NSX]] | |||
[[Category:Networking]] | |||
[[Category:VMware]] | |||
Latest revision as of 17:35, 19 January 2024
RPF stands for Route Path Filtering.
When RPF is enabled, the Edge only forwards packets if they are received on the same interface that would be used to forward the traffic to the source of the packet. If the route to the source address of the packet is through a different interface than the one it is received on, the packet is dropped.
With this article, I am not saying that disabling RPF is a recommendation, I am simply saying that when you have a topology where asynchronous routing is accepted in your design, you have no other choice than to change the setting from enabled to loose or disabled.
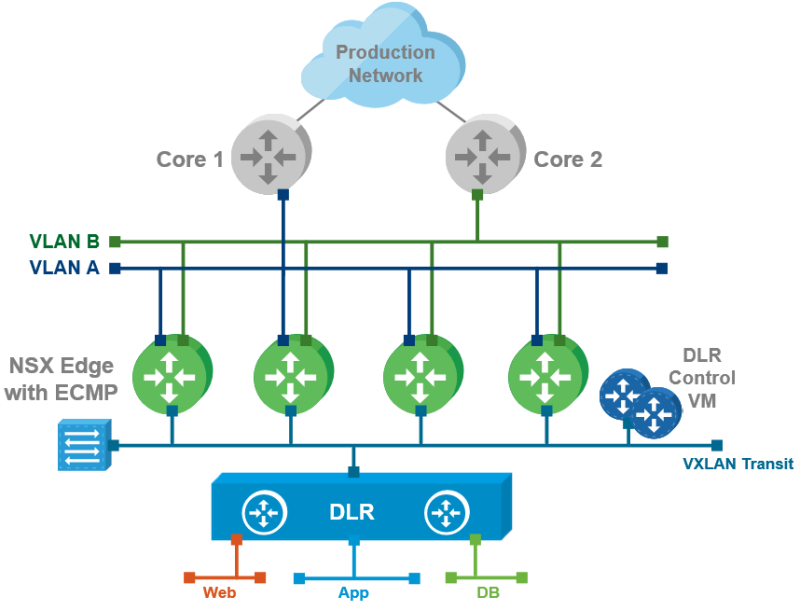
What is ECMP
In case of ECMP networks are reachable through multiple paths/interfaces, and the routing updates are received through multiple paths.
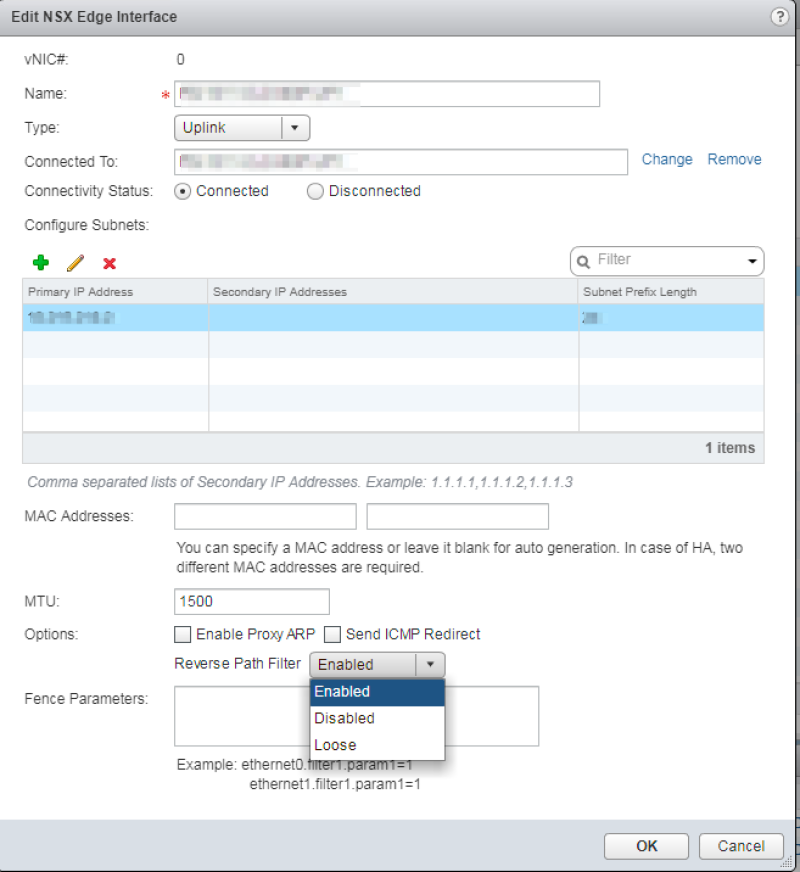
The NSX Edge has the RPF feature enabled by default. The other two options that can be chosen are “Loose” and “Disabled”.
Because asymmetric routing and traffic data paths can occur when we go for the ECMP deployment model you should set the RPF feature to either loose or disable it completely.
Disable RPF
Another thing that should be done when deploying NSX Edges in ECMP is that the (local) Edge firewall should be disabled. The “disable” firewall action is documented very well, but the RPF setting is not.
Other Sources
With this article, I am not saying that disabling RPF is a recommendation, I am simply saying that when you have a topology where asynchronous routing is accepted in your design, you have no other choice than to change the setting from enabled to loose or disabled.
Bayu Wibo
Bayu Wibowo came to the same conclusion here but does not really explain the reasoning behind this, and this article tries to explain this.
Livefire
In this Livefire link, VMware recommends that this RPF “security” feature should be enabled because RPF can be a desirable security feature filtering traffic that should not originate from certain networks. But when using ECMP this is out of the question that we should NOT leave it enabled.