NSX Inventory
The NSX Inventory contains objects that are used to support the network and security services provided by NSX.
Using Groups and Services
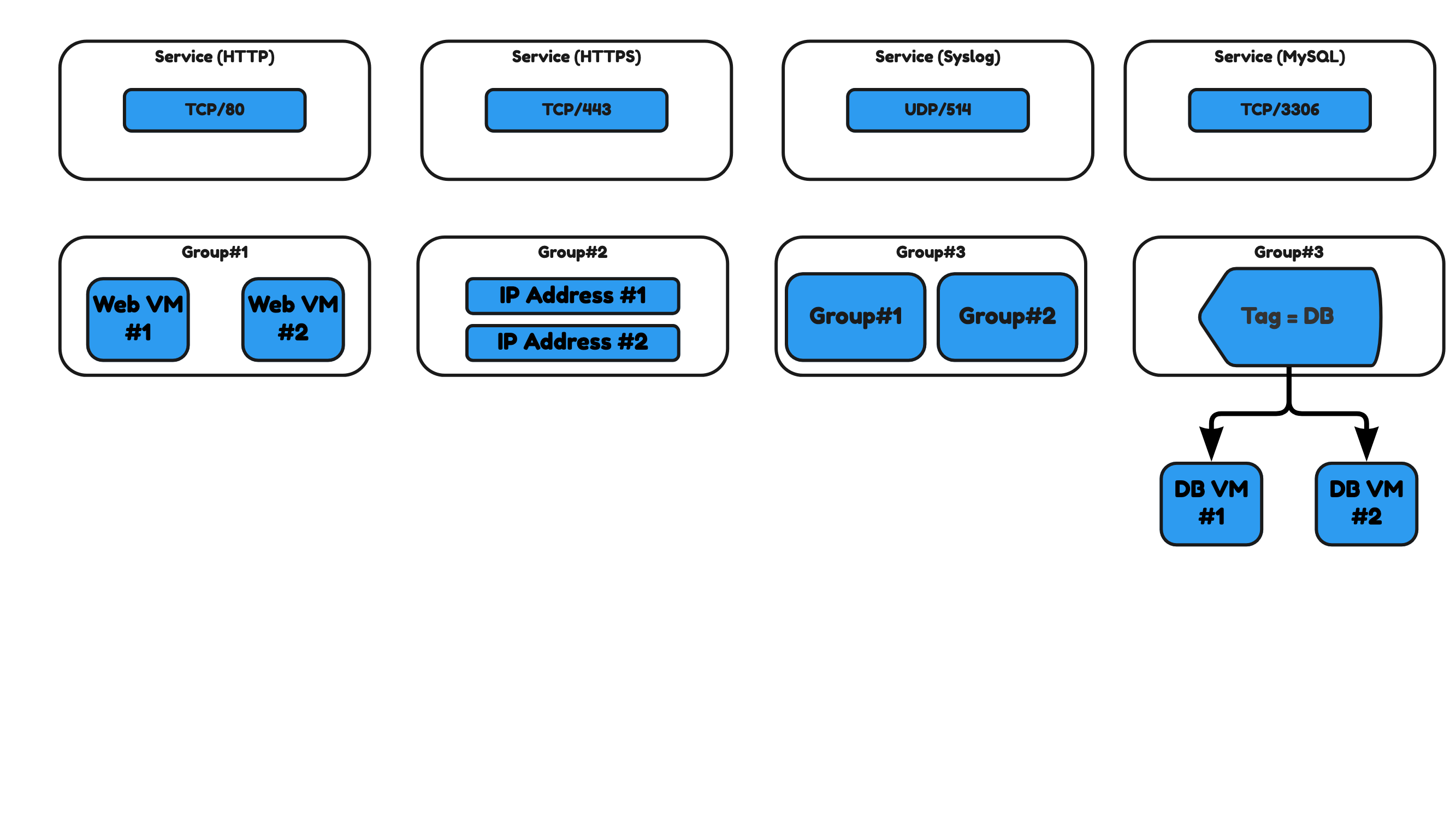
A group is a collection of objects that can be used for grouping purposes. You can create groups with different types of objects like:
- A Group with multiple selected Virtual Machines.
- A Group of multiple selected IP addresses.
- A Group of multiple selected (nested) other groups.
- A group that makes objects part of that group based on a tag.
A service is a combination of a protocol and port. An example of this is that TCP port 80 will form the HTTP Service and TCP port 443 will form the HTTPS Service. NSX has several predefined Services that can be used when you configure Firewall Rules. When a service that you want to use is not pre-configured you can create a custom service.
Figure 32 has some examples of groups and services.
Figure 32:
Using Context Profiles
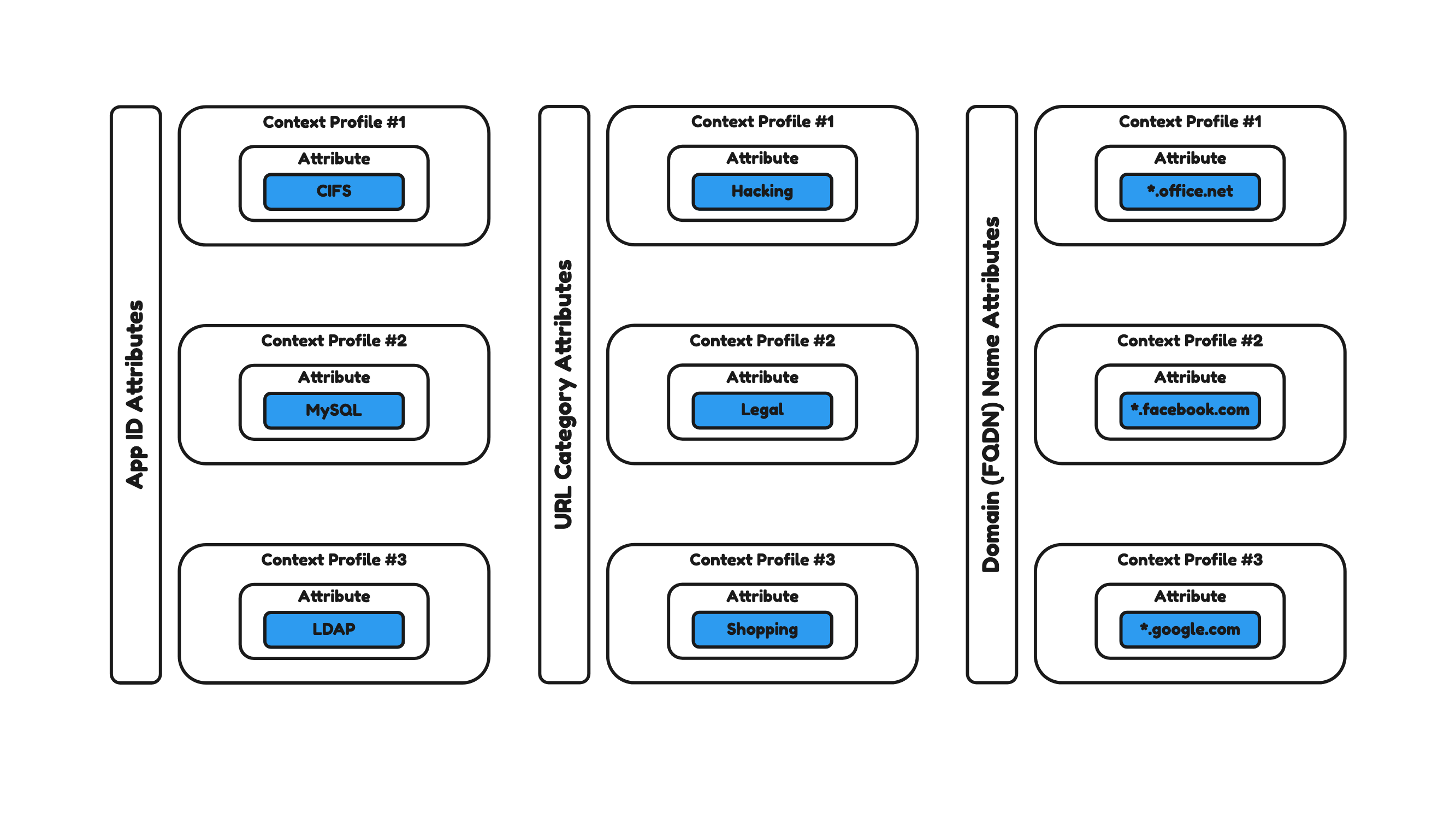
In a Context Profile, you can enforce a specific security policy based on actual data. The different attributes that can be used are App ID, URL Category, and Domain (FQDN) Name attributes.
When a Context Profile with an App ID is selected the firewall will look inside the packet to verify if the traffic matches the traffic type that is processed. Typically, MySQL uses TCP port 3306. Without the Context Profile and App ID Attribute the firewall will only decide based on the TCP and port 3306. With the Context Profile and App ID Attribute the firewall will decide based on the traffic type. If for whatever reason MySQL is using a different port, the traffic will still be subject to the processing of the firewall.
The URL Category is used to block or allow URLs based on a specific category. If you want to block all Shopping websites for example you can use the URL Category attribute Shopping to block websites like Amazon or eBay for example.
With the Domain (FQDN) Name attribute, you can even block or allow specific URLs based on their FQDN.
Figure 33 shows an example of different Context Profiles with different attribute types.
Figure 33:
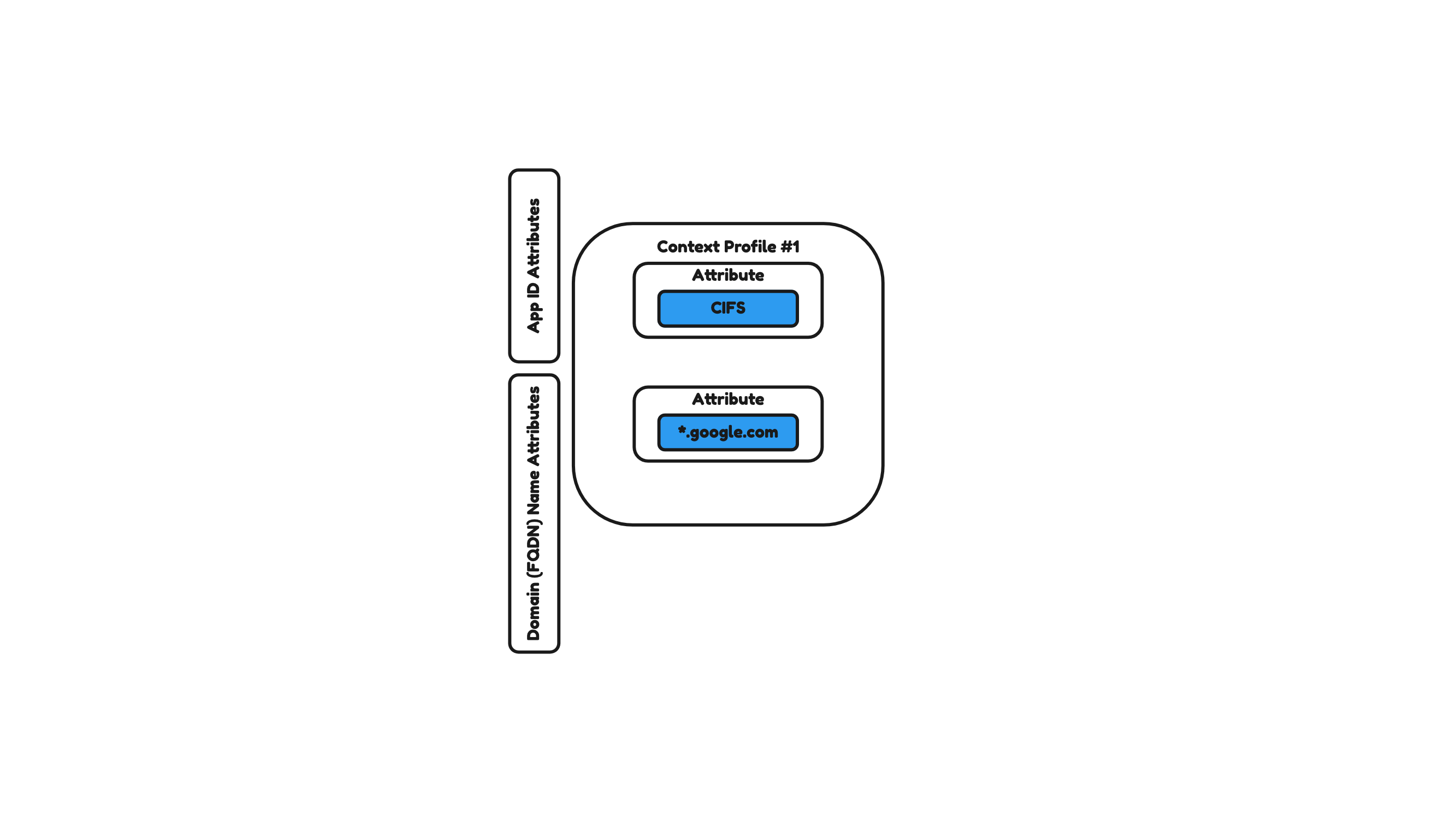
Using Layer 7 Access Profiles
An L7 Access Profile contains more than one entry with a combination of different attribute types (Figure 34) like an App ID, a URL category, a custom URL, and a URL reputation for example. This is typically used for URL filtering in a Gateway Firewall rule, in the profile field.
Figure 34:
Use a Tag and use the tag to make a VM member of a Group based on that tag
Virtual Machines can be part of a group based on a Tag. When you have a group of Web Servers and you want this group to be part of a Group based on a tag, you can provide a Tag (with a specific name) to each of these Web Servers. You also need to create a group with the condition that all Virtual Machines with this tag need to be part of this group.
With this, you can create your security policy (firewall rules) using this group, and the next time you have a new Web Server that needs to use this exact same security policy you can just Tag it and make it a member of the Group and therefore make it a member of the security policy.
⚠️ There are different conditions for making Virtual Machines members of a group but tagging is the one that is mostly used.
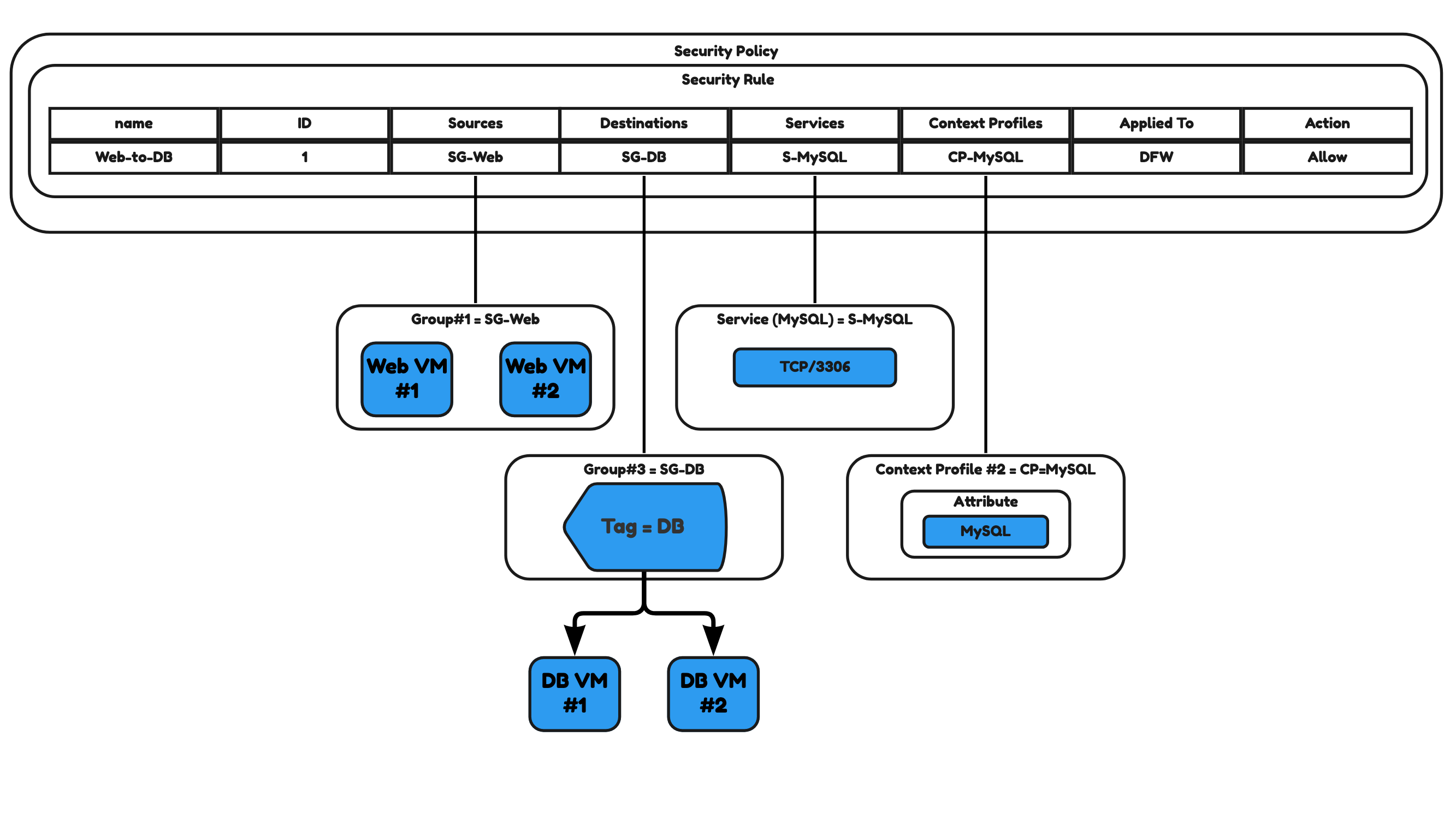
Use Groups, Services, Context Profiles, Layer7 Access Profiles, and Attribute Types to be part of a Security Policy
In Figure 35 you see what you get when you put everything together. When you create a Security Policy (Gateway or Distributed) you can create Security Rules. These Security Rules will typically always contain a Source and Destination. In this example, I have created two groups, SG-Web and SG-DB. SG-Web (Source) will group all my Web Servers and SG-DB (Destination) will group all my Database Servers.
I am also combining the MySQL Service (S-MySQL) that looks for TCP port 3306 with a MySQL Context Profile with the MySQL App ID Attribute).
Figure 35: